It is not possible for a week to pass without a vulnerability being discovered. However, it is necessary that this vulnerability and all the information associated with it be available in an accessible, orderly and reliable format. Next, we are going to explain everything about the most important vulnerability databases. An important aspect is that the different IT security management solutions use these databases to support us in mitigating the risks of potential cyberattacks.
CVE (Common Vulnerabilities and Exposures)
It is one of the most reliable sources when it comes to identifying, analyzing and certifying a vulnerability found. Each of the vulnerabilities present in this database has a CVE number. The latter is provided by a group of specialized authorities from the CVE working group.

But why would a vulnerability have an identifier number? This allows the management of information regarding it to be much more reliable, avoiding ambiguities or erroneous data that damage the information regarding the vulnerability in question.
This same number allows it to be easily identified and evaluated by the different security tools such as SIEM, which are the Information Management Systems and Security Events, so that they can facilitate the implementation of actions to mitigate risks.

Since its founding in 1999, CVE has become a standard when it comes to making any vulnerability public. As we have mentioned, the different security tools implemented, especially in business networks, people specialized in computer security, and even the general public, manage to communicate more fluidly. The latter, regarding what constitutes a certain vulnerability and its impacts.
We are sure that at some point, you will have read some news, publication or tweet regarding one or more vulnerabilities. In many cases, they refer to the CVE number as a form of safe and reliable backup regarding the information presented. We suggest following the CVE’s own Twitter account to be aware of everything that is known regarding the latest vulnerabilities.
CERT Vulnerability Database
Another database that this time corresponds to the prestigious CERT ( Computer Emergency Response Team ). It provides information regarding any software vulnerability. The data included are technical details, possible remedies, and which manufacturers are affected. Several of the records found are the result of the efforts of individuals. Also, people who work outside government institutions in order to make the information found available to all.
Consequently, several of the records could give the impression that there is a lack of depth regarding one or more data. That is why the CERT itself recommends referring to databases of government institutions such as the NVD , which we will talk about below.
NVD (National Vulnerability Database)
As we recently discussed, this database is linked to a government institution. It is the NIST , which is the National Institute of Standards and Technology. It is an extensive repository that houses data regarding vulnerabilities that have been managed through the SCAP protocol. Its acronym stands for Security Content Automation Protocol .
The direct advantage of this data is that it makes it much easier to automate repetitive tasks of vulnerability management, security indicator measurement and compliance. In addition, you can find everything related to security flaws found in all types of software. Also, you will know about errors in the configuration, the name of the affected manufacturer and the potential impacts of the vulnerability or bug found.
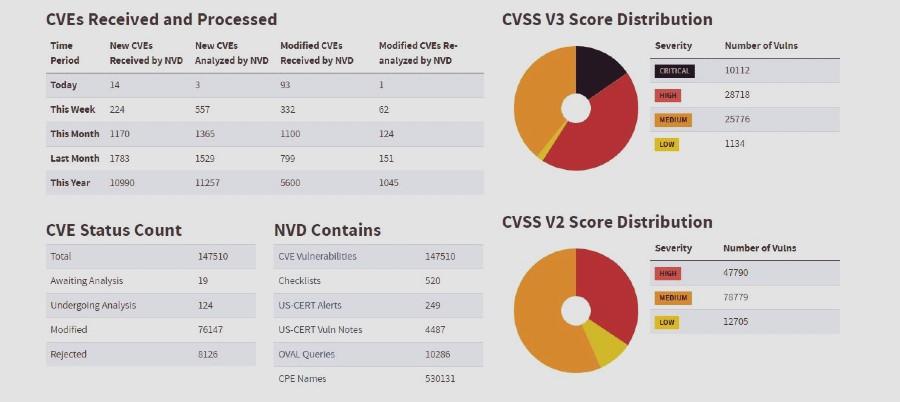
A very important detail is that when entering the statistics panel, we will find the vulnerabilities listed with the CVE classification, which corresponds to the first database that we have cited. This means that practically every vulnerability cited in CVE has an extra backup from the national database. Despite the fact that this is an institution that depends on the United States government, it is one of the most consulted sources to be aware of the latest vulnerabilities.
On the other hand, said panel shows a couple of graphics based on CVSS . These acronyms stand for Common Vulnerability Scoring System . This is an open standard that is used to measure the severity of each of the vulnerabilities found. Basically, there are four possibilities or levels: low, medium, high and critical. It is concluded that a vulnerability has a certain level based on a series of metrics. The standard, as well as all the databases that we have mentioned, is freely accessible and free for anyone interested.
The importance of vulnerability databases
In this article we have recommended the main tools to manage the security of your network. The most important are those that have the Incident Response approach, that is, incident response. However, how do they do it? What data do they handle so that they can tell you that one or more security flaws have been found in your network or some vulnerability in software?
Precisely, the databases that we have mentioned and others are the main contributors to security management solutions. Before there were standards such as CVE and CVSS, the different solutions had their own databases and with a great disparity of criteria when naming them, classifying their criticality and other aspects. This context of vulnerabilities once again highlights the importance of standards in virtually everything we do.