The times we are in require that our systems and networks have a robust and resistant protective shield. What does this mean? That they must be protected against the multiple security threats that we can find on a daily basis. Known vulnerabilities, zero-day , data breaches, and more. It is not necessary to have a system or a network that thousands of people depend on to operate, those that are medium or small are also affected, mainly because they are the majority.
Consequently, we must opt for solutions such as security incident response management tools, or also known as Incident Response Tools in English. Today in this article we are going to introduce you to several of them to correctly manage security incidents.
Is a Security Incident Tool Really Worth It? As we have discussed, it helps to ensure the integrity of systems and networks. Through these tools, systems and networks will be protected from various security threats and risks. However, the most important thing is that it supports obtaining solutions to the various Security Incidents that may arise.

These types of tools are complemented by antivirus-antimalware solutions and firewalls to analyze and alert on potential events that threaten the security of systems and networks. Therefore, there are some tools that also help mitigate the consequences of these dangerous events, if they do occur.
These tools provide responses to Security Incidents by collecting information . What are the fonts used? They can be logs, network endpoint information, authentication history, and more. In other words, any record that can be obtained of the activity on the network helps these tools to fulfill their functions. We can even find tools that help prevent potential Security Incidents based on the most recent exploits discovered or on zero-day vulnerabilities .
Do I really need Security Incident tools?
If you are currently not sure about its implementation, time will take care of saying yes . They help a lot with the tasks of monitoring, identification and resolution of security incidents that may arise. We must bear in mind that, according to the size of the system or the network, these tasks can become very repetitive and become subject to multiple errors. Of course, these also consume a lot of productive time during the day.
In the field of computer security, these types of errors in many cases, leads to the loss of the integrity of systems and networks. Consequently, we can say that Incident Response tools contribute to the automation of these tasks. Thus, computer security specialists can focus their efforts on implementing solutions to identified incidents.
Recommendations of tools to manage Security Incidents
It is possible to find both free and paid tools. As for the paid ones, some are cheaper than others, according to the number of functionalities it offers and the provider’s support model. However, if the financial resources are a limit, or you want to use it for other purposes, we will also recommend some tools that do not require a subscription and you can use them for as long as you want.
Sumo Logic
It is a platform that has the ability to function independently, or integrating with other SIEM tools. Remember that a SIEM stands for Security Information and Event Management , which also helps us in the management of different security incidents that may arise. Therefore, it can also be integrated with work environments that are in the cloud or those that are hybrid.
The latter, above all, is something that occurs frequently because the migration of all applications and services to the cloud can be either very expensive, or simply not what the organization needs. Sumo Logic uses machine learning to greatly improve the quality of detecting security incidents, reaching the level of detecting them in real time.
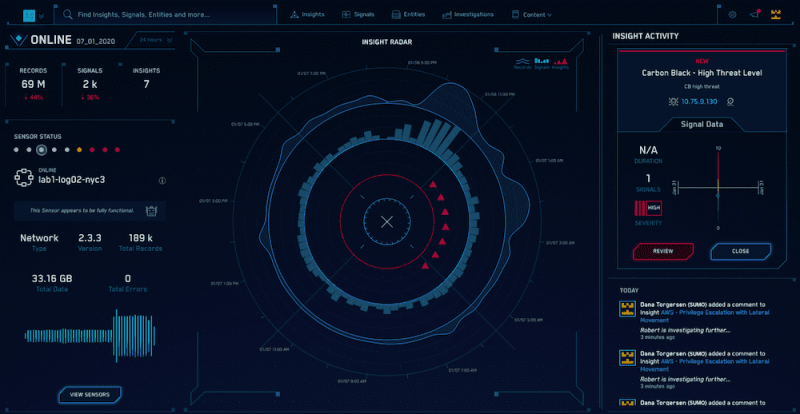
Those IT teams that need full visibility into these incidents can use this tool. With ease, it helps to strengthen the tasks of analyzing security incidents, managing generated logs, monitoring compliance with standards (PCI-DSS, HIPAA, etc.) and much more. Sumo Logic’s ability to automate these tasks saves both time and technological and human resources for effective incident management.
Although it is presented as a simple tool to implement in the different systems and networks, to scale and update the software if necessary, it is a fairly inexpensive solution. Many of these tools are known to be very promising, but inaccessible.
If you wish, you can start with a free trial that will be ready to use in minutes. The main condition is to have a corporate email and to take this into account, you will not need to register a credit card. In the event that you opt for any of the plans with cost, you will come across much cheaper options in relation to other available solutions.
Manage Engine
If you need to focus your Security Incident response management on auditing and compliance, this solution will be useful. Manage Engine enables effective management of generated logs, audit processes and IT-focused compliance. Devices that are part of networks such as routers, switches, firewalls and those that are oriented to IDS / IPS generate a high volume of data through logs, as well as servers, applications, databases and web servers. Analyzing them manually means a great waste of time, as well as possible human errors and, therefore, increases the risks of cyber attacks.
Let’s highlight some of the features it has. As we have commented, one of the focuses of this solution is auditing . Part of the focus of these audit processes has to do with the devices that are connected to the network. What is possible to detect? Changes in policies and security rules firewalls, logon logs including those who have failed and any traffic log input or output that may be suspicious.
All this information is presented through reports in a format suitable and understandable to all. Also, it is possible to configure alerts that will warn you about irregular events in the network. To make this much easier, Manage Engine has pre-designed templates for alerts.
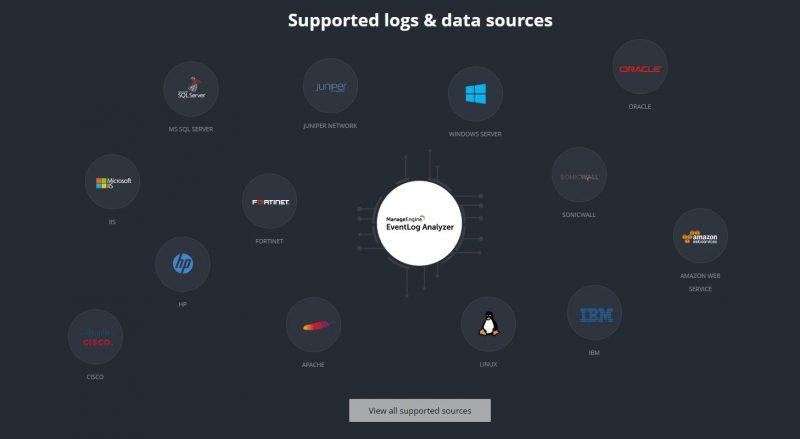
As we can see, this solution is compatible with many other connectivity, network and database solutions such as Windows Server, Oracle, Juniper, Cisco, Amazon and others.
Threat Intelligence . This area of computer security is known in English as Threat Intelligence . Once you have installed this solution and without prior configuration, you will be able to detect security threats by detecting suspicious IP addresses. A comprehensive database of IP threats supports this functionality. On the other hand, it is possible to detect URLs of suspicious sites and domains that interact with the network, and it can also do all this in real time.
You can access a limited free version or request a quote if you opt for the plan via subscription.
The Hive Project
The particularity of this security incident management platform is its collaborative nature. The related tasks are created and distributed among the members of the computer security team. On the other hand, it is possible to manage alerts from other tools that your system or network already uses, such as SIEMs. Simply import the data into The Hive’s platform and carry out the investigations.
With this solution, in addition to automating repetitive tasks, it is possible to take them to the next level, thanks to the possibility of adding metrics, custom fields to the different pre-designed work templates . In this way, the analyzes and reports generated regarding Security Incidents report relevant events. The graphical interface of the generated reports is dynamic and you can even add labels to highlight some points.
If your network is a victim of frequent receipt of emails with suspicious attachments, they can be imported into The Hive for analysis without exposing us to the danger of opening them.
Do you or your team have knowledge of Python? The Hive puts at your disposal an API called TheHive4py . This API allows you to create work cases for the platform from sources such as email clients and SIEM. The platform itself proposes a practical case: a given Security Operations Center needs reports regarding email activity and this has to be sent to a specific address. Every time that address receives that report, a script from TheHive4py collects that data, calls the aforementioned API and this is responsible for sending alerts to the platform. In turn, specialists can analyze these alerts and import them as work cases.
On GitHub we can find everything you need to start using The Hive and its corresponding documentation . Completely free!
Cyphon
There are situations in which the data we need to analyze to effectively identify security incidents come in raw format, that is, raw. Processing them takes a long time and Cyphon can automate these tasks according to the needs of the Computer Security team. You can also generate alerts, generate criticality ratings of incidents and track the work done by each member of the team.
Is it necessary to escalate an incident? This tool allows you to do it and once the person in charge has resolved the problem, alerts are generated to communicate the results. This functionality is especially useful if there is a team dedicated to Computer Security and, in turn, there is a distribution of tasks and responsibilities. It is like a team that provides Internet service support, with its corresponding levels (1,2,3, etc.).
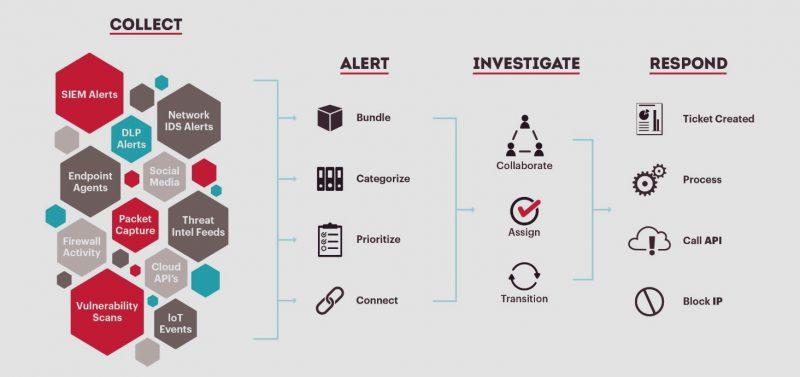
Above, we see the outline of this solution. From data collection from sources such as SIEM alerts, packet capture, vulnerability scans to incident response thanks to resolution through ticket creation, IP address blocking and more. Today, more than ever, we need tools that not only allow us to carry out the act of incident management, but also that facilitate it. You can enter the official Cyphon website from here.
We are sure that one or more of these tools will be useful to help protect your system or network. Try one of these tools right now!