
OWASP ZAP (Zed Attack Proxy) is the most widely used vulnerability web scanner in the world, it is completely free and open source, therefore, you can adapt it to your needs. This program is actively maintained by an international community of volunteers, who work to improve the tool little by little and also incorporate new features. Today in this article we are going to teach you everything you need to check the security of your website to avoid vulnerabilities that put your server and your data at risk.
OWASP ZAP Main Features
The first thing we must indicate is that OWASP ZAP is not a commercial tool, it is completely free and open source, in addition, it is a multiplatform tool, being compatible with Windows operating systems (32 and 64 bits), Linux, MacOS, and even We can download a Docker container that will incorporate everything necessary to run it correctly. This program is very easy to install, we will only need to have Java installed on our computer to be able to run it, other characteristics are that this tool is translated into more than 12 languages, including Spanish, in addition, thanks to the community we have a lot of documentation, help tutorials and we also have forums where we can put our problem and help us solve it.
Users of this security forensic tool will be able to audit different web applications with a series of specific functions and analyzes. We will be able to check all the requests and responses between the client and the server, setting up a proxy that will be in charge of capturing all the requests for further study. We can also locate resources on a server, perform automatic analysis, passive analysis, the possibility of launching several attacks at the same time, and even use dynamic SSL certificates. Other interesting features are that it allows the use of smart cards such as the DNIe, and even personal certificates, it is also capable of working with authentication systems and we have a store of extensions (plugins) to further increase the functionalities of this great tool.
ZAP is currently in its version 2.10, and they have been incorporating a large number of new functionalities, such as new attack modes to search for vulnerabilities, improvements in the injection system to attack several servers simultaneously, policy systems to choose different rules that will form part of the analysis, scan dialogs with advanced options, new access control plugins and scan sequence to perfectly configure how we want the attack and vulnerability verification to be carried out and much more.
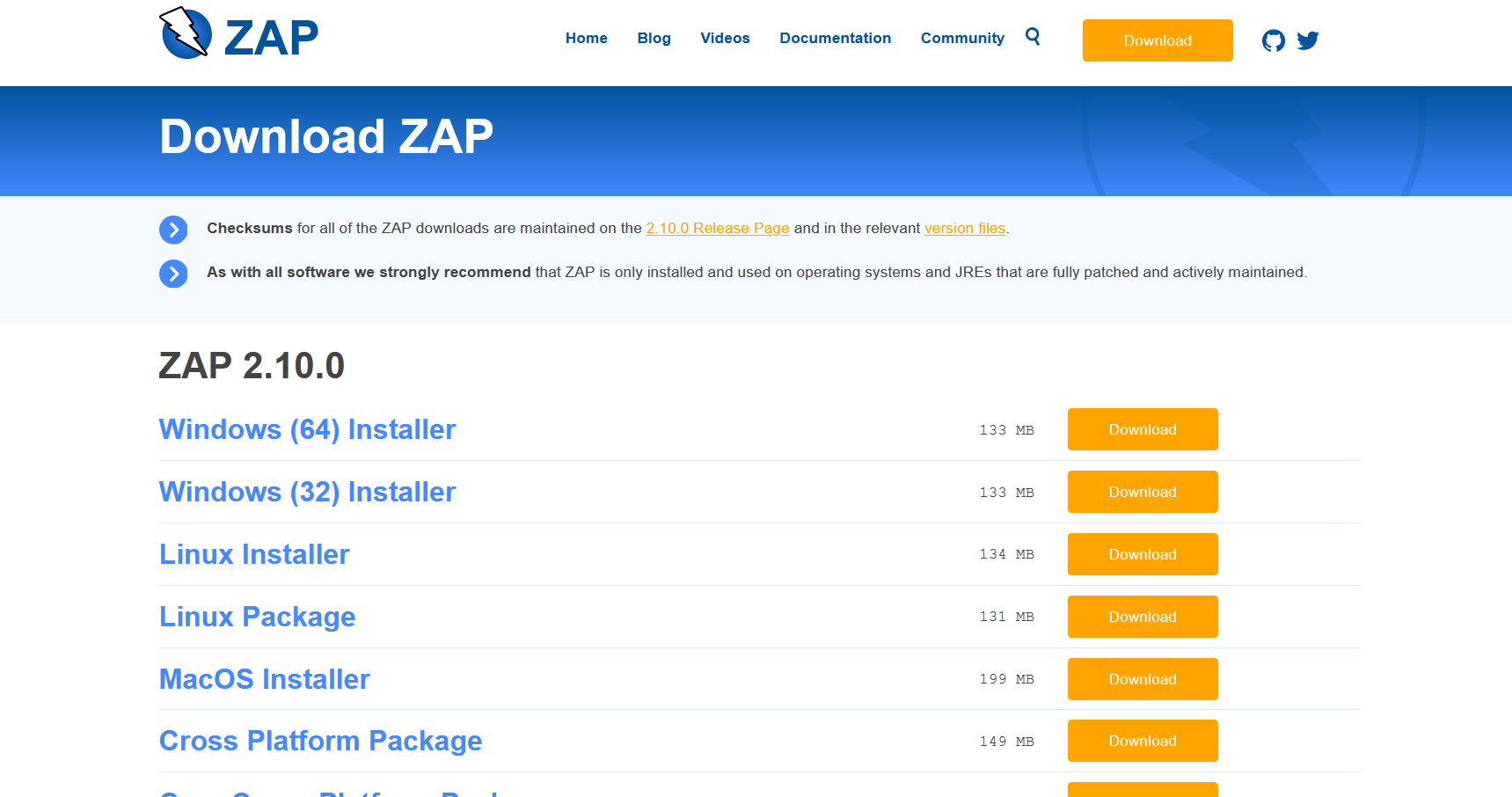
On the OWASP ZAP official website you can find the links to download it, both for Windows, Linux and macOS as well as the Docker containers that already include everything necessary for its correct operation.
Installation and commissioning
The installation of this program is really simple, we will simply have to follow the installation wizard, choose if we want the standard or custom installation, then we can choose the directory where to install the entire program and then run it.
We can also choose to create a folder in the start menu, create icons on the desktop and even quick access. Finally, OWASP ZAP will allow us to check for updates, both for the ZAP itself and also for the add-ons that we can install. In addition, we can also install the new rules that are created for web scanners etc.
Once installed, we can run it to start scanning web servers and check for any known security flaws.
Check the vulnerabilities of your web server
The first thing we have to do is run this program, it will take a few seconds to load correctly.
Once started, we can configure the ZAP session to later save the entire project and the data that we have taken with the security audit to the web server. We will have a total of three options, although the Spanish translation is not very well done, it is quite well understood.
In the main menu we will have the possibility to carry out an automated scan, or a manual scan if we have previously defined what we want. We can also directly access the help of the tool.
If we click on “Automated Scan” we can perform an automated scan to the URL that we want, we can put any URL to attack, either with an IP address or domain, a very important detail, is that we will have to have permission to perform this type audit, and do it carefully because web attack alerts could jump in the IDS / IPS that we have configured, and also in the mod_security of our Apache server etc.
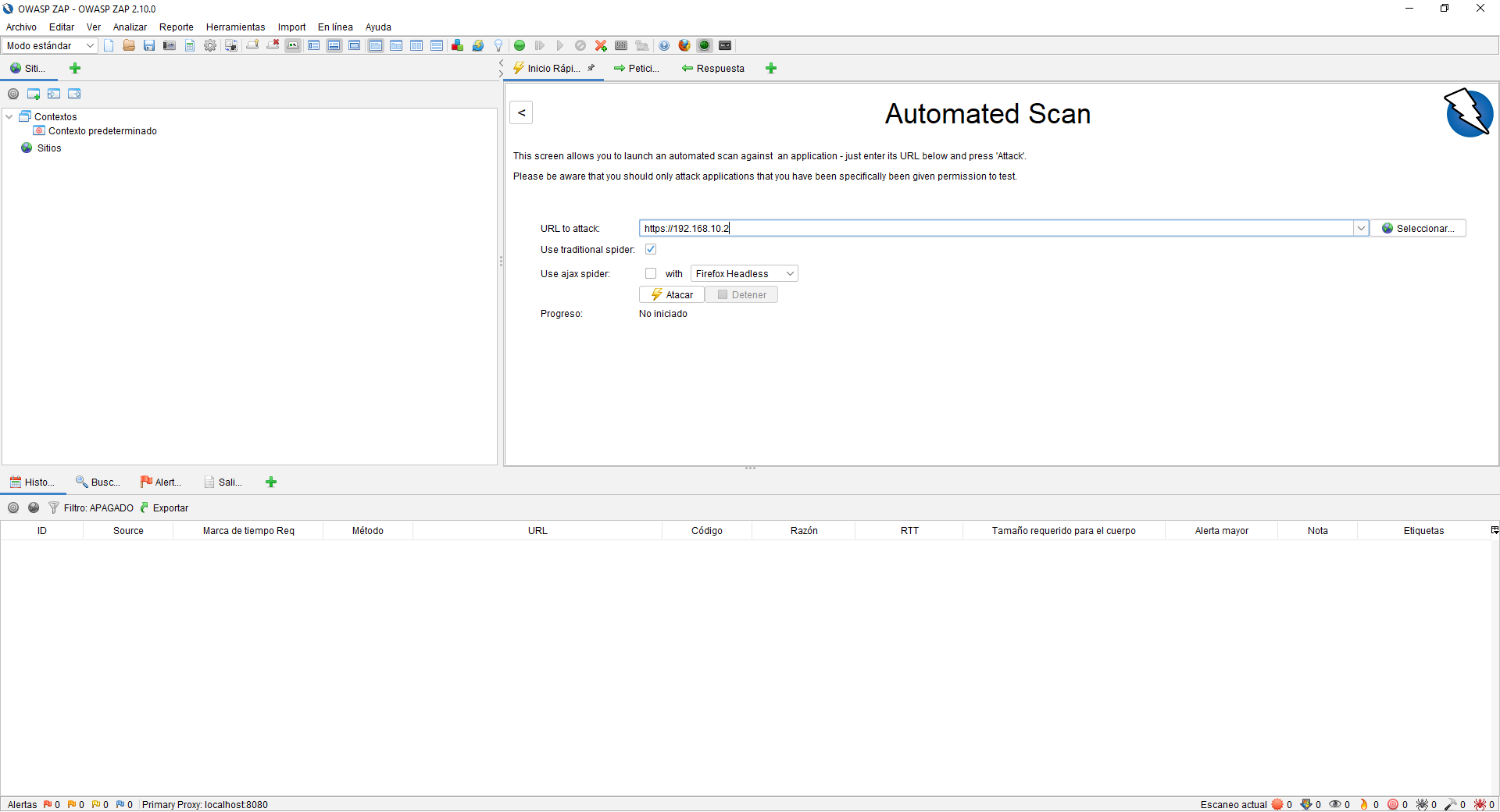
We will have the possibility of using a traditional or Ajax spider, in addition, we will be able to make use of the profiles of Chrome, Firefox among others. Once we have configured everything, we click on “Attack” and it will begin to scan the entire web server making GET and POST requests to detect possible vulnerabilities in the application.
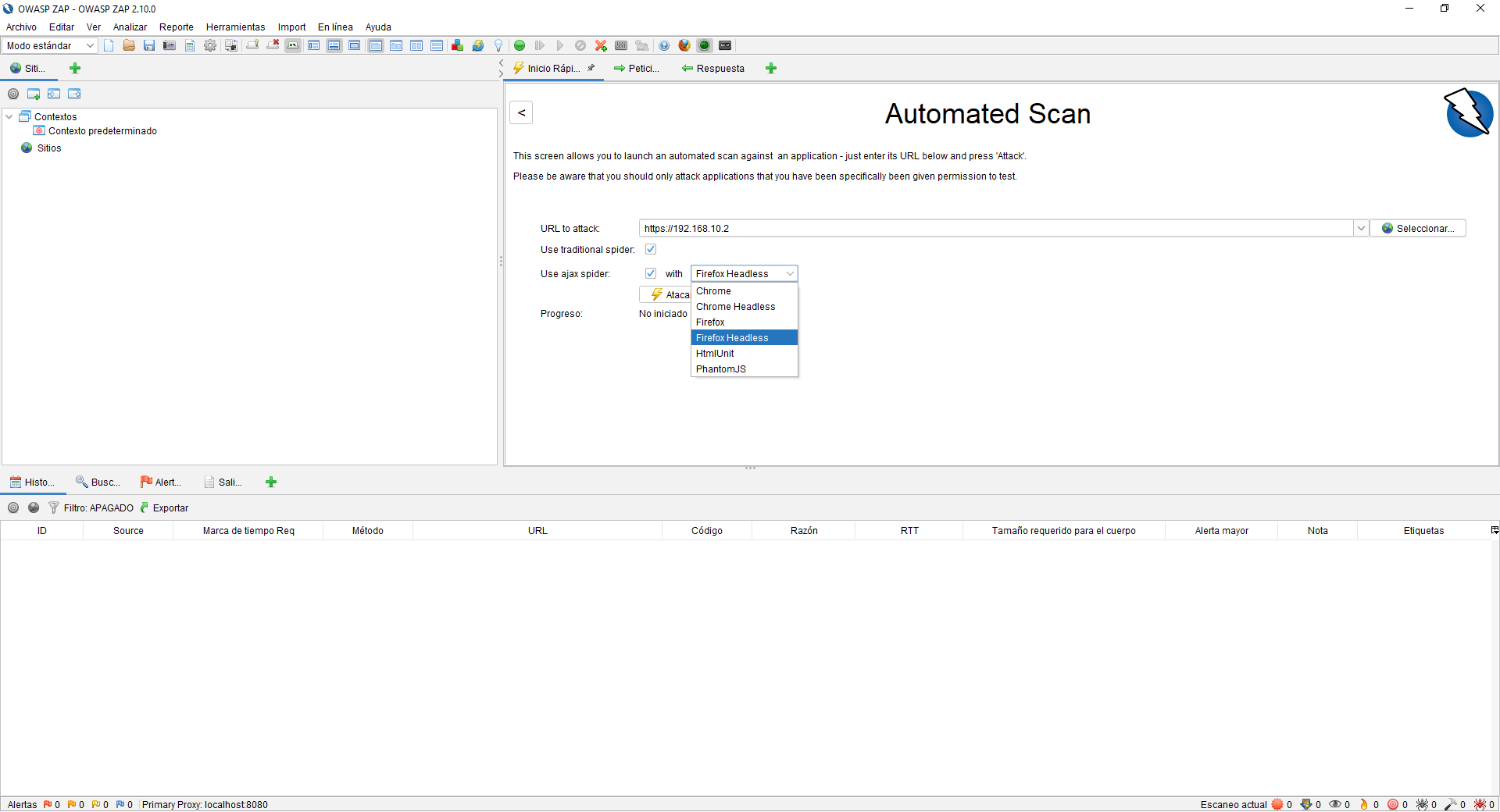
At any time we can stop this attack and check everything you have analyzed. At the bottom is where we can see all the information. We will have the possibility to see the history of attacks carried out to check security, and we can even attack it again and many other advanced options.
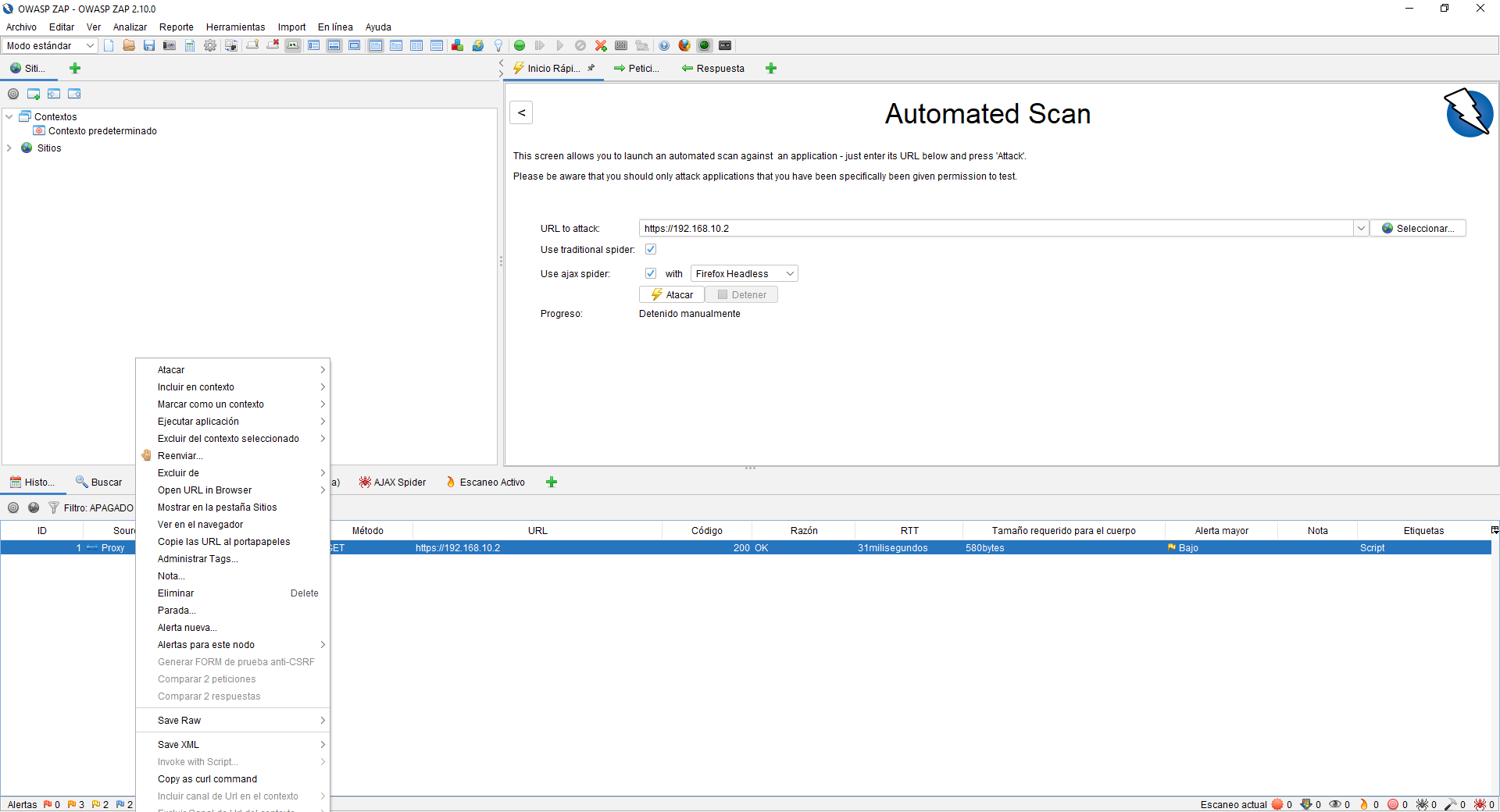
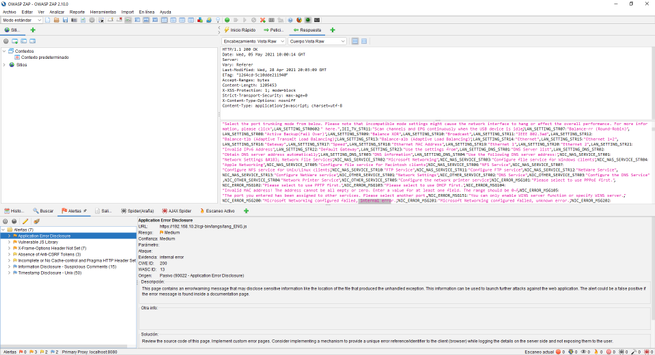
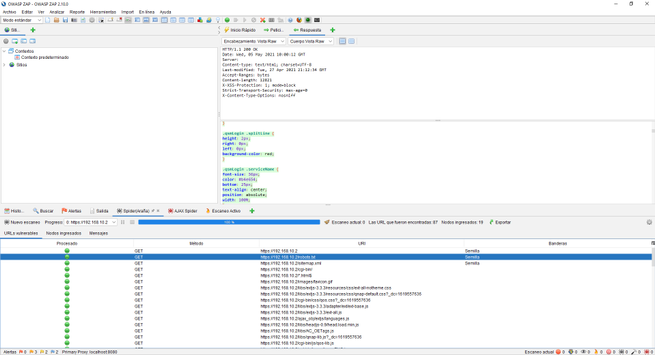
In our case, we have attacked the web server of a QNAP NAS server updated to the latest version. We will be able to see many GET and POST requests from the HTTP / HTTPS service itself. In the lower left part we will see all the alerts we have, by clicking on each of them we can see in the right part what type of vulnerability or error we have located, and in the upper part we will see everything raw.
Depending on what we open in the alerts, we will see one information or another, it would be advisable to review all these alerts that OWASP ZAP gives us to verify that everything is correct and there are no security flaws.
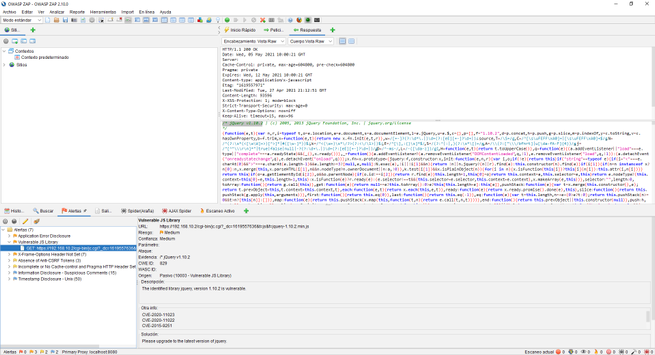
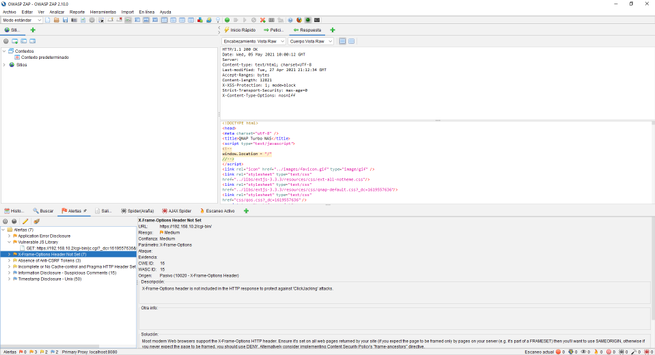
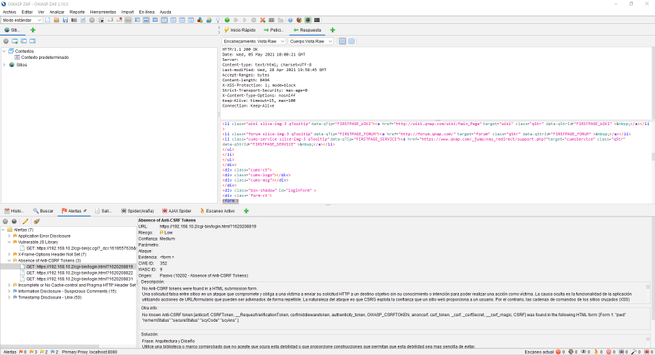
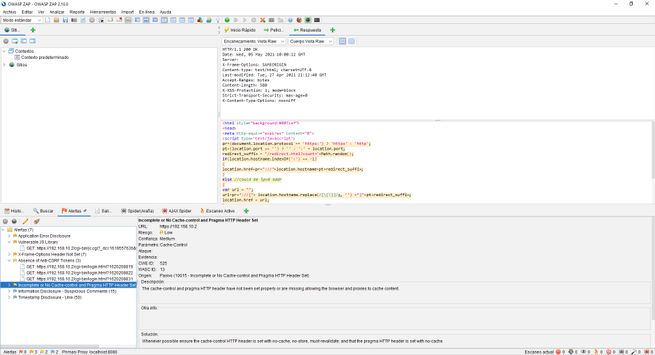
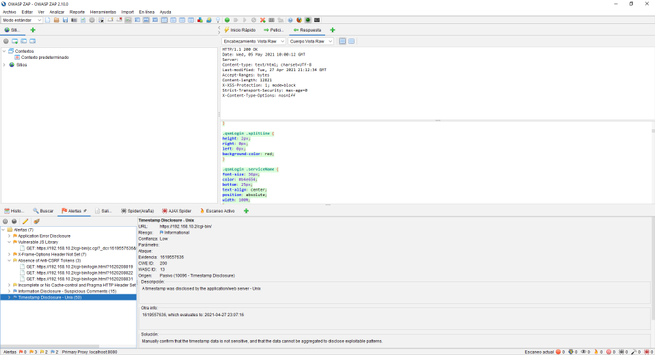
The spider has also done its work with this web server, making requests against the web server to try to show us all the files that exist in it, we can also see the files that do not exist or are out of reach.
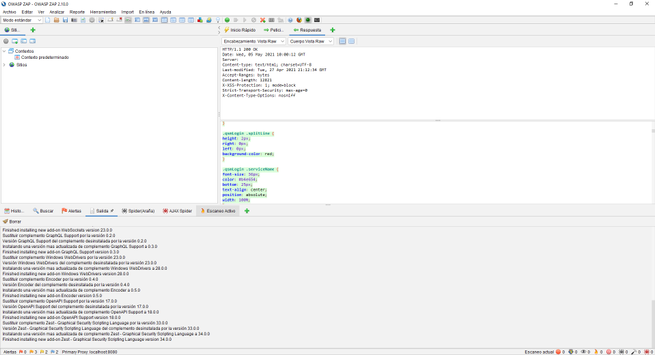
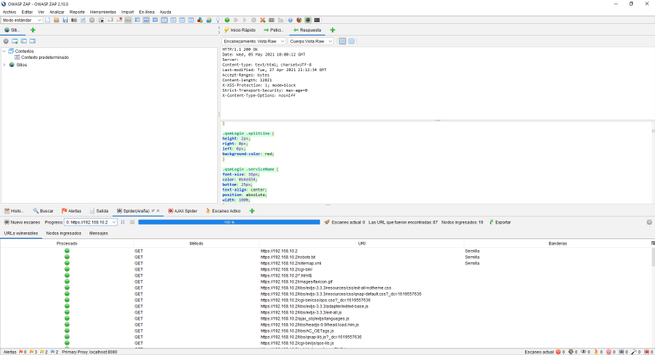
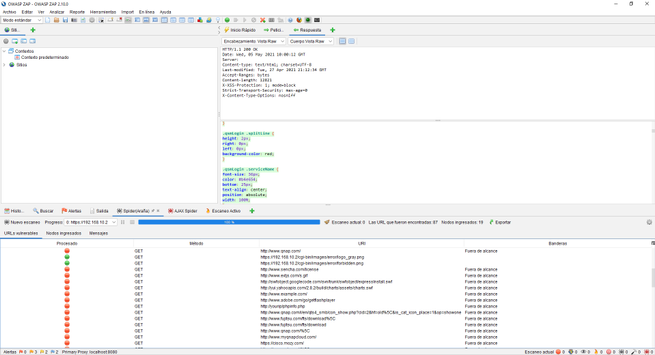
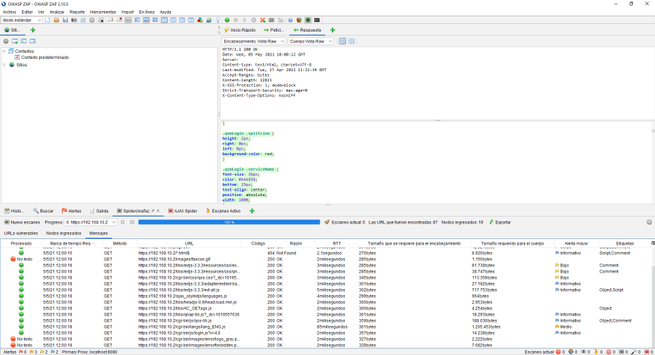
On the next screen you can see the CSS code of the web server, as you can see, we will find all the information necessary to evaluate the security of our web application, and if we have denied access to different parts.
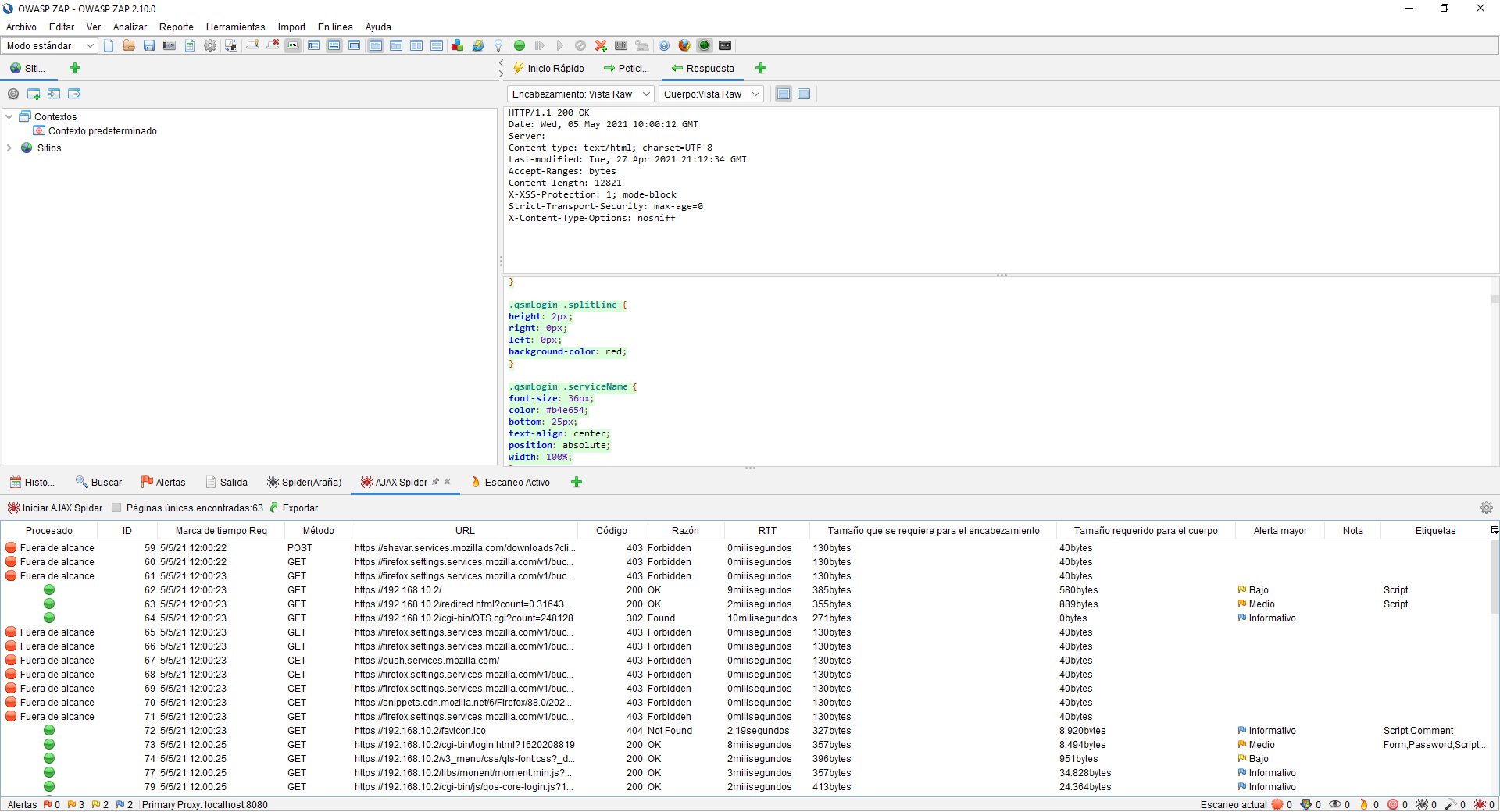
If we click on «Sent Messages» we will be able to see all the POST that we have made, with the received code, RTT and a lot of other related information.
In the upper area of the program we can see the different “File”, “Edit”, “View”, “Analyze”, “Report”, “Tools”, “Import”, “Online” and “Help” menus. This program is really advanced and will allow us great configurability.
In the case of QNAP, when it detects that someone tries to make a failed login several times, it will automatically put us on the blacklist, therefore, we must take into account the protections of a web server, either by the L7 firewall that we have configured, the IDS / IPS that will detect anomalous traffic etc.
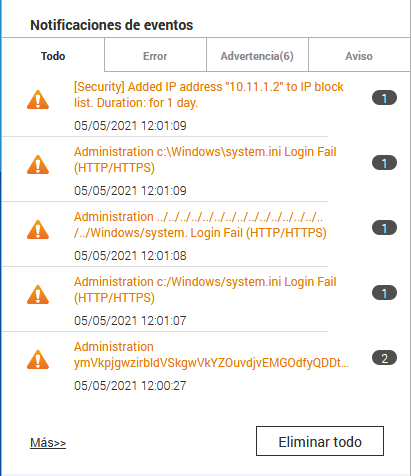
As you have seen, OWASP ZAP is a very advanced tool to check the security of our server and web application, it is essential that, when we develop a web application, we carry out a security audit to verify that everything is correct and there is no fault in security that could be exploited.