Working from home has become the norm in many organizations in recent times, however, when working, we must be sure that we will be able to access the resources of our organization safely and whenever we need them. Today in this article we will talk about secure remote access tools , what they are for and what are some of the tools that we could try. If you are an IT administrator in an organization, you will certainly take advantage of this guide.
More than ever, the offer of services such as VPN or security at the endpoint level is extremely wide. In any case, we must pay special attention to what benefits each one really has to make the best decision. It doesn’t do much good to spend a lot of money on a ‘very prestigious’ and expensive business solution, if, after all, we can’t make the most of everything it could offer. Most likely, you do not need to purchase any licenses or services, as there are currently free software to do this.

We can find payment options with free access for a limited time, only those that are paid, and also, those that are free permanently.
Akamai
This is one of the best known companies in the world of web development. It is especially characterized by its CDN solutions. However, in this guide we mention it for its Secure Remote Access and Universal Threat Protection solutions.
Speaking specifically of the remote access solution, this solution is based on the emerging Zero-Trust model. Remember that one of the main advantages of it is that it is possible to configure user access only to the resources it needs. So it is possible to have a more detailed control of the permissions of each one. It will no longer be necessary for everyone to have access to the entire internal network!

An advantage of Akamai is that it has the ability to easily integrate with multiple solutions that your network already has in place. Some of the tools are Windows Active Directory, CDN solutions, proxies, SIEM tools and much more. According to the organization’s own portal, once the integration has started, the following protection schemes are activated:
- Protection of the data path.
- Identity and Access Management (better known as IAM).
- Application Security.
- Multi-Factor Authentication.
- Single Sign-on.
- Management Visibility and Control.
Do you want to try these solutions? In this link , you can have direct access to try them and they will be free for 60 days . On the other hand, if your organization needs more specific advice and solutions, a contact form is at the same link.
Cloudflare for Teams
This solution will be available at no cost until September 1. According to Cloudflare itself, this initiative is a reality because many organizations are not having the best time economically, so in some way or another they must continue to operate to sustain the business. Likewise, they must have solutions that guarantee the safety of users who must continue their activities from home.
Consequently, it is possible to access the free offer until September through this link . You just have to fill out the form and pay attention to the following steps. In case you need it, you can have an introductory session on the Teams solution for 30 minutes where an expert advisor will guide you so you can start implementing it.

Now, what benefits does it offer? Basically Teams is divided into Cloudflare Access and Cloudflare Gateway . The first is aimed at guaranteeing safe and efficient access to the internal applications of the organization. As Akamai does, the Zero-Trust model is implemented to ensure that each user (including external people who work for the organization), access what they need. On the other hand, it is possible to have complete monitoring of each login event and requests.
On the other hand, Cloudflare Gateway offers secure access to the network avoiding situations such as latency or general slowness when using applications. In addition, you can have visibility of all traffic, so that you can detect potential data flows that could compromise the integrity of the network.
Chrome Remote Desktop
There are solutions that do not require further prior configurations. The Google Chrome solution may be what you need. What you will need is from the Chrome browser itself, in addition to a Google account. Once you have them, you can create a PIN that restricts access to your account from other computers or devices. Although it is a very quick and easy solution to implement, the benefits can be somewhat limited.

However, given the immediacy and the few requirements that a very small organization would have, this may be the ideal alternative. Basically, you’ll get remote access to your organization’s computer from home from any device that has Chrome and your Google account on it. On the other hand, Remote Desktop can be used for remote assistance. There are situations where you may have a problem and the IT representative must have access to your computer.
Without further ado, you can enter this link to quickly implement this remote access service. In a few minutes, both remote access and remote assistance will be implemented on your network.
Windows Remote Desktop
This is a feature that is already included in the Windows operating system itself, so it will not be necessary to make any additional payment in the event that you opt for this alternative. Nor will you need to make any additional download. It is quite simple to use and for a direct need to have remote access to another Windows computer, it is all you need.
First, you must enter Control Panel> Systems and Security> System and select the Remote Access Configuration section
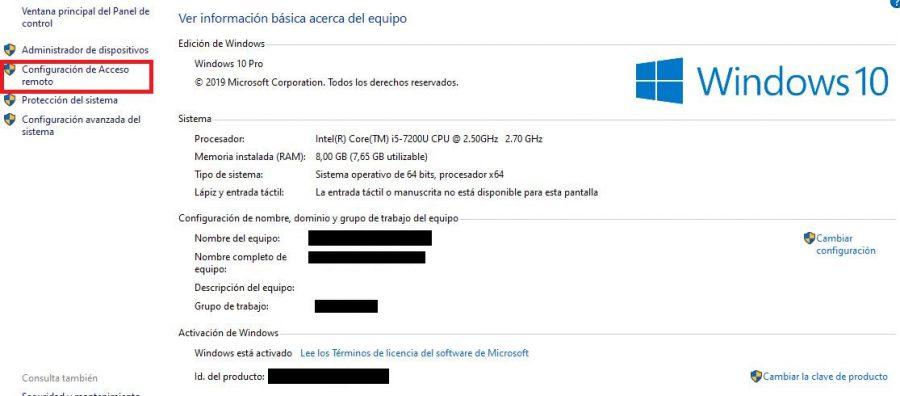
A floating window will appear and you should go to the Remote tab. In it, enable the option Allow remote connections to this computer . By default, the option to only allow connections from computers that have a remote desktop with network-level authentication will also be enabled.
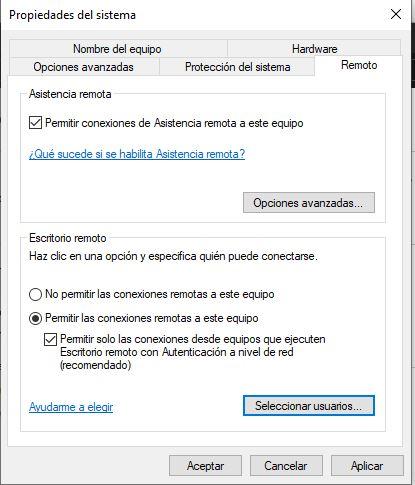
Also, you can create a list of users who can have remote access to your computer. However, anyone within the Windows workgroup who has administrator permissions will be able to have remote access, even if they are not on that list.
BlackBerry Desktop
Yes, the company is still operational. At one time, this company was the leader in mobile business devices. Those times have passed and nowadays, it is mainly dedicated to business-oriented software. On this occasion, it offers a solution aimed especially at those companies that apply the BYOD (Bring Your Own Device) model . The latter means “bring your own device.” This model talks about the act of using a computer or personal device to carry out work activities. BlackBerry Desktop allows users to have secure access to applications such as the email client, corporate sites, servers and general content.
This service is compatible with devices that have the Windows or macOS operating system. The interesting thing about solutions like this is that it can be applied to both the organization’s internal collaborators, as well as external ones, and also suppliers. This solution can be integrated with existing work environments such as the popular Microsoft Office 365. There will be no need for connectivity through VPN, extra hardware, certificates or authentication processes or additional logins.
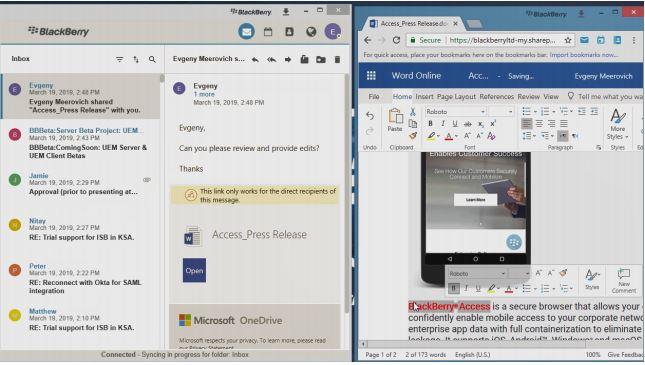
With an emphasis on integration with Microsoft, this solution highlights the fact that it will be very easy to collaboratively edit documents that are created through Office 365 . Users will be able to perform their frequent tasks with fully synchronized email, calendar and contacts. Likewise, the edition of documents such as text, presentations or spreadsheets can be done safely using a built-in editor. The environment of this BlackBerry solution ensures that data will remain secure.
AnyDesk
This is another of the solutions that are especially accessible for individual users or for those organizations with reduced requirements. You have the possibility to download two versions: one for personal use and the other for companies . AnyDesk is oriented to remote assistance. According to its official portal, it is compatible with Windows, Linux, Free BSD and macOS.
It also has its mobile versions for both Android and iOS. A great advantage is that it is not necessary to pay an additional cost for the use of such mobile versions.
One of the characteristics that is worth highlighting is that it is a fairly light application , considering the type of use it is given. In principle, you do not need to install the program with administrator permissions and you do not have to follow multiple steps for the installation. It is good to keep in mind that, in the event that you want to have remote access to your computer from your mobile, for example, you must enter a password to access with greater security.
On the other hand, if you need to record what happens during remote access to the computer, AnyDesk allows you to do it without major inconveniences. So, in posterity, you can share the recordings with those who need it. This is very useful in case you have to do a step by step of how to configure some functionality in Windows or any other program.
If you want to use this tool, you can access it permanently for free. You just have to choose the platform or operating system you use, and you will have it installed in a few minutes. However, if it is for an organization, the AnyDesk license has a cost that in general can be considered quite accessible.
TigerVNC
It is a program that uses virtual network computing (in English, Virtual Network Computing ). This is the reason for the acronym VNC. Although it is quite effective in launching remote access, its configuration settings are not among the friendliest for users with limited technical knowledge.
In case you want to use TigerVNC, you will have to do port configuration, establish a static IP in case you need it, or choose dynamic DNS. Also, have control of the different aspects of security. When you download this tool, you already have a VNC server and a VNC viewer . However, if you use a computer with macOS, you will already have the built-in VNC server by default.
Another aspect that we must take into account is that this tool does not have encryption enabled in principle. So it is necessary to install an SSH server so that you can establish remote accesses safely. You can download this alternative through this link that will take you to its repository on Github.
X2Go
We can not fail to mention open source solutions. X2Go is one of them and allows access in a very effective and quite secure way. One of the advantages is that, if you need remote access and have limitations in terms of connectivity, you can still use the application. It can be used using Windows, Linux and macOS operating systems.
As we have mentioned, it is a safe tool. This is so since traffic travels through a tunnel created using the SSH protocol. On the other hand, it is possible to share files and resources such as printers. Like TigerVNC, it has many more features that are more aimed at users with more advanced knowledge and, of course, with more specific needs in terms of remote access.
Anyway, if you are curious and like to try, you can cheer up and resort to its official portal whenever you need it. The level of detail in its documentation is quite high, so you will have a good level of support. In the same link, you can find the X2Go versions so that you can download them according to the operating system you use.
These are just some of the many options that we have at our disposal. Anyway, we are sure that you can take advantage of some of them. Even solutions like Windows Remote Desktop do not require any other download or need to make an additional payment. There are other tools that require a little more technical knowledge and this could be intimidating to some people. In any case, there is a solution for every need and it doesn’t have to be that expensive.