Last week all the alarms went off after a group of researchers published, in good faith, a vulnerability that they believed was patched in Windows 10 . Unfortunately, they were wrong about vulnerability, and basically they released a zero-day bug that allows any computer to be hacked. Luckily, Microsoft has already released the patch to fix it.
June Patch Tuesday included a patch to address a vulnerability that allowed a computer to be hacked remotely through the Print Queue . Researchers believed that it was the same bug that they had reported a few months ago, and decided to even publish the proof of concept for the bug. The problem is, that wasn’t the one patched, and they basically released the exploit for the zero-day vulnerability so that anyone could take advantage of it.

Microsoft releases patch for PrintNightmare
Last Saturday the solutions for the vulnerabilities were published, and yesterday Microsoft has released an advance patch to solve this serious vulnerability instead of waiting for the next Tuesday of July 13 , which is when the Patch Tuesday of July will be released. .
The patch, named KB5004945 for May 2020 Update and later, has already begun to be released on Windows 10 computers, and its installation is highly recommended before massive cases of attacks or hacks begin to occur.
The vulnerability has even received its own name: PrintNightmare . Microsoft has rated the patch Critical as it allows an attacker to remotely execute code with SYSTEM permissions on all Windows computers to date, as the Print Queue is present on all of them. With those privileges, they can install programs, modify data, create new administrator accounts, and basically take complete control of the PC.
Even Windows 7 has received its patch
So serious is the failure that Microsoft has released a security update for Windows 7, despite the fact that the operating system no longer has official company support since January last year. There are also patches for Windows Server 2019, Windows Server 2012 R2, Windows Server 2008, Windows 8.1, and Windows RT 8.1, and all versions of Windows 10 that are currently supported. The patch addresses vulnerabilities CVE-2021-1675 and CVE-2021-34527 .
However, the vulnerability consists of two parts, where one is remote code execution, and the other is privilege escalation, which can be exploited locally. In this case, only the remote code execution has been patched , and it is expected that for Patch Tuesday the local code execution will also be patched. This allows someone with access to a computer, or taking advantage of another local vulnerability, to take control of computers, but it is more complicated.
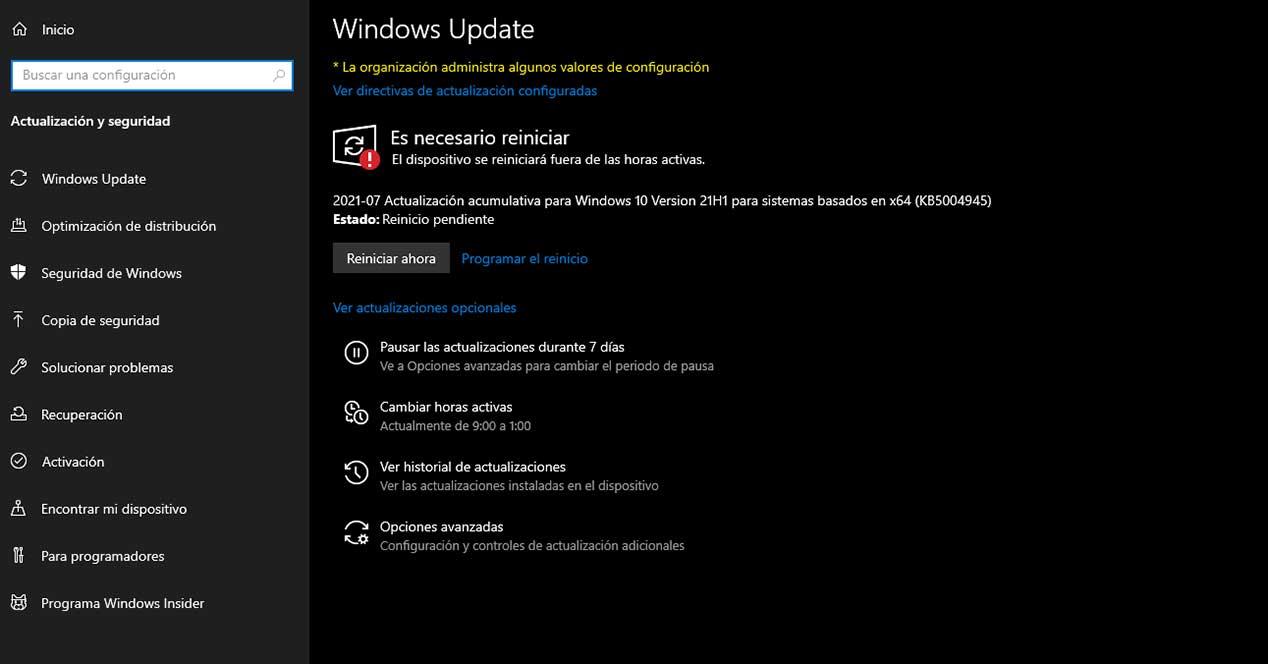
In short, we recommend that you install the patch immediately, which will probably have already been downloaded to your computers, and you just have to restart your computer for the changes to take effect. In the event that you cannot install the patch yet, disabling the Print Queue can be a good solution, although it may cause problems when printing if you use a network printer.