
As our mobiles are more and more connected, tools are needed to ensure our security. Android always boasts new security features with each new version. This means that third-party applications are increasingly at bay, and we can control the permissions and the use they make of elements such as the camera, location or connectivity at all times. It is precisely the latter, one of the best to protect, if we do not want to get a scare in our data voucher.
Background uses are the ones that can damage our privacy the most, or even drain the battery. For this reason, Android integrated a function so that apps can use certain functions, only when they are in use. However, there is an option called “Data without restriction”, which can cause some apps to bypass the restriction and consume data whenever they need it. Therefore, if we perceive that our data bonus is going too fast in a suspicious way, it is worth taking a look at this option.
Disable apps with access to Unrestricted Data
We can search for the function within the search drawer of the settings menu, since due to the different layers of customization, it is possible that it is located in different routes. The most common is to enter Settings and then Apps and notifications. Once inside we will see the option “Special access of applications” and we touch on “Data without restriction”.
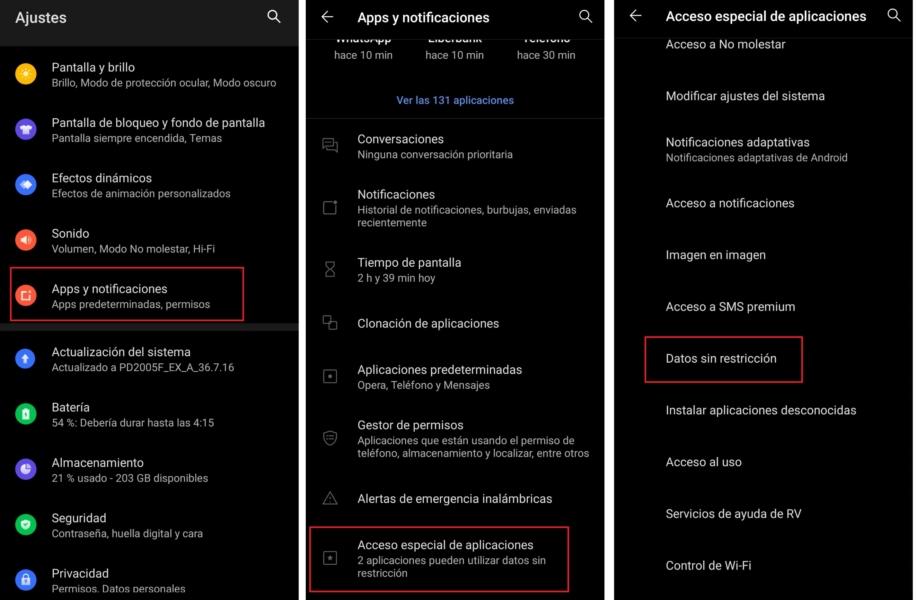
Complete list of apps
Once inside we can see the list of applications, which can use the data without restriction. This means they can ignore power saving modes, and other situations where data is disabled for other applications. If all goes well, only some system app should have this function activated. But we can choose ourselves those that we can consider essential so that they have access at all times.
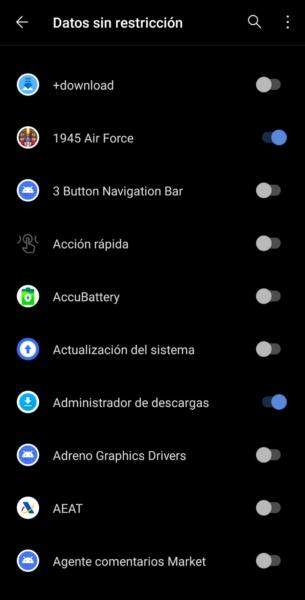
Suspicious apps
When reviewing the list, we should not see that games or other non-essential applications have access to this feature. If so, we should uncheck the box, as it could be exploited by the dreaded malware to make unwanted access and consume our data. It is also possible that we have granted this access by mistake, so it is a good idea to review the list from time to time to make sure that everything remains the same.