A new massive malicious campaign is using more than 200 typosquatting domains that pose as 27 apps and well-known brands to make you believe that you are entering their website and trick you, steal your money in cryptocurrencies or attack your Android mobile.
Typosquatting domains are those that have been registered to favor deception, since they have a name similar to that of genuine brands and, if you do not look closely, you will think that it is the original domain. Spelling mistakes are often used, putting some extra letter, changing a letter position or similar actions. The key is to deceive as many people as possible in order to attack them.

This technique is very old, but it still works on many occasions. Cybercriminals know this and take advantage of any opportunity. The possible victims are Android and Windows users . Not only do they use a domain similar to the brands they supplant, but also the malicious websites are usually clones of the originals or sites very similar to them to encourage deception.
This is how they want you to fall into their trap
These websites can be reached by entering them directly , by typing the wrong address on the mobile, but also by phishing emails and SMS, social networks, direct messages, forum posts and other ways in which hackers try to reach more victims.
Not only do they use one domain for each service, but they use multiple variants of each of these domains to try to cover as many typos as possible and thus reach more potential victims.
There are many domains looking to simulate popular app stores like Google Play, APKCombo, and APKPure . Also download portals for services and apps such as PayPal, VidMate, Snapchat, Google Wallet and Tik Tok. In total, there are 27 impersonated brands that are known so far, of which they take advantage of tricking website visitors into downloading malicious programs for their Android mobile, also for Windows.
For example, a page mimics the Play Store that downloads a malicious Android APK posing as Google Wallet when clicking Install. This is one of the many examples that we can find.
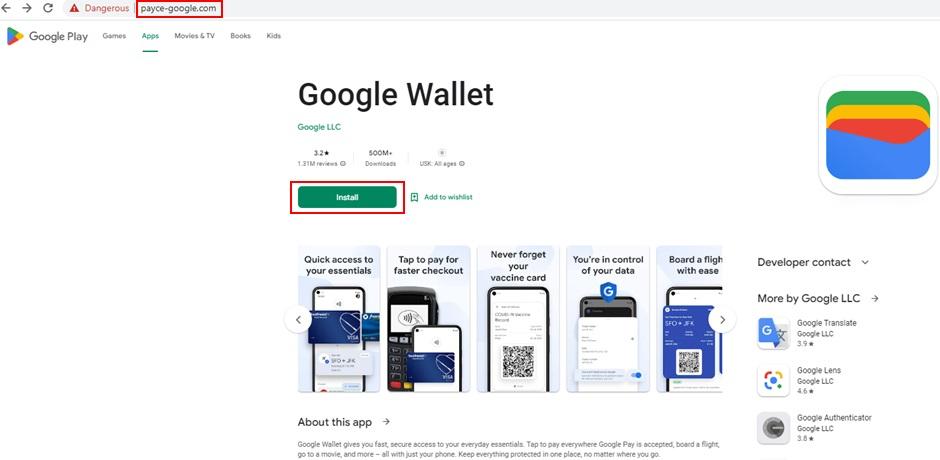
If a user falls for the deception, they will be made to download ERMAC , an Android banking Trojan targeting cryptocurrency wallets and bank accounts.
Malware can steal sensitive data like SMS messages, contacts and list of installed apps on your device. It captures the list of installed apps to steal credentials with phishing pages on the home screen of its victims.
Some of the domains detected are:
- payce-google[.]com – Impersonates Google Wallet
- snanpckat-apk[.]com – impersonates Snapchat
- vidmates-app[.]com – impersonates VidMate
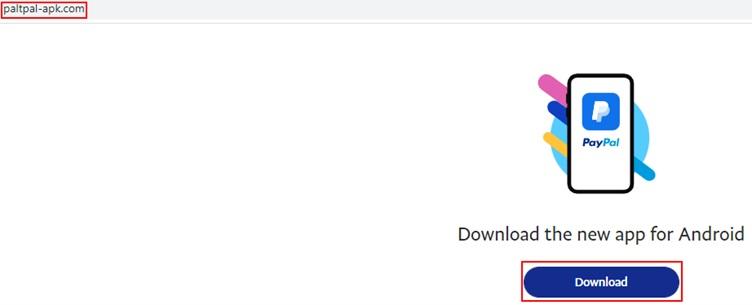
- paltpal-apk[.]com – Impersonates PayPal
- m-apkpures[.]com – impersonates APKPure
- tlktok-apk[.]link – Impersonates the TikTok download portal
Although Cyble’s report primarily focuses on Android malware, the campaign encompasses much more than that and affects Windows users as well.
Thus, it impersonates mobile services and apps , software, cryptocurrency sites, cryptocurrency and stock trading, and other websites such as the Tor browser, Ethermine, MetaMask, Figma, and others. The number of domains to use it is not negligible, at least more than 200 that are recognized.
Take extreme precautions, they are on websites
For this reason, it is best that you do not access any domain from messages on your mobile, messaging apps, social networks or Internet sites, but try to enter it by searching for it in a search engine such as Google or typing it directly, checking that there are no errors. If you are going to install an app, do it directly from the Play Store on your mobile, without websites.
If you suspect, do not open the web and, of course, do not download anything that is not strictly necessary or without checking that it is not malware. The best thing is that you have a good antivirus service on your mobile to check it.