A new Android banking malware called Revive has been discovered, which masquerades as a two-factor authentication app or 2FA and specifically attacks BBVA bank customers.
Particularly noteworthy is the fact of creating a tool that specifically attacks BBVA customers. This type of malware is quite different from other famous Android banking Trojans, such as TeaBot or SharkBot, which are capable of attacking several banks/crypto apps installed on the infected device at the same time through their modular architecture.

This is how Revive works and how it supplants BBVA
Cleafy researchers were the first to see this malware in action on June 15 and analyzed its behavior. Currently, Revive has three main capabilities in case of successful infection on Android:
- Capture everything written on the device through a keylogger module, to steal keys if they are not accessed with your fingerprint or through your mobile phone’s facial recognition technology.
- Perform phishing attacks by using cloned pages, the goal of which is to steal banking login credentials.
- Intercept all SMS received on the infected device, usually from banks and financial institutions in the PSD2 area (for example, 2FA ( Two Factor Authentication ) and OTP ( One Time Password ) authorization codes).
Revive BBVA (Photo: Cleafy)
The name Revive has been chosen since one of the features of the malware (called by cybercriminals precisely “revive”) is the restart in case the malware stops working.
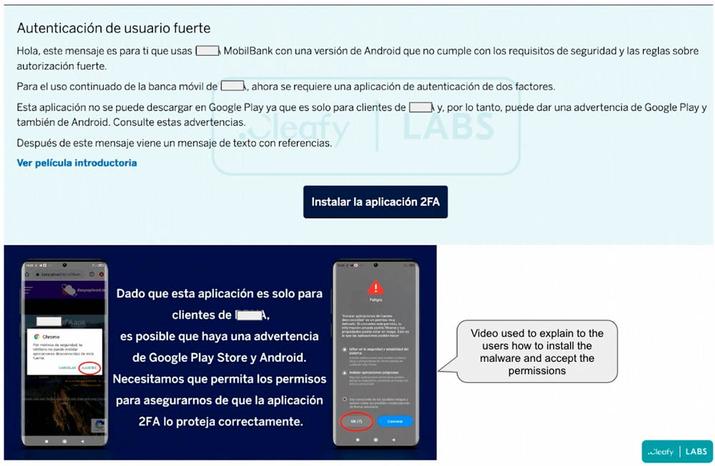
Speaking of operation, a fake video tutorial was even created impersonating BBVA in which victims were guided through the installation process with tricks such as “Since this application is only for BBVA customers, there may be a warning from Google Play Store and Android. We need you to allow the permissions to make sure the 2FA app protects you properly.”
Full control via accessibility
Once the victim downloads the malware, Revive tries to get the Accessibility Service feature via a pop-up window . This permission is used to monitor and steal information from the victim’s device.
When the user launches the app for the first time, they are prompted to grant access to SMS and phone calls , which might seem normal for a two-factor authentication app. After that, Revive continues to run in the background as a simple keylogger, logging everything the user types on the device and periodically sending it to the Command and Control (C&C or C2) server.
Doing so will send the credentials to the cybercriminals’ C2 and then load a generic landing page with links to the actual website of the target bank, to minimize the chances of detection.
Revive antivirus detections (Photo: Cleafy)
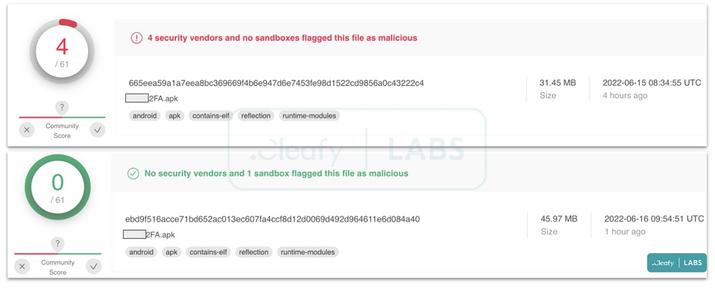
Speaking of detection, analysis of Cleafy’s tests on VirusTotal shows four detections in one sample and none in a later variant of the malware . Despite probably being based on Teradroid, the Android spyware whose code is publicly available on GitHub, the fact that Revive is so specific makes it bypass security checks.