The new Zombinder malware has arrived on Android , as discovered by cybersecurity teams who claim that this malware attaches itself to legitimate Android mobile apps to steal Google credentials from its victims.
It is important that you pay attention to everything while using your mobile because malware can ‘sneak in’ when you least expect it and steal your password that you can use to view and save your photos, manage your email, use certain services and much more. They could use it to harm you and other users in many ways.

This new malware runs a keylogger to collect the passwords you use on your phone. But that’s not the worst, they have managed to include malware in legitimate APKs by injecting viruses or payloads into the mobile while you install what appears to be a legitimate app.
This means that you could have been infected without realizing it because, when the applications you have installed work, you will not have suspicions unless you detect something strange. And you probably haven’t realized or imagined that you’ve installed an app with malware at any time.
What is this malware, Zombinder, and how does it work?
The Zombinder virus first came to light when ThreatFabric was investigating a Trojan based on the Ermac malware on computers and Android devices. The researchers discovered that the cybercriminals were using a third-party service, Zombinder, which worked like glue to bind the malware dropper’s capabilities to the legitimate app.
The modified legitimate app is downloaded from a malicious website by imitating the app’s original website, which is usually reached via malvertising. Once downloaded, the app, now linked to the malware, works as expected until an update message appears.
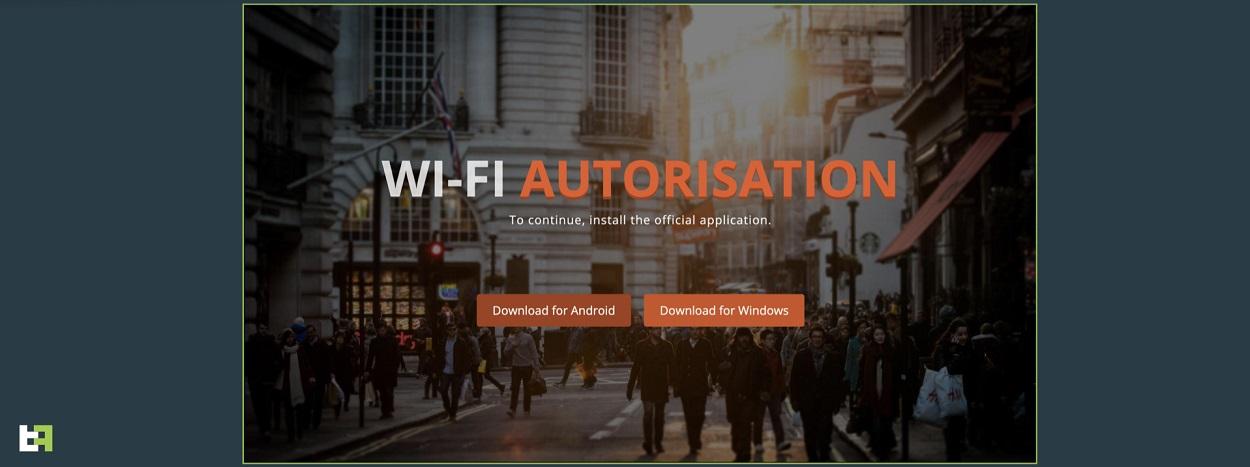
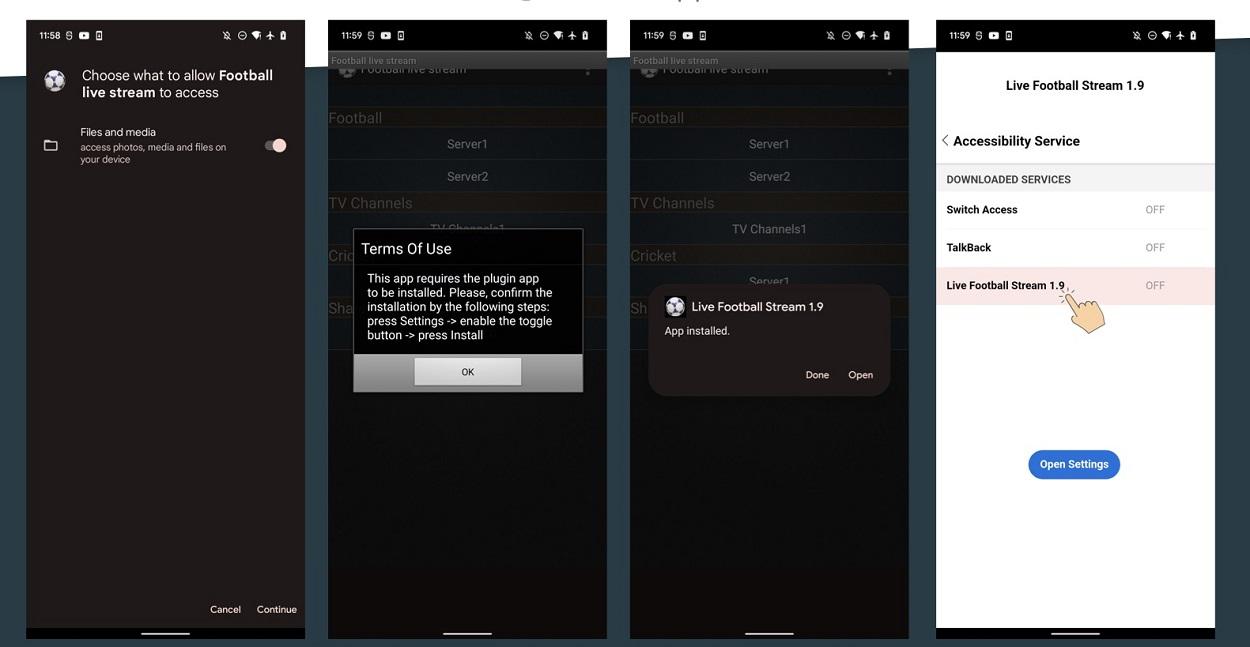
The loader is obfuscated to evade detection, so when the user starts the app, it will display a prompt to install a plugin. If the prompt is accepted, a malicious payload will be installed and run in the background. Zombinder’s service provider claims that malicious application bundles created with it are undetectable at runtime and can bypass alerts from Google Protect or antivirus.
This virus has reached Android devices and it is extremely dangerous . The problem comes when you accept the possible update of the apparently legitimate app. If you do, hackers will be able to access your Gmail messages, two-factor authentication codes, and much more. They may have information about your password and sensitive information that you type.
In which apps can we find it?
Zombinder malware currently affects banking apps in countries like Spain, among others, or apps to find WiFi hotspots , but it could reach many more apps due to its ease of installation. It has come to see a live streaming football app and even a modified version of the Instagram app. The names are the same as the legitimate apps, which makes it even more dangerous.
For example, they have discovered that a malware campaign was distributing the Xenomorph banking Trojan under the guise of the VidMate application. Some malicious apps that can simulate are Unicaja móvil, BBVA Spain, ABANCA, ING, CajaSur. Mobile Bankinter, Openbank, Banco Mediolanum Spain, EVO Mobile Bank and others. You can check out some of these apps, as the list may grow, here .
The only way to combat it is to avoid installing apps on Android outside of the Google Play Store and be wary of what may look suspicious. If you are going to do it from a website, check that it really is the original of the service, and if you do not know it, do not do it.
If you have installed any of these apps and you realize it in time, or have doubts, do not accept any message that comes from it and uninstall it immediately.