A group of researchers has found a new weather vulnerability in the Transport Layer Security (TLS) protocol . This newly discovered security flaw can allow a cybercriminal to break encryption and read confidential communications under specific conditions. Next, we are going to explain everything about this new attack on TLS with the «Racoon Attack».
Introduction to Raccoon Attack
The attack known as Raccoon Attack exploits a vulnerability of time, in the TLS specification that affects HTTPS and other services that depend on SSL and TLS, such as virtual private networks based on TLS (OpenVPN and SSL VPN).

These protocols that we just mentioned before allow everyone on the Internet to surf the web, use email, shop online and send instant messages without third parties being able to read our communication.
Raccoon Attack allows attackers, under certain conditions, to break encryption and read confidential communications. However, this vulnerability is very difficult to exploit. The reason is that in order for us to obtain results we have to rely on very precise time measurements and have a specific server configuration.
How Raccoon Attack works
Diffie-Hellman (DH) key exchange is a well-established method of exchanging keys over TLS connections. When we use Diffie-Hellman, both TLS pairs randomly generate private keys (a and b) and their public keys are calculated. These public keys are sent in TLS KeyExchange messages. Once both keys are received, both the client and the server can compute a shared key called a premaster secret. This is used to derive all TLS session keys with a specific key derivation function . The Raccoon Attack works by exploiting a TLS specification side channel; TLS 1.2 and its earlier versions. It prescribes that all leading zero bytes of the premaster secret are removed before being used in further calculations .
On the other hand, learning a byte from the previous premaster secret would not help the attacker much. However, here the attack becomes interesting since we have obtained the first results. By studying the behavior of server time, an attacker could find values that lead to a premaster secret that start with zero. Ultimately, this helps the attacker build a set of equations, and use a Hidden Number Problem (HNP) solver to calculate the original premaster secret set between the client and the server. This is an outline of how the attack works :
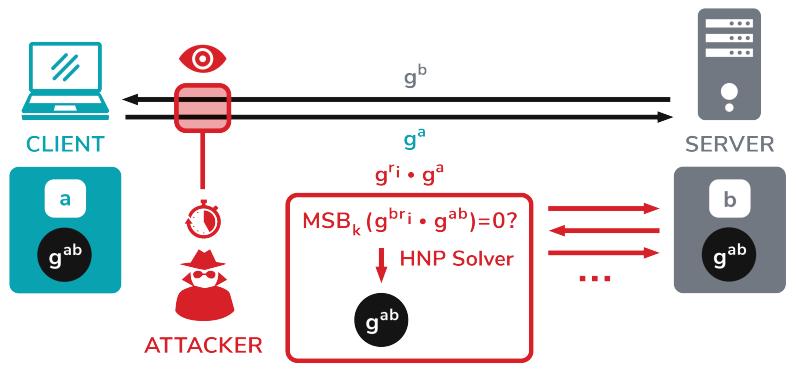
On the other hand, if you want to know the complete technical document on how Raccoon Attack works, click here .
Raccoon Attack practicality, possibilities of use and solutions
In the case of being an administrator, you will wonder if you should drop everything and fix this problem. The answer would be probably not, as many factors are required to align to successfully decrypt a TLS session in the real world. However, there are exceptions that we must consider. As for checking if our website is vulnerable we can use the Ssllabs.com tool. If your server will answer ” yes” .
Regarding those who are vulnerable, Raccoon Attack generally those who use TLS 1.2 and earlier versions. We can also clarify that the TLS 1.3 version is no longer affected. In the hypothetical case that difficult circumstances were met and an attacker could crack the connection between users and the server, he could obtain a lot of information. For example, usernames and passwords, credit card numbers, emails, instant messages, confidential documents, and more.
Companies have responded quickly to address this vulnerability. F5 named the issue CVE-2020-5929. Additionally, various F5 products allow a special version of the attack to be executed, without the need for precise timing measurements. On the other hand OpenSSL assigned the problem CVE-2020-1968. From then on, OpenSSL uses new DH keys by default since version 1.0.2. Mozilla also studied it in CVE-2020-12413. In this case they have solved it by disabling DH and DHE cipher suites in Firefox and Microsoft faced it in problem CVE-2020-1596. Finally, Raccoon Attack, although it is very difficult to exploit if given the right conditions, can lead to a leak of important information.
We recommend our tutorial on how to check TLS certificates to secure the web, and also how to know the TLS version of a web server .