If we want to make sure that a PDF document has not been altered since its creator saved it until it reached the computer, we must look at the digital signature. When signing a PDF document, a hash is stored in it that helps us to guarantee its integrity. If any change is made to the document, the hash is broken, the signature is no longer valid, and therefore we know that something has been changed. However, a group of researchers has just discovered a vulnerability that allows anyone to modify a PDF without breaking the signature .
PDF signatures are generally used in business environments. It is a way of ensuring that a document, or an invoice, has not been modified somewhere in between. In the event that any modification is detected with the signature, then the recipient will see a notice indicating that the digital signature is invalid.

It is not the first time that they have managed to break the security of a PDF document . In 2019, a group of researchers found a series of weaknesses in the main viewers through which it was possible to modify the content of any document without jumping the invalid signature notice. The viewer developers created patches to fix this problem and make the signatures more reliable.
However, this very week, a group of German security researchers have found a way to bypass all these viewer security measures and thus break the integrity protection of digitally signed PDFs.
Shadow Attacks: hide content in PDFs without breaking the signature
The technique used to carry out these techniques is known as ” Shadow Attack “, or “Shadow Attack”. Unlike the techniques used so far, this type of attack takes advantage of the flexibility offered by the original PDF format. In this way, the author of the document can see the original document, while the victim will see a totally different document. And in both cases, the digital signature is still valid.
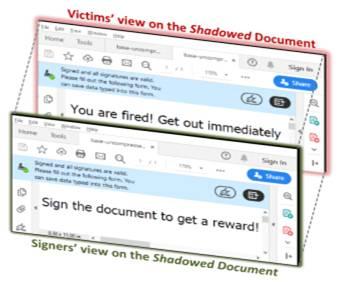
This technique can be used in a number of ways. For example, a text can be hidden behind an image that occupies the entire page. When the creator signs the document, and hackers get hold of it, they can modify it so that the image is not displayed, so only the content behind it could be seen. And the signature would still be valid.
Another way to take advantage of this vulnerability is by substitution . The Adobe format allows you to modify certain elements that are not part of the integrity of the document without modifying the signature. For example, the font. However, an attacker can add a purpose-built font to the document that changes the characters or numbers in the document.
And you can also combine both techniques to carry out much more complex attacks.
How to protect ourselves
The truth is that these types of cyber attacks are quite targeted. It would be rare to see these techniques in massive attacks, for example via email. But it could happen. And because these techniques abuse legitimate Adobe features, they cannot be blocked by patching the viewers.
Therefore, the only way to be sure that the file has not been modified is to make sure, with whoever created it, that the content we see is really the one that was originally there , and that nothing and nobody has been able to change it on the way. from your PC to ours.