
SMB (Server Message Block) is one of the protocols par excellence for sharing files on the local network, in 1998 Microsoft renamed this protocol to CIFS (formerly it was known as SMB but it has been renamed to CIFS (Common Internet File System)) . Since then it is known as SMB / CIFS in many places, the latest versions of SMB / CIFS incorporate support for hard and symbolic links, larger file sizes, and we even have authentication and secure file transfer using cryptographic protocols. Samba is the free implementation of the Windows SMB / CIFS protocol, so we will have compatibility between Microsoft systems and Linux and Unix-based operating systems without problems. Today we are going to explain how to enable or disable the different SMBv1 protocols,
SMB / CIFS characteristics in its different versions
SMB is a network protocol that allows us to share files, folders and printers on the local network between different operating systems, including Windows, Linux, MacOS and any Unix-based operating system that incorporates Samba. This protocol is within the application layer, and underneath, it makes use of TCP port 445, therefore, data transfers are reliable because there is retransmission of the data in case of problems. Since the birth of SMB / CIFS until now, we have several versions that have been incorporating improvements in the operation and also in the security of the protocol, however, not all servers that work with SMB / CIFS make use of the latest versions. protocol, so we could run into unexpected crashes when trying to connect to a local SMB server.
Access to SMB / CIFS resources can be done through authentication with local users, through RADIUS or LDAP server-based authentication, and, of course, through active directory authentication. At the configuration level, we could configure the server to avoid null passwords, we could also create guest accounts that will allow access to certain resources without any type of authentication. Other features of SMB / CIFS is that we can enable support for OS / 2 extended attributes in a shared resource, as well as store these DOS attributes if we are using Microsoft operating systems. Of course, we can establish a mask for creating files and also directories, so that those files or folders that we are going to create new ones have specific permissions.
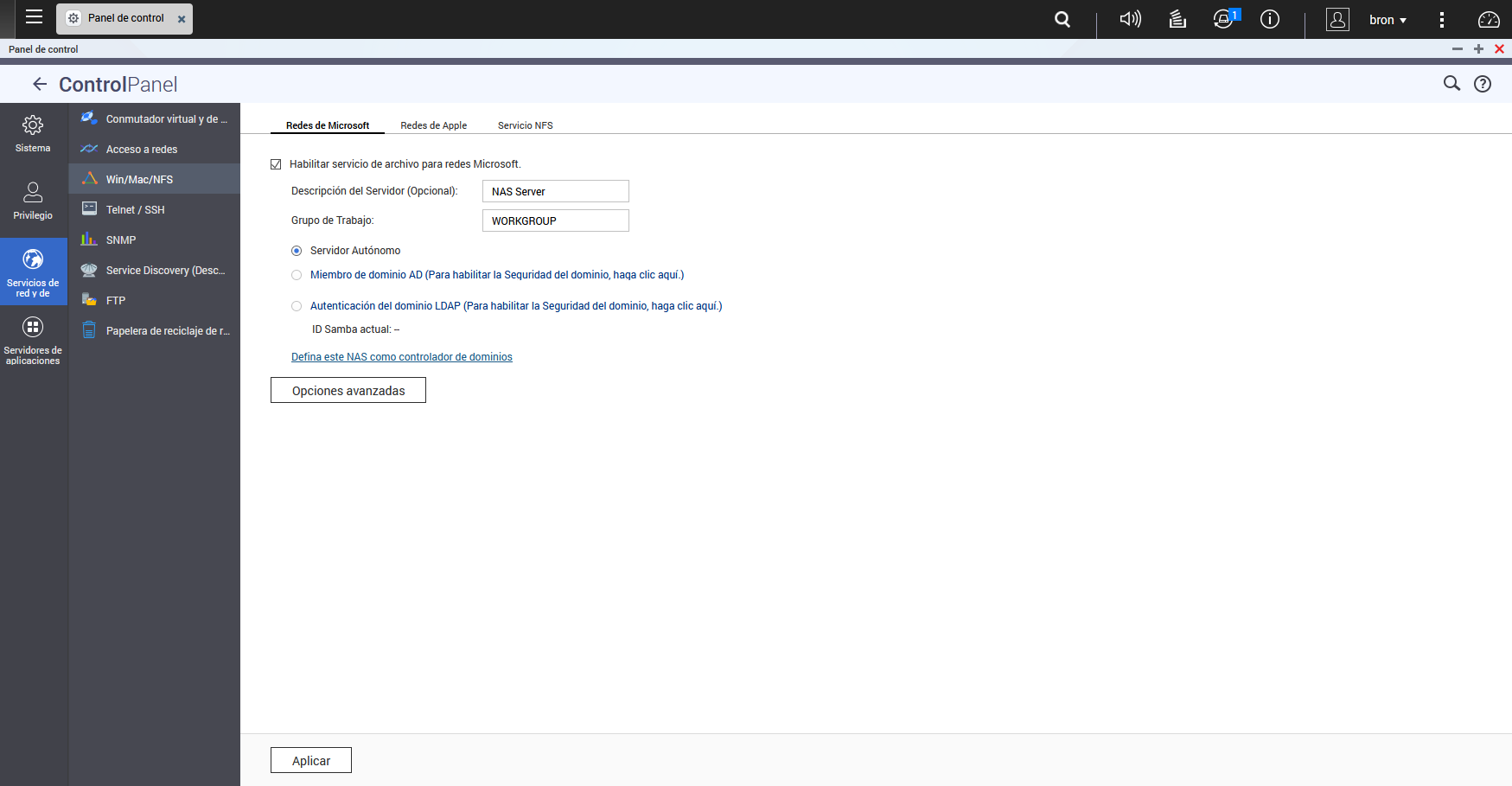
Regarding the performance of SMB / CIFS, we can enable asynchronous I / O, in order to achieve better reading and writing speeds in Samba resources, in addition, this could only be used for files of a size greater than that defined in the configuration of the server. When we are going to configure an SMB / CIFS server, the version used is very important, both on the server and on the client. At the configuration level, we can define different parameters to set the maximum supported server-level protocol, and also the minimum server-level protocol, in order to provide the best security to clients. For example, a very secure configuration would be to support only the SMB3 protocol, however, we may have problems with some clients that only support up to SMB2,
SMB / CIFS version 1
The first version of this protocol was born in 1983 and was built using Microsoft’s NetBIOS, however, in later versions NetBIOS was no longer used. All the old versions of Microsoft Windows make use of SMBv1, however, the new versions of the versions of Windows 10 and Windows Server do not incorporate SMBv1 installed in the operating system for security reasons, because it has been shown that this protocol is currently not secure at all and it is not recommended to use it. For example, Windows Server 2016 and later and Windows 10 Fall Creators Update do not include this version by default.
It is also true that some routers still use the first version of the protocol on their SMB / CIFS servers, in this case, little or nothing can be done to configure it with higher versions, because it depends on the manufacturer in the vast majority of cases. For example, if you have a third-party firmware such as OpenWRT or DD-WRT then you could disable this SMBv1 protocol and activate the latest versions, because the software incorporated in the firmware supports it.
SMB / CIFS version 2
Microsoft released the SMBv2 version for Windows Vista in 2006 and in Windows Server 2008. Although this protocol is private, its entire specification has been published to allow programs such as Samba for Linux and Unix to use it and for the different operating systems to be interoperable. otherwise, only Windows operating systems could exchange information with each other.
SMB2 is a great change compared to the first version, also in operation as well as in security. SMB2 reduces the establishment of the connection compared to SMB1.0, reducing the number of commands and subcommands, in addition, it allows to send additional requests before the response to a previous request arrives, saving a lot of time and improving speed when we have a high latency in the connections, or when we want to achieve the best possible performance. Other very important options are the possibility of combining multiple actions in a single request, reducing the amount of information exchanged. SMB 2.0 incorporates a series of identifiers to avoid reconnecting from scratch in the event of a brief network outage, in this way, we will not have to re-establish communication.
This new SMB 2.0 version supports symbolic links, caching, message signing with HMAC-SHA256 and better scalability to have multiple concurrent users on the same server, in addition, it also allows to improve the number of shared resources and files opened by the server. . While SMBv1 uses 16-bit data size and the maximum block size limit is 64K, in SMB2 32 or 64 bits are used for storage, this means that in ultra-fast network links such as Gigabit, Multigigabit networks or 10G, file transfer is much faster when sending very large files.
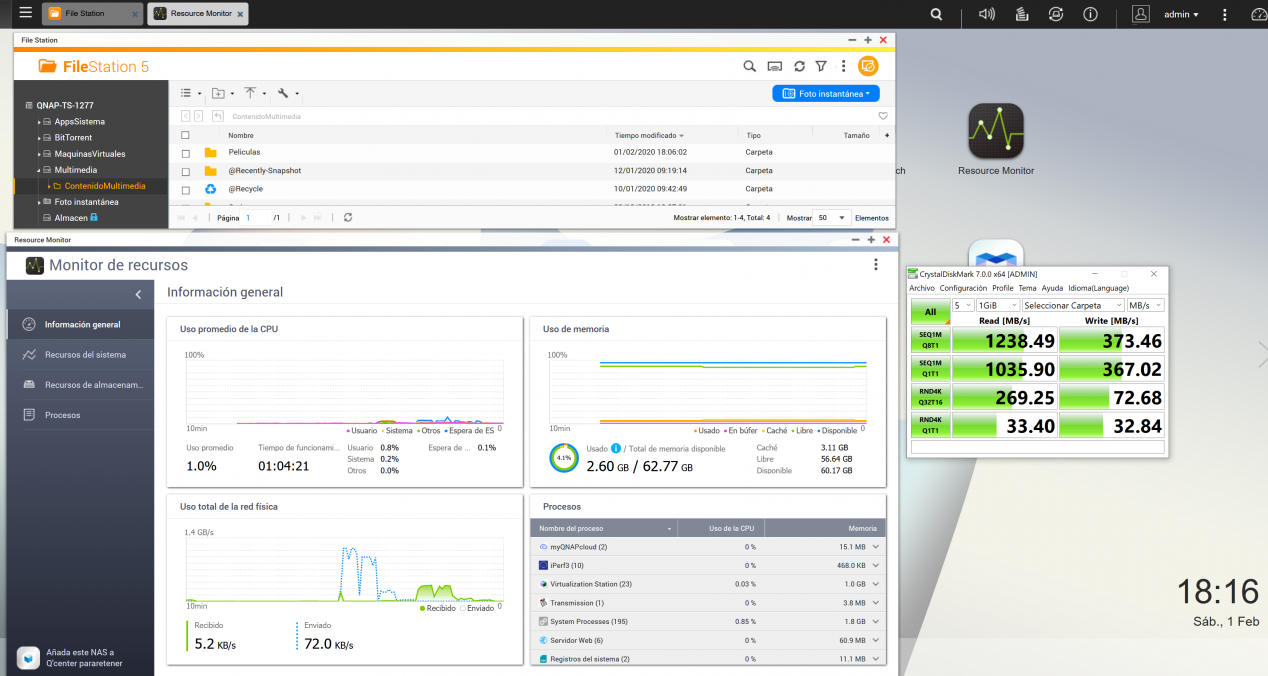
In RedesZone we have been able to achieve speeds of 1.2GB / s in a 10G network using SMB2, with a QNAP TS-1277 NAS server with SSD storage, and in the source PC we also had SSD storage, because traditional storage with Hard drives do not support these high speeds unless we use certain RAID of many disks.
Windows Vista and Windows Server 2008 and later operating systems make use of SMB2 by default, however, you may still encounter SMB1 on certain computers, so you may have to specifically enable it to connect to these servers as well. ancient. Finally, SMB 2.1, which was introduced in Windows 7 and Windows Server 2008 R2, further improved performance with a new opportunistic locking mechanism.
SMB / CIFS version 3
This SMB 3.0 version was previously called SMB 2.2, it was introduced with Windows 8 and Windows Server 2012, with new very important changes aimed at adding new functionalities and improving the performance of SMB2 in virtualized data centers. Some of the changes introduced were the following:
- SMB Direct Protocol: this allows to use SMB over direct access to RDMA remote memory, any server with this version incorporates this functionality to greatly improve performance.
- Multichannel SMB: this feature allows us to make multiple connections per SMB session, to force communications as much as possible and squeeze the local network where we are running the server and clients.
- Fully transparent failover.
However, the most important feature is the authentication of the user in the SMB, now it is fully encrypted, before it is always done in clear text, so a malicious user could put a network sniffer and capture the user’s credentials. Thanks to this, authentication is done safely. The possibility of having end-to-end encryption with AES has also been incorporated in order to encrypt or encrypt file and folder transfers. Therefore, with SMB 3.0 we have two configuration possibilities:
- Secure authentication with encryption and unencrypted file and folder transfer.
- Authentication and exchange of files and folders with symmetric encryption, this will provide us with maximum security, but performance could be impaired.
If the SMB server does not support AES-NI in its processor, it is likely that the performance we achieve when transferring files and folders is really low, so it is highly recommended that you have a powerful processor with a hardware encryption engine . Currently all processors as of the year 2015 approximately have this technology, but you should review it in its technical specifications.
In addition to the SMB 3.0 version, the SMB 3.0.2 version was also introduced in Windows 8.1 and Windows Server 2012 R2, improving functionalities and performance, in addition, in these operating systems it is already possible to disable the SMB 1.0 version to improve security, because When connecting, clients can negotiate which SMB protocol to use.
Lastly, Microsoft has introduced SMB version 3.1.1 in Windows 10 and in Windows Server 2016 and later. This new version incorporates the symmetric AES-128-GCM encryption to provide the best possible security and the best performance in reading and writing, we also have the option to configure the CCM encryption mode. In addition to this, it implements a prior integrity check that makes use of a SHA2-512 hash, one of the most secure currently. Finally, this version of SMB 3.1.1 forces the negotiation of clients using SMB 2.0 or higher to be with security, that is, authentication with encryption.
Enable or disable different SMB protocols in Windows
Currently if we are using the latest versions of the Windows operating system, the SMB 1.0 version is disabled by default for security, because it is a protocol that is currently not considered secure, it is necessary that you use SMB 2.0 or higher to avoid security problems. However, it would be advisable to check whether or not we have the different protocols enabled to know which ones we need to enable or disable.
Next, we are going to explain how to detect, disable or enable the different versions of Samba, the first thing we have to do is click on the «Windows» key and then search for « Powershell «, we right-click the mouse and « execute it as administrator «.
SMBv1 both client and server
If we want to enable or disable SMBv1 support on our computer, we first have to verify if we have it enabled or disabled.
To detect:
Get-WindowsOptionalFeature -Online -FeatureName SMB1ProtocolTo enable the SMBv1 protocol (it is not recommended for security), you must put:
Enable-WindowsOptionalFeature -Online -FeatureName SMB1ProtocolTo disable it:
Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
SMBv2 / SMB3 both client and server
If we want to enable or disable support for SMBv2 or SMBv3 on our computer, we first have to verify if we have it enabled or disabled.
Get-SmbServerConfiguration | Select EnableSMB2ProtocolTo enable it:
Set-SmbServerConfiguration -EnableSMB2Protocol $trueTo disable it:
Set-SmbServerConfiguration -EnableSMB2Protocol $falseThis works for both the SMBv2 version and the SMBv3 version, in this way, we will not have a specific command for SMBv3 because it is already integrated in SMBv2, but we should verify if data encryption is activated, a unique feature in the latest version SMBv3:
Get-SmbServerConfiguration | Select EncryptDataIf it indicates “False” it means that data encryption is not enabled, to enable it, we must execute the following command:
Set-SmbServerConfiguration -EncryptData $TrueYou must make sure that the remote server supports SMBv3, otherwise, it will give you an error when trying to access the shared resources of any server.