When we want to check connectivity, we all use the Ping command, a tool that sends ICMP packets to a specific server to know if the communication is correct or there is a problem. However, this tool is very simple and does not allow practically any modification of the packets, nor does it use other protocols to send information. Hping3 is a more advanced application, which will allow us to modify the packets that are sent through the TCP / IP protocol, so that we can have a much greater control of these packets, being able to adapt them according to our needs.
Main features
Hping3 is a terminal application for Linux that will allow us to easily analyze and assemble TCP / IP packets. Unlike a conventional ping that is used to send ICMP packets, this application allows the sending of TCP, UDP and RAW-IP packets. Along with the analysis of packets, this application can also be used for other security purposes, for example, to test the effectiveness of a firewall through different protocols, the detection of suspicious or modified packets, and even protection against attacks. DoS of a system or a Firewall.
In the past, this tool is used for cybersecurity issues, but we can also use it to test networks and hosts. Some of the main applications that we can do with this tool are the following:
- Check the security and operation of the firewalls.
- Use it as an advanced port scan, although it is better to use Nmap for this task.
- Network tests using different protocols, ToS, fragmentation etc.
- Find out the MTU on the route manually.
- Advanced traceroute using all supported protocols
- Remote fingerprint from operating system
- Check the time away
- TCP / IP stack audit
Due to the large number of possibilities of this tool, in this article we are going to show you the main uses and how to do it.
Install Hping3
Hping3 is available in the official repositories of Ubuntu, Debian and also other Linux distributions, so to install it we simply have to open a terminal (or a package manager like Synaptic) and type in it:
sudo apt install hping3
The tool will occupy about 3,600 KB that, once installed, we can start using it.
Hping3 command listing
The functions that this program supports are immense. From performing a simple ping to sending packets through a specific port even hiding the source IP. If we want to know in depth all the parameters that this program offers us, we can consult the help included in the tool simply by typing in the terminal:
hping3 --help
Basic use of the tool:
- v –version shows the current version of hping3
- -c –count packet counter
- -i –interval timeout (uX for X microseconds, for example -i u1000)
- –Fast aliases for -i u10000 (10 packets per second)
- –Faster alias for -i u1000 (100 packets per second)
- –Flood sends packets as fast as possible, does not display responses.
- -n –numeric output with numbers
- -q –quiet silent command without showing it on screen
- -I –interface name of the interface, if nothing is set, by default it is the interface of the default above gate.
- -V –verbose verbose mode for debugging
- -D –debug debugging information
- -z –bind bind ctrl + za ttl (defaults to destination port)
- -Z –unbind unlinks ctrl + z
- –Beep beep for each received packet that matches
Modes:
- Default mode is TCP
- -0 –rawip RAW IP mode
- -1 –icmp ICMP mode
- -2 –udp UDP mode
- -8 –scan mode SCAN mode.
- -9 – ready listen mode
Example: hping –scan 1-30,70-90 -S www.target.com
IP:
- -a –spoof spoof the source IP address
- –Rand-dest random destination IP address.
- –Rand-source random source IP address.
- -t –ttl ttl (default 64)
- -N –id id (random default)
- -W –winid use win * id byte order
- -r –rel relativizes the id field (to estimate host traffic)
- -f –frag fragments packets into more than one fragment, can traverse weak ACLs
- -x –morefrag fragments more
- -y –dontfrag does not fragment packets.
- -g –fragoff sets the fragment offset
- -m –mtu sets a virtual MTU, it implies that the fragment of the packet is greater than the MTU.
- -o –tos type of service (default 0x00), try doing –tos help
- -G –rroute includes the RECORD_ROUTE option and shows the path buffer
- –Lsrr loose source routing and route log
- –Ssrr strict source routing and route log
- -H –ipproto sets the IP protocol, only for RAW IP mode.
ICMP:
- -C –icmptype ICMP type (defaults to ICMP Echo request)
- -K –icmpcode ICMP code (default is 0)
- –Force-icmp sends all ICMP types (by default only sends supported types)
- –Icmp-gw sets default gateway address for ICMP redirect (default 0.0.0.0)
- –Icmp-ts aliases for –icmp –icmptype 13 (ICMP timestamp)
- –Icmp-addr alias for –icmp –icmptype 17 (ICMP subnet mask address)
- –Icmp-help displays help for other icmp options.
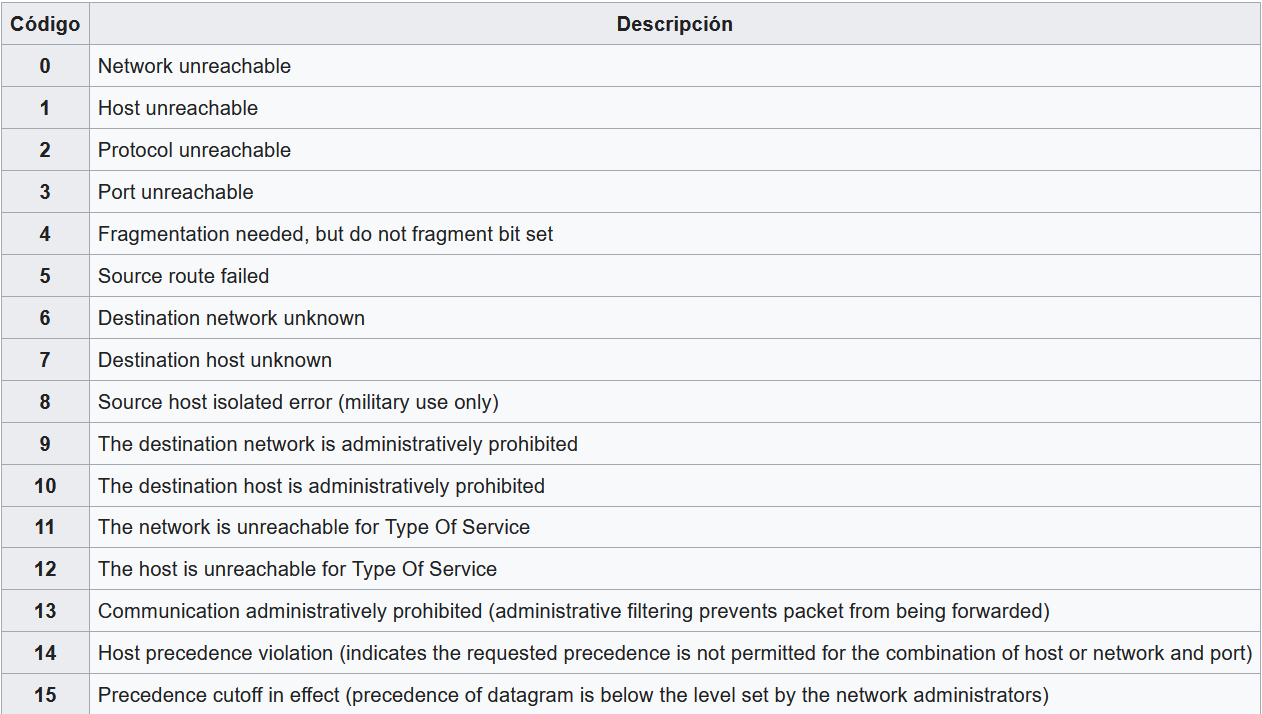
ICMP codes
It is very useful to know some ICMP codes that hping3 could show us, below, you have all the most used ones:
TCP / UDP
- -s –baseport base source port, default is random
- -p –destport [+] [+] <port> destination position (default 0) ctrl + z inc / dec
- -k –keep keep source port
- -w –win window size, default 64
- -O –tcpoff sets tcp data offset false (instead of tcphdrlen / 4)
- -Q –seqnum shows only sequence number
- -b –badcksum (try to) send packets with spoofed IP checksum, many systems will fix this checksum when sending the packet, so you will have a wrong checksum at the UDP / TCP level.
- -M –setseq sets the TCP sequence number
- -L –setack sets TCP ack
- -F –fin sets FIN flag
- -S –syn sets SYN flag
- -R –rst sets RST flag
- -P –push sets PUSH flag
- -A –ack sets ACK flag
- -U –urg sets URG flag
- -X –xmas sets unused X flag (0x40)
- -Y –ymas sets Y flag unused (0x80)
- –Tcpexitcode uses the last tcp-> th_flags as the exit code
- –Tcp-mss enables the TCP MSS option with the given value
- –Tcp-timestamp enables the TCP timestamp option to guess the uptime.
Options common to all
- d –data data size, default is 0.
- -E –file data from a file.
- -e –sign adds a signature
- -j –dump dump packets in hexadecimal
- -J –print dumps printable characters
- -B –safe enables “safe” protocol
- -u –end tells you when a file has reached the end
- -T –traceroute traceroute mode (implies –bind and –ttl 1)
- –Tr-stop Exit when the first non-ICMP packet is received in traceroute mode
- –Tr-keep-ttl Keep the source TTL fixed, useful for monitoring just one hop
- –Tr-no-rtt Does not calculate and does not display RTT information in traceroute mode
- ARS package description (new and unstable)
- –Apd-send Send packets described with APD
Examples of using Hping3
Simple ping test
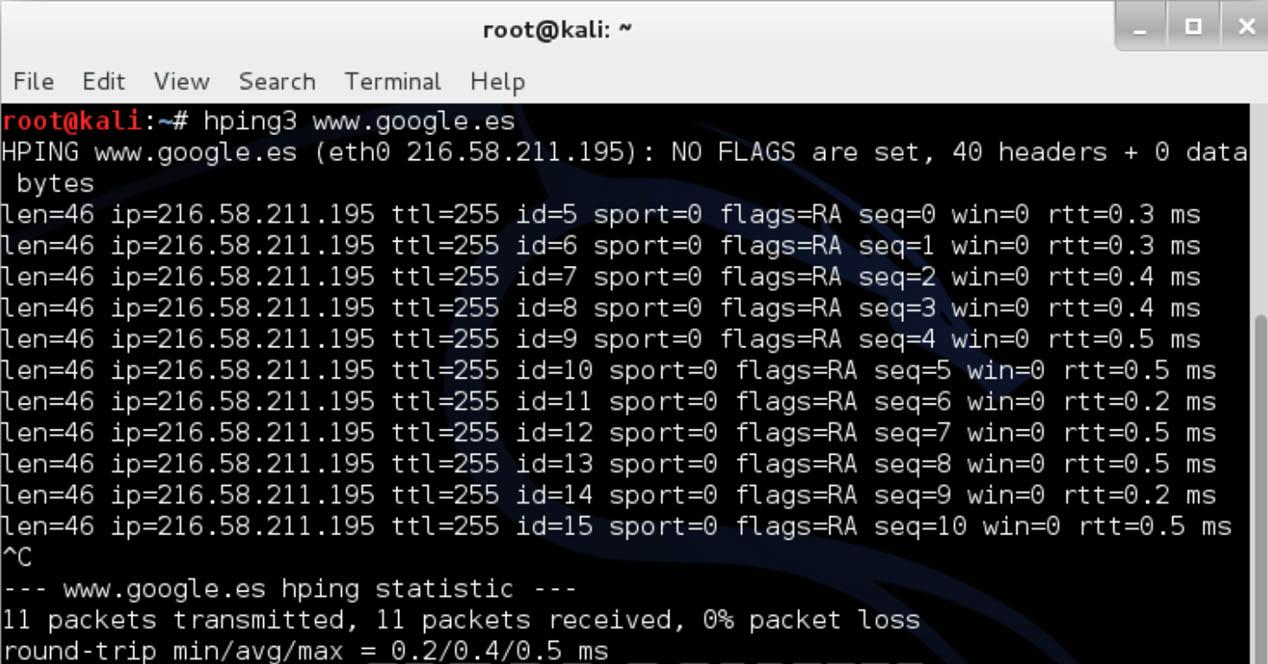
We can use this tool like the conventional ping command, obtaining practically the same results. To do this we simply have to type:
hping3 www.google.es
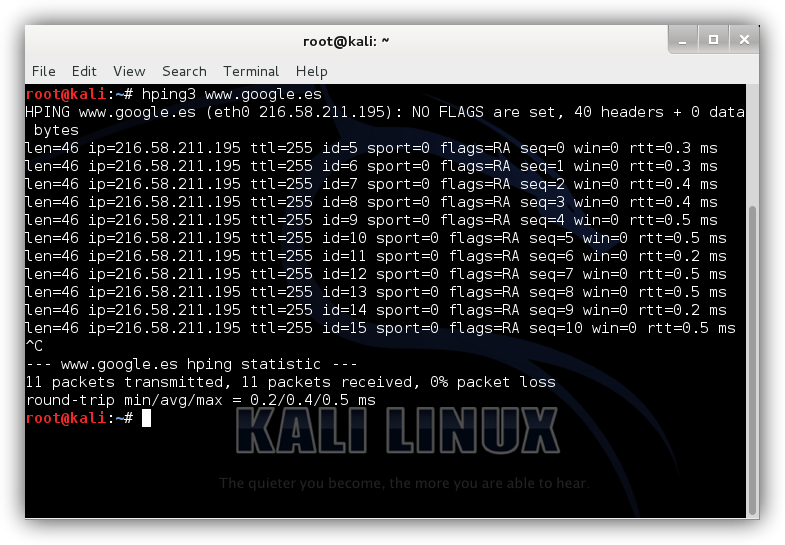
And we will see how this simple connection test is performed. (We can change the Google domain to any other or directly use an IP to ping it).
Plot connection path
In a similar way to the “tracert” option in Windows or “traceroute” in Linux, with this tool we can also follow all the jumps between networks of a packet from when it leaves our computer until it reaches its destination, being able to know at any time if there is some kind of problem in the connection.
To do this we simply have to type:
hping3 redeszone.net -t 1 --traceroute
Port scanning using the TCP SYN flag
This tool also allows us to send packets under the TCP protocol, in the purest Nmap style. To perform a scan using this method, we will type in the terminal “hping3 –S [Destination IP] –p [Port]”, the result being similar to the following:
hping3 -S www.google.es –p 80
The result of this test will return an SA flag, which means that it corresponds to SYN / ACK , that is, the communication has been accepted, or what is the same, that the port is open . Otherwise, if the value is RA it corresponds to RST / ACK or what is the same, that the communication has not been carried out correctly because the port is closed or filtered.
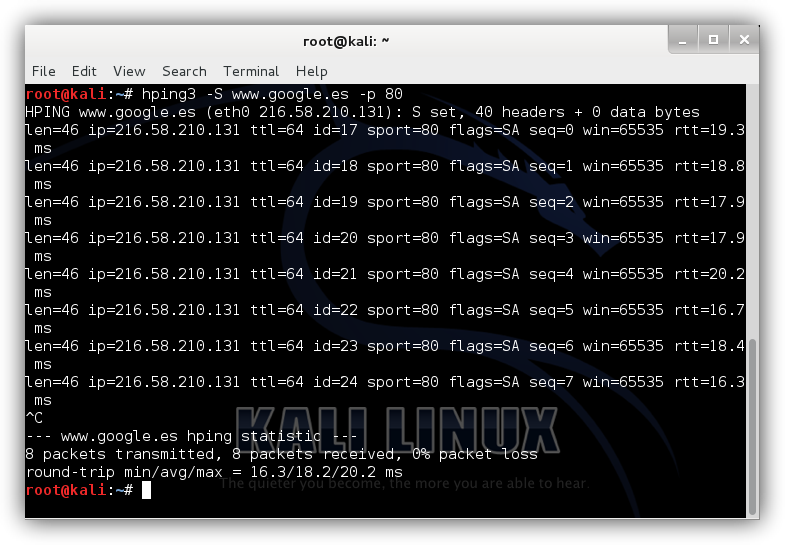
In this way we will be able to know, for example, if communication is allowed to a certain port, or if otherwise the Firewall is filtering it.
Sign packages with a custom text file
It is possible to use this tool to modify the packages we send and insert a personalized message in them similar to a signature. To do this we simply have to type:
hping3 redeszone.net -d 50 -E firmaredeszone.txt
This command will introduce into the Ping packages the content of the indicated txt file. If we analyze these packages with suitable software such as WireShark we would see that within them is the content of the file in question.
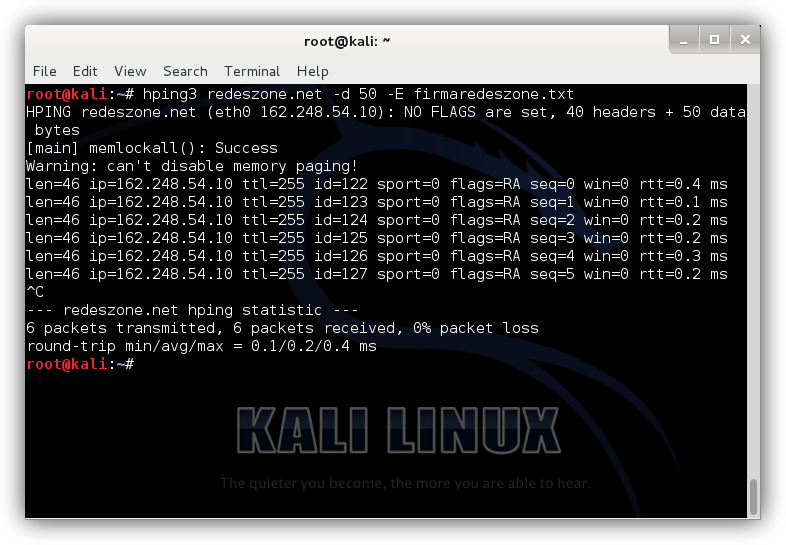
The entered parameters mean:
- -d: The length of the message that we are going to enter, in this case, 50.
- -E: File from which we are going to take the message signature that we want to introduce to the packages.
We can also use other parameters, for example, -p to indicate the port to which we want to send these packets or -2 to send the packets through the UDP protocol.
Generate multiple requests to test DoS and DDoS protection
This tool will also allow us to check the stability of our system against network attacks such as DoS and DDoS, generating real tests, either towards localhost or towards another server inside (or outside) the network.
We can make a series of unique pings by modifying the source IP of the same in the TCP / IP packets simply by typing:
hping3 --rand-source 192.168.1.1
Likewise, we can add the –flood parameter so that the packets are sent in real time in bulk. In this way, we will be able to check, firstly, if our firewall works and, secondly, how well our system responds to a threat of DDoS attack.
For this we will type:
hping3 --rand-source --flood 192.168.1.1
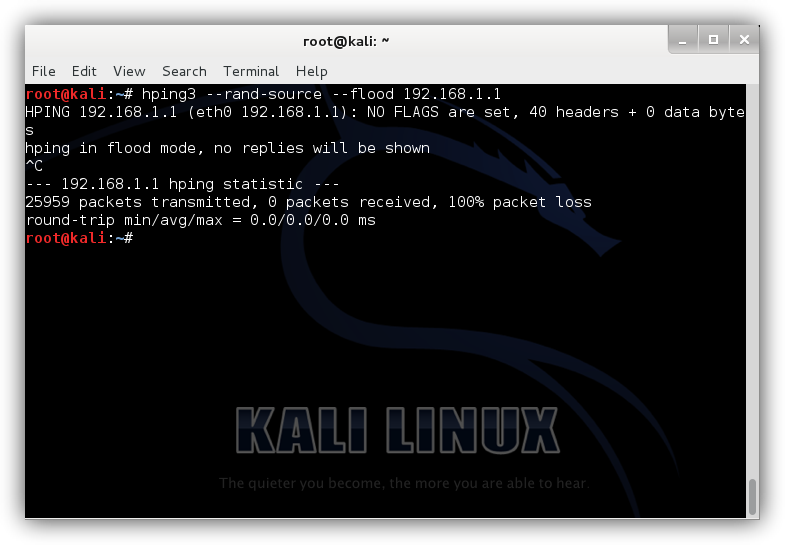
In just a couple of seconds we have generated more than 25,000 packets, so we must be careful as our network may be blocked and unusable.
With this, a large number of packets with a “false origin” will begin to be generated (thanks to the rand-source parameter) that will be sent continuously to the destination server (in this case 192.168.1.1). In this way we can verify the robustness of our system against DDoS attacks since, if the system stops working or crashes, there may be a configuration failure and that we must apply the corresponding measures to prevent this from happening in a real environment.
This tool is very useful, although it should always be used in closed and controlled environments since going outside it is possible that we end up carrying out a denial of service attack on a team that we should not, this being illegal and may end up sanctioned for it.
We recommend that you access the official hping MAN PAGE to find out all your options.