The Google Chrome web browser is the most widely used by users worldwide, in fact, statistics from the end of last year indicate that more than 65% of Internet users use this browser. Far away we have other browsers like Firefox or Safari for Apple computers. However, in recent years more serious vulnerabilities are appearing in Google’s browser, why is this? Why weren’t there so many security flaws before and now there are? Today in this article we are going to explain it to you.

More and more vulnerabilities appear
In Google’s security blog we find more and more security flaws in the Chrome browser, it seems that there has been a fairly significant increase in the security flaws found, and how cybercriminals are taking advantage to launch exploits and try to infect users. users. However, as they comment on the official security blog, this is not the case.
The main reason Chrome now seems to have more security flaws is because it has more visibility to attackers , actually this is a good thing, because it means that they can respond to these vulnerabilities with patches much faster than before, with the objective of protecting its users. A few years ago the vulnerabilities in Chrome did not have as much visibility, although it may seem that there were no errors, there were but they were “hidden”. Now this has radically changed and allows Google to solve them much sooner, in addition, they also learn how real attackers operate.
Google’s Project Zero team has publicly tracked all zero-day security flaws, ie unknown vulnerabilities that attackers are exploiting to their advantage. In the following graph you can see the main web browsers and the related security flaws, paying special attention to the now defunct Flash and also to WebKit, although they are not browsers, they were or are part of browsers in a very important way.
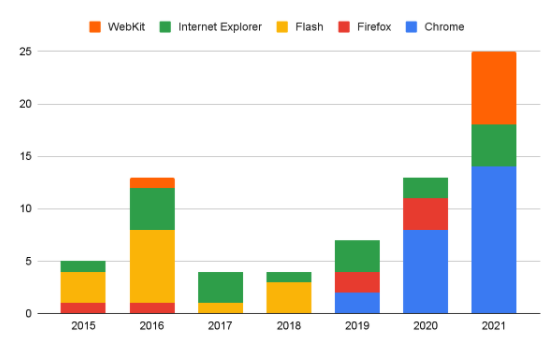
As you have seen, between 2015 and 2018 it seems that there was no security flaw in Google Chrome, something that is not possible. The team did not detect any 0-days during those years, but that does not indicate that there were none and that they were stealthily exploited by cybercriminals. As of 2019, security flaws in Chrome have grown very significantly, but this is because they simply have more visibility than before, that is, there is more transparency with 0-days.
Another of the reasons that Google officials have commented is because Chrome continues to grow and increase its share of use, this means that cybercriminals are more focused on this web browser because it could affect more potential victims. Cybercriminals always want to make money, and their targets try to be very numerous, with the aim of doing as much damage as possible. It makes no sense to spend a lot of resources on a seldom-used web browser, because the potential victims will be few in number. We should also keep in mind that before 2019 Flash is always attacked, because it was a software that was a real 0-day sneak, and with its disappearance, cybercriminals have focused more on Chrome.
We should also keep in mind that previously only one 0-day failure was needed to compromise the web browser, now at least two are needed. The first failure will serve to execute the code, and another failure will cause this code to leave the sandbox used by Chrome, so this “fattens” the statistics. Finally, the Chrome browser is much more complex than before, and this causes programming errors and the number of possible 0-days has grown, to mitigate this problem a bit, they continue to improve their sandbox to isolate all web pages.

In summary, the reasons why Chrome now seems to have more security flaws are:
- Greater transparency when communicating 0-day security flaws to users.
- Evolution of the attackers, they have abandoned Flash to focus on the popularity of Chrome.
- It takes at least two security bugs instead of a single bug to compromise the rendering process and the sandbox, so this multiplies the stats. It is also possible that multiple failures may need to be chained together to achieve a single step.
- More complex software and more possible programming errors.
Although more and more bugs are appearing, the Chrome team is heavily involved in several projects that aim to provide the best possible security:
- Improved website isolation, especially on Android
- Heap sandbox: Will prevent attackers from using JavaScript JIT compilation bugs.
- MiraclePtr and *Scan projects to avoid exploiting the biggest browser process bugs.
- Write parts of Chrome with memory-safe programming languages. This typically represents up to 70% of exploitable security bugs.
- Methods for mitigating 0-day errors.
As you can see, although the number of 0-day notifications from Chrome has increased, it doesn’t mean that there weren’t any before, just that they weren’t communicating.