Maintaining security on the network is a very important factor to avoid password theft, data leakage or malware sneaking in. We can take into account certain precautions, such as using antivirus, having everything updated or good programs. In this article we are going to focus on isolating a browser . We are going to explain what it consists of and why it is something that can help improve security when we browse the Internet.

How browser isolation works
When we browse the Internet we can leave a lot of traces and they could even attack us through different methods. What web browser isolation does is reduce the risk of attacks . It is a cybersecurity practice that is responsible for separating browsing activities, such as visiting a website, from the equipment we are using. In other words, it will separate Chrome, for example, from the Windows system that we have on our computer.
Good browser isolation will improve the security of web activity. It will completely isolate your browsing activity with the local network. It is one more method that we can take into account to preserve proper functioning and avoid security problems.
One option for implementing browser isolation is to run it on a remote or virtual server . The connection to this server is based on the cloud, so it will not have contact with the system that we are using. It always carries an extra layer of security and will allow the remote browser to be properly isolated from the rest of the network.
When a browser session ends, all content is automatically deleted . This means that it will not store data, nor possible malware that may have been present. When the safely isolated browser is started again, everything is back to the way it was, empty.
Why is it good for security?
It is very interesting in order to be protected from possible attacks that appear on the network. For example, being protected when visiting a web page that may contain malware and infect our device and thus affect other programs that we are using or our personal information.
A clear example is protection against zero-day exploits . They are vulnerabilities that have not been corrected and that an attacker could use to send malware, steal passwords, information or in some way put the security of that computer at risk. There are threats of this type that are based on the web.
It will also mean greater peace of mind when browsing the Internet without the risk that we may be victims of an attack. For example websites that may have malicious code that is executed when we make a visit. We are not going to have the risk of this affecting our team, since everything takes place in an isolated environment.
In addition, it will be very useful in order to protect our team from Phishing attacks . Sometimes we go to a website and click on a link and download a file that is actually malware. That will affect our system and can be a serious problem. If this happens with browser isolation, the malware will stay there, isolated.

Therefore, browser isolation allows you to reduce the attack surface and browse more securely, without compromising personal data. It is basically isolating the danger, making sure that any threat has no further path than that isolated section and does not reach the rest of the network or computer.
Tips for safe browsing
Beyond having explained what browser isolation consists of, it is important to take into account certain recommendations to browse safely . The objective is to prevent our personal data from being compromised and to minimize the probability of malware entering.
Have the browser updated
The first thing to mention is the importance of always having the latest versions . It is essential to have the browser correctly updated and thus correct any vulnerability that may appear. You have to apply this to Google Chrome, Mozilla Firefox or any program you use.
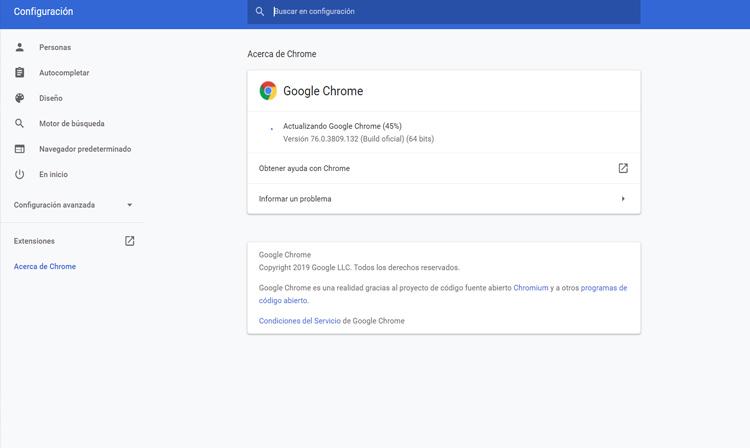
For example, in Chrome, to update it you have to go to the top right menu, go to Help and click on Google Chrome Information. There it will begin to analyze what version you have installed and add a new one if it is available. You can do this periodically and make sure you always have the latest version installed .
Use security programs
You must also have security applications installed. For example a good antivirus , such as Windows Defender, Avast or Bitdefender. These applications will help prevent the entry of malware and eliminate possible malicious files that may be on our computer.
In addition, another option is to have browser extensions that help improve security. There are many available for the main ones, such as Chrome or Firefox. Of course, you should always make sure that they are really going to contribute something positive, since the more add-ons you have installed, the more performance problems you may have.
Download only from trusted sources
In this case, it is about avoiding making the mistake of downloading documents or programs that could be dangerous. A clear example is the applications, where we can include the browser extensions themselves. You have to download them only from official and reliable sources , since otherwise we could have problems.
If we download programs from third party sites they may have been maliciously modified. They may contain dangerous code and serve to exploit certain vulnerabilities or infect the system. This happens, for example, when we click through a link that comes to us by mail and we download a program from there.
Common sense
But perhaps most important of all is common sense. It is a bit in tune with what we mentioned about downloading only from official sources. It is essential not to fall into the trap of hackers, such as Phishing, downloading dangerous files by email, clicking on messages that reach us through social networks, etc.
This is something that you should apply at all times and not just when browsing the Internet. You must take care of the use you give to any device on the network, always maintain a good configuration and avoid any error that could compromise security at any given time.
All in all, browser isolation is a very useful feature used in cybersecurity to protect data and the system when entering a web page. It is also essential to carry out a series of recommendations that can be very interesting to minimize security problems.