No one is saved from phishing, not even those who are leaders in organizations. On this occasion, we are going to talk about a phishing variant that guarantees very good results for cybercriminals: whaling. People with high hierarchy in an organization or who belong to financial or technological institutions are part of the main target of this cyber threat. Today in this article we are going to show you what are their differences regarding phishing, how to identify them and most importantly: how to protect the organization from these types of attacks.
What is a Whaling attack?
As we highlighted at the beginning, it is a variant of phishing. What distinguishes it from others is that it is aimed at people who occupy senior positions in an organization. For example, directors, presidents, and managers. This variant turns out to be very effective because it is carried out using Social Engineering techniques. Remember that the latter has the purpose of convincing people to carry out an action that involves the use of their personal data, such as sharing access data to a specific account or making an “emergency” bank transfer.

Let us dwell on the detail of the urgency. From the moment the cybercriminal manipulates victims to catch that sense of urgency, they will simply do what is asked of them. This will be so even if the action is not entirely reasonable. We know that in desperation or the desire to avoid any inconvenience, one could do anything. Whaling is one of the attacks that generates the most income for those who carry it out, mainly because its victims work for financial institutions, organizations that process payments or technology companies that offer services at the forefront.

Main strategies of the attackers
The UK National Security Agency explains in great detail how whaling is carried out. This guide will show you the most important thing and what is recommended to do to avoid being a victim of Whaling. First of all, it is good to know that not long ago, phishing was considered unique, that is, anyone could be the victim of the same type of malicious email.
However, the passing of the years has allowed cybercriminals to gain more knowledge about key terminology from the business, industry and references field that only victims could understand. An email message that serves as a bridge to carry out Whaling is disguised as one of the many messages that a boss, manager or director receives on a daily basis. Reports, balance sheets and even personal and corporate banking transactions.
This is the importance of the security awareness of these people with high positions. Unfortunately, it is customary for them to have the prejudice that nothing will happen at all with their data and that they can do whatever they want online, both in the workplace and personally. This naivete is exploited by cybercriminals to apply social engineering and carry out this dreaded variant of phishing.
Receive email after a call
This is one of the simplest but most effective methods. The cybercriminal communicates with the victim, asks some questions that make the victim feel confident. Also, it can be expressed in such a way that you can transmit that sense of urgency so that you can confirm the data as soon as possible. In this case, the email.
A frequently occurring scenario is that those who attack pose as the victim’s trusted providers or contacts. How can Whaling become so specific? Before carrying out the attack in question, the cybercriminal may otherwise compromise the victim’s data such as their contacts in Google, Outlook and others. In this way, it is easier to be able to “disguise” yourself from someone the victim would trust.

The victim will be so confident in email messages that they will not even carry out one of the key phishing prevention practices – checking email addresses. Let’s cite a random example: example123 @ redeszone.net is not the same as example_123 @ redezon.net . We note that there is a similarity between both directions and many times, due to the rush or other type of situation, the victim does not take those few seconds to corroborate if whoever was contacting you has really good intentions.
Social networks for personal and professional use
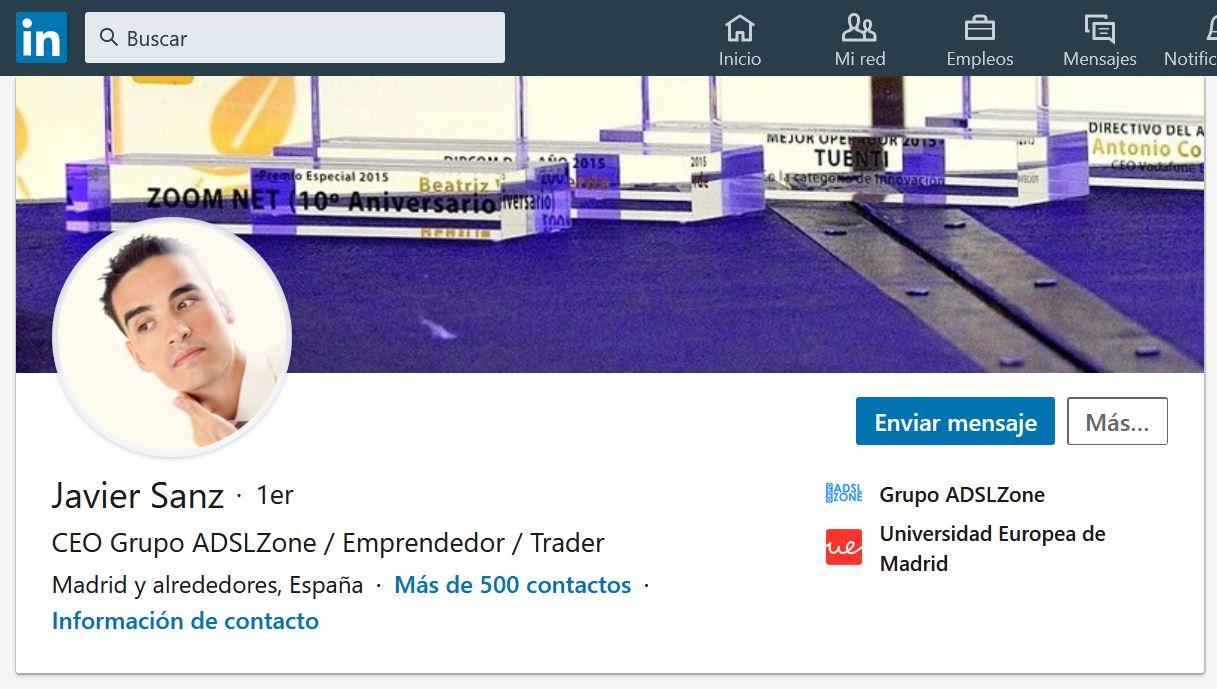
As well as the content of the person’s email activity, their social network profiles provide a lot of information to carry out Whaling. Professional social media accounts like LinkedIn can provide a lot of information regarding the victim’s network of contacts. If you use this platform, you can notice the fact that every time you enter the profile of a contact of yours, it appears if it is your contact on the first, second or third level of connection.
In this case, if it is of the first level (1st) , it is most likely a contact with whom you interact frequently, a relative of yours or someone you trust. You don’t perceive it, but any type of social network exposes information about you to a great extent and this comes in handy to attackers.
We know that we could be somewhat extreme and, in any case, not have an account registered in any portal at all. Thus, no one will know about us and the things we do. However, connectivity has taken over our lives in such a way that it is impossible to avoid sharing personal data, even if we are as cautious as possible.
We must emphasize the latter: caution . Whether you are an organization manager or a common user, you should pay more attention to your online activity. Remember that phishing, in any of its variants, can appear at any time and benefit from your data or your financial resources. It is very difficult to recover from the damage that this type of attack can cause, so it is never unnecessary to doubt situations such as those of “extreme urgency”.