SSD drives have ended up conquering the market. The improvements they offer, together with the progressive drop in prices, has meant that many have installed them on their computers or have directly bought a new computer with this feature. Leaving aside debates about the useful life of SSDs, the truth is that their speed or reliability stand out above all else. However, we cannot relax as there is always a problem on the horizon that may affect us in the future.
In this case, we are talking about malware. Most of these threats are detected by the antivirus that we have installed on the PC. The problem comes when these malicious programs use advanced techniques to hide or place themselves beyond the detection capabilities of antivirus. We have seen it in the past and now we will see it again. In fact, a group of Korean researchers have developed a series of malware attacks that hide on your SSD and are undetectable by antivirus.

Take advantage of the Flex capacity feature
These attacks take advantage of Micron’s Flex capacity feature and “attack” a hidden area of the device. This feature is widely accepted and used by solid state drive manufacturers to optimize performance. Basically, it refers to the ability of the SSD to adjust to suit different applications and workloads.
This dynamic system creates and adjusts a “space” called over-provisioning that occupies between 7% and 25% of the total disk capacity. The area for this is invisible to the operating system and its applications, which includes security solutions and antivirus suites that we may have installed on the computer.
The SSD automatically adjusts the space based on the workload, depending on the need of the process to read or write data to the drive. All this is done in a transparent way for the user and that is precisely what these security researchers have taken advantage of.
From the Korea University in Seoul they explain that a cybercriminal can “attack” an area of invalid data that has not been erased between the “normal” space of the SSD and the over-provisioning (OP) area. Many manufacturers choose not to erase this area of invalid data to save resources which can be used to access sensitive information.
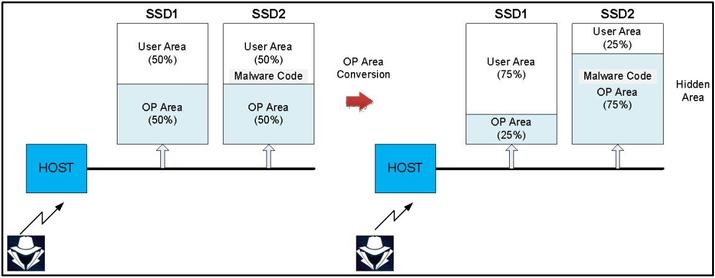
They have also shown how the over-provisioning (OP) area can be used as a secret enclave to hide malware. They explain it as follows in their research:
Let’s assume two storage devices SSD1 and SSD2 are connected to one channel to simplify the description. Each storage device has 50% OP area. After the hacker stores the malware code on SSD2, it immediately reduces the OP area of SSD1 to 25% and expands the OP area of SSD2 to 75%.
At this time, the malware code is included in the hidden area of SSD2. A hacker who gains access to the SSD can activate the malware code at any time by resizing the OP area. Since normal users keep 100% of the area on the channel, it will not be easy to detect this malicious behavior.