From the moment we connect to the Internet, our data is being controlled by all types of companies, such as Microsoft, Google and even our ISP. All the pages we visit and everything we look for will be associated to our ID and, therefore, to ourselves. And that information, of course, will be used for commercial purposes. It is almost impossible to connect to the Internet completely anonymously and privately. Although luckily there are options that help us achieve it, as is the case of Tails.
In an increasingly connected and threatened world, it is increasingly necessary to have a minimum level of privacy. Tails is a Linux distribution, based on Debian, whose main feature is that it has been designed in such a way that it takes users’ privacy and anonymity to the highest level.
Main features and installed software
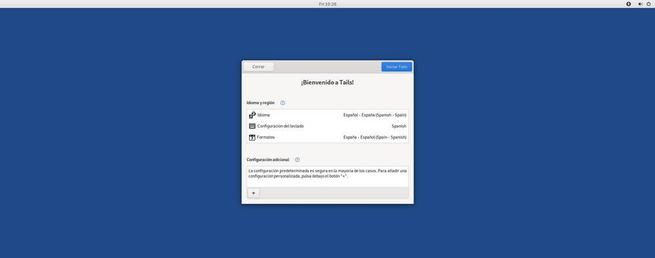
Tails protects the privacy and anonymity of users from the start. The first thing that catches the attention of this distro is that it is intended to be used from a USB stick in “Live” mode . This allows any user to boot the PC with it, load the entire system into RAM and leave no trace on hard drives. When the computer is turned off, the RAM data is deleted and it is impossible to know that Tails has been used on that computer. Unless, of course, we want to install it on a hard drive or use it as persistent storage.
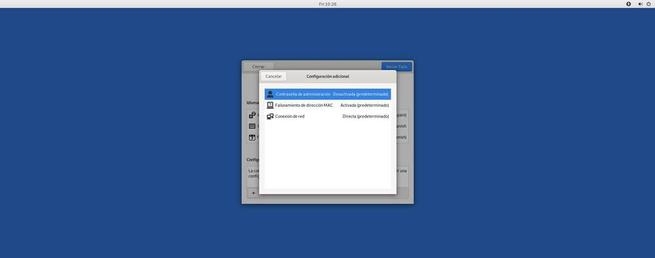
To protect the anonymity of users, this distro comes with a whole instance of Tor installed by default. This will allow us, from the moment the boot starts, all traffic leaves our encrypted and forwarded computer through this distributed network. To surf the Internet, Tails comes by default with the latest version of Tor Browser , the official Tor browser, based on Firefox, which is configured for maximum security and privacy. In addition, it comes with interesting extensions such as Torbutton, HTTPS Everywhere and NoScript, among others.
We can also find other very interesting distros, such as OnionShare, to share files in a totally private way, Pidgin, with OTR, for totally private instant messaging, Aircrack-ng to audit Wi-Fi networks and KeePass to manage our passwords.
The desktop chosen by the developers is GNOME. This allows all users to find a simple and familiar environment, very quick to use and master. Everyday programs such as GIMP, LibreOffice, Audacity and other tools have been installed next to the desktop to improve both the security and usability of Tails.
Finally, we can also find several Bitcoin wallets, such as Electrum and DeepOnion, to be able to operate with this cryptocurrency easily and with total security.
Download and launch Tails
It is very important to make sure you are using the latest version of Tails, and also that the image we have downloaded is the official one. This means that, if we are concerned about our privacy, we must make sure to download the latest version available from their website .
Downloading Tails from an unofficial website, or downloading an image from an old version, can seriously compromise our computer. We do not know if the distro has been modified to include spyware or other malware. And the privacy and anonymity in doing so is virtually nil.
When we download Tails (we recommend using torrent download) we will have an ISO image in our possession. What we must do with it is to burn it to a CD, DVD or a USB memory to create our Live operating system to boot the computer. The best way to do this is to use a program called “Etcher”.
When we have Tails on the Live-USB, just use it to boot our computer. We can start surfing the Internet anonymously and privately thanks to Tails and Tor. If we are going to use Tails from a virtual machine, then just mount the ISO on the VM and start it normally.
Keep Tails updated
Why is it important to keep Tails always updated to its latest version? Basically because the slightest failure that may appear in the distro can break all privacy and anonymity, exposing our identity and personal information.
The Tor network is plagued with hackers in search of the least opportunity to put our security at risk. Therefore, whenever a new version of Tails is released, it is imperative to update our Live-USB or download the new ISO image to ensure that we continue to maintain the same level of privacy and security.
Unfortunately, updating Tails from a Live-USB is not a simple process. Although it is true that in the latest versions it has been simplified. Unless we have a partition with persistence and some configuration in Tails, it is much better to flash the new Tails ISO from scratch on the USB to have the new version ready to boot.
The Tor network: one of the pillars of anonymity
If anyone can use Tor, what makes Tails so special? This Linux distro is not only Tor, it is a complete ecosystem to offer users an experience of maximum security, privacy and anonymity from the first moment. Without having to worry about making any additional configuration.
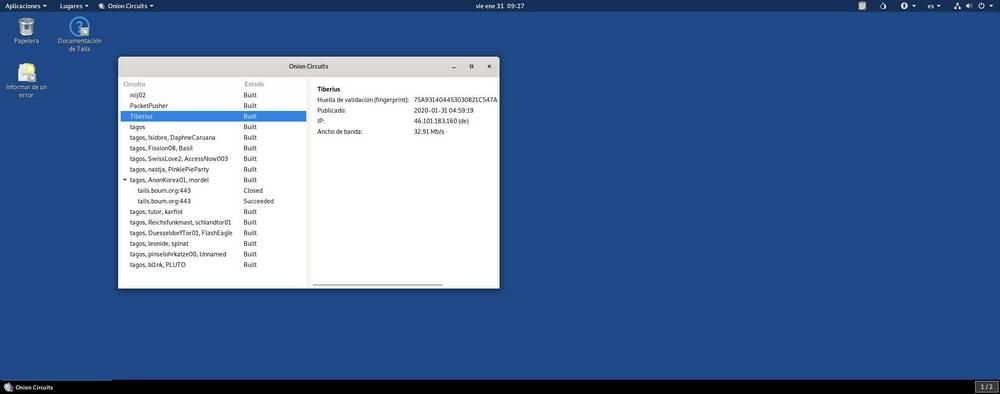
In addition to the many tools and configurations to preserve our security, one of the strengths of this distro is Tor and, above all, Tor Browser . From the first moment we installed it, we are already sending all traffic to the Internet safely.
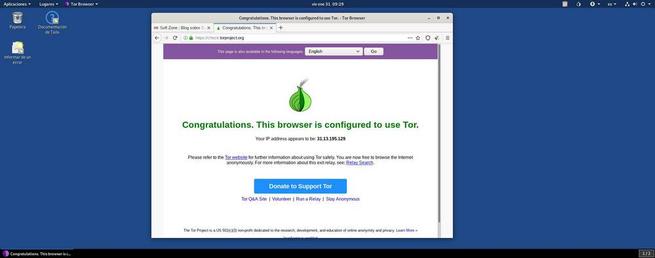
Thanks to Tor Browser we will be able to visit any normal Internet website without a trace, in addition to having access to the entire Deep Web. Without configurations and without compromising our security or our data. Of course, the fastest and easiest way to maximize our privacy on the network.
A distro for day to day? Why not
Although connecting to the Internet safely and anonymously is Tails’ main purpose, it is not the only one. This distro brings us a complete Linux ecosystem, with a GNOME desktop, and a large number of programs to use in our day to day.
In addition to being able to connect to the Internet normally from Tor Browser, thanks to programs such as GIMP and LibreOffice we will be able to work with Tails as if it were any computer focused on productivity. With the extra security provided by the Linux system.
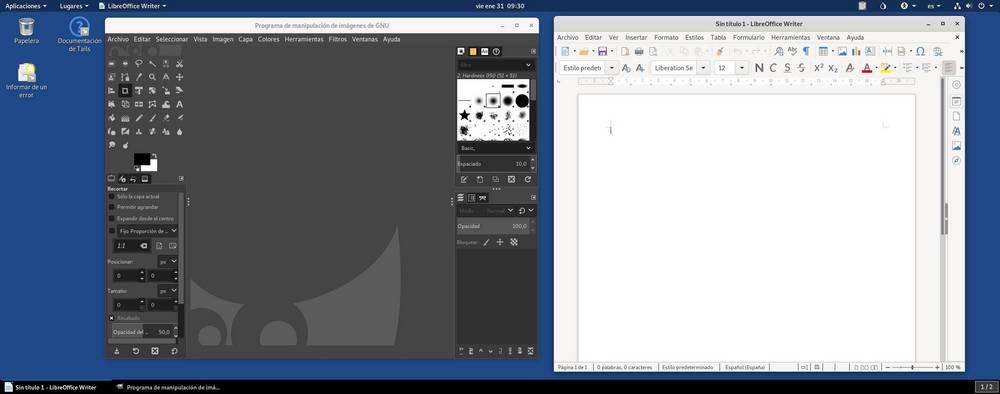
And, in addition, if we ever have to use a computer that is not the new one, for some reason, thanks to Tails we can do it without risking a single byte of personal information.