Cybercriminals are always looking for new formulas, they even observe those of their colleagues to carry out attacks on their victims. This time, it was the latter and they were inspired by the Ragnar Locker band. Thus with their Maze ransomware, like the previous ones, they have used a virtual machine to completely encrypt the computers and ask for the typical ransomware ransom.
The background to Ragnar Locker ransomware
In May of this year, Shophos alerted to the presence of Ragnar Locker ransomware that encrypted through VirtualBox Windows XP virtual machines to bypass security software on the end host. That virtual machine mounts the drives on a host as remote shares, then runs the ransomware on a virtual machine to encrypt the files on the share. Because the virtual machine is not running any security software and is mounting the host drives, the host’s security software cannot detect and block malware. This attack is started by first creating a tools folder that includes VirtualBox, a Windows XP mini virtual disk called micro.vdi, and various executables and scripts to prepare the system. Then also, it has the vrun.bat file, which will mount each shared drive, encrypt it, and then move on to the next shared drive with the virtual machine.

As we have explained before, the security software running on the victim’s host does not detect the ransomware executable on the virtual machine, and will continue to run and encrypt the files. Upon completion, the victim will find a personalized ransom note explaining that their company has been attacked and their files fully encrypted.
Maze ransomware and its use of virtual machines
It all begins when Shopos, attending to a customer incident, discovered that the Maze ransomware had tried to implement its ransomware twice. However, thanks to the Sophos Intercept X feature it was blocked. The virtual machine used by Maze was running Windows 7, while the one for the Ragnar Locker as we mentioned earlier was Windows XP. The investigation also revealed the following data:
- They found several installation scripts thanks to which it was possible to discover their way of acting.
- The attackers were found to have spent days creating lists of IP addresses within the target’s network. To do this, they used one of the target’s domain controller servers, and exfiltrated data from Mega.nz.

The Maze ransomware attacks started by using batch files and made several attempts to encrypt machines on the network. Then, since they did not achieve their goal, they created scheduled tasks to run the ransomware based on:
- Windows Update Security.
- Windows Update Security Patches.
- Google Chrome security update.
However, thanks to Intercept X’s Cryptoguard behavioral protections being activated, those Maze ransomware payloads were captured and quarantined on protected machines before they could cause damage. The attackers, having failed in their first two attempts, then opted for a more radical approach.
In the third attack, Maze deployed an MSI file that installed the VirtualBox VM software on the server along with a custom Windows 7 virtual machine. On the root disk of that virtual disk we have three files associated with the Maze ransomware:
- preload.bat
- vrun.exe
- payload (no file extension), which is the actual payload of the Maze DLL.
Then with the virtual machine already started, the Maze ransomware, a batch file called startup_vrun.bat would be executed that prepares the machine with the Maze executables.
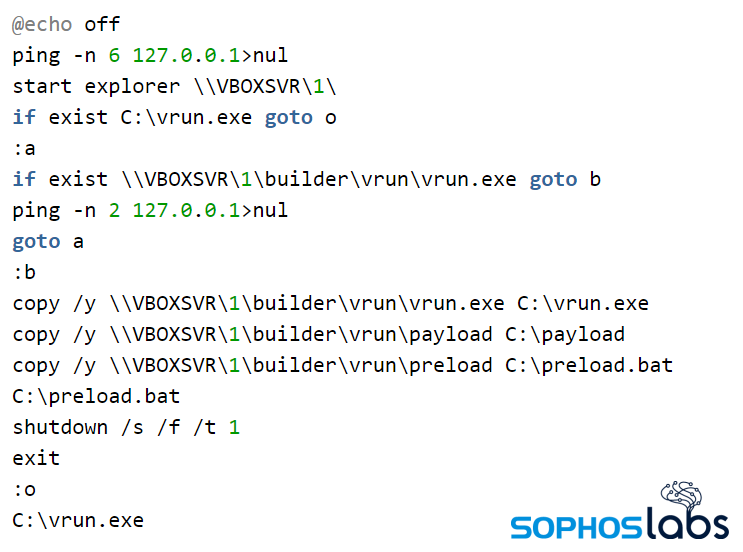
The machine then shuts down and once it restarts again, it will run vrun.exe to encrypt the files on the host. Because the encryption is done on the host’s mounted drives, the security software was unable to detect the behavior and stop it.
Maze ransomware versus Ragnar Locker comparison
Researchers from SophosLabs point out that Maze ransomware is more expensive to implement in terms of disk size compared to Ragnar Locker. Here we have a table in which you can see this:
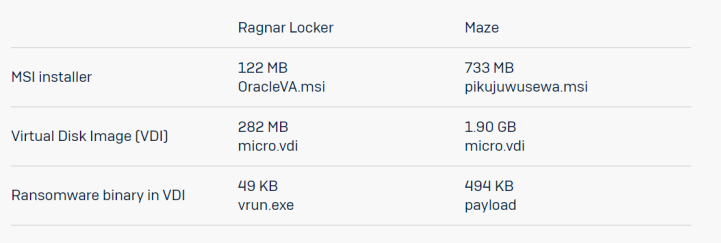
Ragnar Locker was implemented inside an Oracle VirtualBox Windows XP virtual machine. The attack payload was a 122MB installer with a 282MB virtual image. Instead, the Maze ransomware attackers took a different approach using a Windows 7 virtual machine. This caused the size of the virtual disk to increase significantly, but also added some new features to it. In this case we go to a 733 MB installer and a 1.90 GB virtual hard disk. Finally, as you may have seen, the creators of the Maze ransomware have used techniques similar to those of other cybercriminals such as Ragnar Locker.