Many people like to travel, some do it for work and others for leisure. Cybercriminals are everywhere and looking to profit from their attacks. An oversight on our part can facilitate the work of other people’s friends. In this tutorial we are going to make a series of safety recommendations to travel smoothly. One of the most important aspects, without a doubt, is the correct use of public Wi-Fi networks, should we connect to a public Wi-Fi network if we need it? The answer is complex, sometimes with the appropriate security measures we can do it, but in many others it would not be recommended.

Things we should not do on a public Wi-Fi network
Something very important that we should not do when we connect to a public Wi-Fi network is not to send confidential information . In that sense, we would have to focus on two things:
- Do not send emails that may contain sensitive data.
- We must avoid filling in information in forms that contain our personal data.
Another fundamental thing we must do to maintain security while we are traveling is not to log in with our accounts . The reason is because they could steal our username and password, and our personal information could be exposed.

In public Wi-Fi networks we must also avoid making payments . These types of operations can be insecure and the data of our credit card or other means of payment can be in the hands of cybercriminals. In the event that you have to pay yes or yes, it is highly recommended to use prepaid cards, such as Bnext or Revolut cards among others, however, try to pay with PayPal whenever you can, since we will have a payment gateway safe where the data of our cards will not be exposed.
We have to try not to enter unencrypted websites . In this case we refer to http pages, it is always advisable to enter HTTPS websites so that all traffic is encrypted point to point. On some occasions, there are public Wi-Fi networks that force us to fill in some data to be able to use them (captive portal), in this sense, it is important to read the terms of conditions carefully since, sometimes, we are agreeing to receive advertising and it can generate future spam problems.
We must have our devices ready before the trip
As for our laptops , we must ensure that the last day before traveling, the latest security updates are installed . In addition, you must have a good updated antivirus and anti-malware software, in addition, it would always be highly recommended that we have authentication with username and password to log in, and not only that, but it is recommended that our disk is fully encrypted. If you use Windows, you can activate Bitlocker on the operating system partition, to encrypt each and every one of the data, in this way, if someone is able to steal our PC and unmount the hard drive, they will not be able to access its internal content.

With regard to smartphones, we must act in a similar way. In this sense, we must focus on these sections:
- Have the latest security update from the manufacturer installed.
- Update applications from Google Play or App Store.
Thus, we can save mobile data from our data rate and go more secure. Having our devices updated means that our equipment is exposed to fewer failures and security breaches. Another very important aspect is that many devices such as smartphones, tablets and laptops allow automatic connection, this can be dangerous because these devices could connect to a public Wi-Fi network without a password automatically, and leave our data exposed. Therefore, it is highly recommended to look at this functionality of our device, and if possible, disable Wi-Fi connectivity if we are not going to use it.
Use your smartphone as if it were a WiFi router
Previously we have explained why it is not advisable to connect to a Wi-Fi network, what if we need to connect to the Internet with our laptop? The best we can do in these cases is to use the smartphone as a WiFi router when we have to send confidential information or make a payment .
If we want to configure our Android mobile as a Wi-Fi router, it is very simple. What we have to do is go to Settings . There we have to look for a section that is usually called one of the following ways: Other wireless connections, Connection and sharing or Network and internet. In the model that we have used as an example, it would be to go to Settings and then we touch on Other wireless connections .
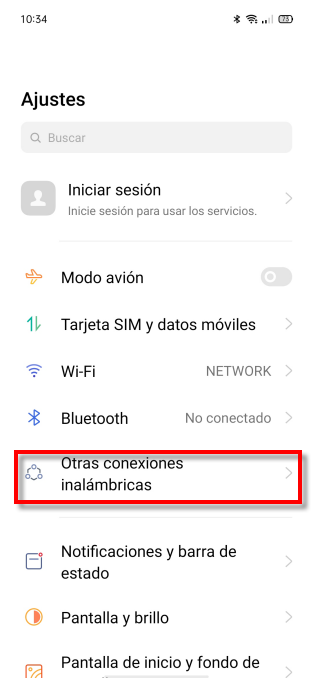
Now we must perform the following steps:
- Click on Share data over WiFi . Other commonly used alternate names are Portable Wi-Fi Hotspot, Portable Access Point, or Wi-Fi Access Point.
- Click on Settings to share data over WiFi , to start the configuration of our access point and guarantee the safety to travel. On this screen we are going to configure a series of sections to create a secure Wi-Fi access point.
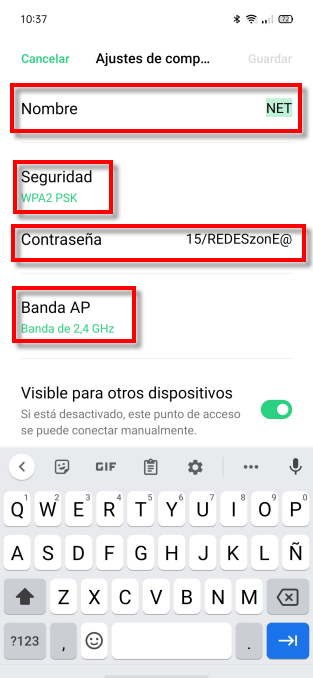
Here we have to configure the following elements:
- Name or SSID : in which we can name the Wi-Fi network so that we can distinguish it from the others.
- Security : we must ensure that it has encryption on it, the recommended minimum would be WPA2.
- Password : here we will establish a password that contains a minimum of 12 characters and that includes uppercase, lowercase and symbols such as @.
- AP band : for compatibility the best would be the 2.4 GHz band since not all devices can operate in the 5 GHz band.
With this we would have our access point ready to navigate safely through the mobile broadband network.
Use a 4G or MiFi router to surf safely
Another equivalent option would be to buy a portable WiFi router . In this sense, this option to share the Internet is as safe as the mobile one. However, it provides advantages, such as not having to depend on running out of battery on the mobile, in addition, we can also buy one with 5G connectivity, the possibility of having simultaneous dual band, a slot for micro SD cards and sharing files on the local Wi-Fi network. -Fi etc.

This option can be interesting if we travel a lot. The drawback is that we must have an independent SIM card or remove the one from our smartphone.
Disable Bluetooth, it is also an attack vector
Travel safety involves having Bluetooth turned off . More and more vulnerabilities affect this type of connection. Therefore, unless we are currently using a Bluetooth headset, or another device that requires it, it must be disabled for safety. Bluetooth has more and more security problems. By minimizing its use we prevent possible intruders from being able to exploit these security flaws. It does not matter what operating system or device we use . In that sense, it can affect both a laptop with Windows or Linux and a smartphone with Android and IOS. All of them can be vulnerable to attacks of this type and compromise our security.
Depending on the device you use, the deactivation of Bluetooth is done in one way or another, but it is really simple because we will only have to disable it, and not make any additional configuration because the only option is to be or not visible to others. Therefore, from this article we recommend that, if we are not using Bluetooth with any equipment, it must be deactivated.
Improve travel security using a VPN
If we are going to connect to public Wi-Fi networks or open networks where we do not really know who may be in them, it is convenient to use a VPN. What VPNs do is encrypt our connection . In this way, we could imagine its operation as if our data were traveling in a tunnel in which they are fully encrypted, so if they intercept our connection, they will not be able to see the data inside the VPN tunnel.

Using a VPN can be used on different operating systems like Windows, Linux, Android, and IOS. We can choose both free VPN and paid VPN. The ones with the best features and the possibility of connecting to different VPN servers are the paid ones, in addition, they are very cheap, so if you travel constantly it is highly recommended to always have one available.
Beware of public and borrowed USB chargers
It is already common to see public chargers to be able to charge our devices. In the metro of big cities, shopping centers, and even in restaurants, it is a clear example where we can find USB wall chargers to recharge our smartphone easily. This is ideal if we do not have a powerbank and we have run out of battery.

These types of public chargers can have two drawbacks. The first of them is that it may not provide us with the proper voltage, therefore, it could not charge our smartphone correctly, and even damage it. However, the most dangerous thing is that they can be manipulated to extract information from our smartphone without our knowing it, currently there are some adapters to prevent this task, blocking the USB pins that are intended for data exchange. The same could apply to loaned chargers.
Finally, travel safety requires that we take it seriously and put into practice all the tips we have mentioned. In addition, it requires that we keep our equipment safely and always in sight to avoid being the subject of theft .