pfSense is one of the most comprehensive router and firewall oriented operating systems out there today. Thanks to the large number of advanced configuration options, pfSense is suitable for use both at an advanced home level, as well as in small and medium-sized companies. Today in this article we are going to explain how to configure access to pfSense via the web using the secure HTTPS protocol, and also how to configure the SSH server with the best possible security, so that the authentication in the operating system is carried out in an encrypted and secure way .
The two main accesses that we have to the administration of the pfSense operating system are via the web and via SSH. In the first case, pfSense is configured by default to use the HTTP protocol on port 80, a protocol that is not secure because the authentication and data exchange is done without encryption, therefore, it is a mandatory requirement to configure the HTTPS protocol. to have the maximum possible security. The same happens with the SSH server incorporated in the operating system, it is advisable to make some changes in the configuration to have the best possible security, because via SSH we can configure any internal aspect of the operating system, and we must protect these two accesses against external intrusions .

Web management configuration with HTTPS
To configure the HTTPS protocol, we must go to the ” System / Advanced ” menu, and in this menu we will see the “Admin Access”. We can choose between the HTTP and HTTPS protocol, it is advisable to always use the HTTPS protocol to ensure our communications and also their integrity. When we activate the HTTPS protocol, we must choose an SSL / TLS certificate, which is already created by default with the operating system, however, we can create a new one without problems and even renew it.
In this menu we can also choose the TCP port to use, if we do not put anything, the default port of the HTTPS protocol is always 443. We can also choose the maximum number of concurrent users managing pfSense, by default it is 2 but we can upload it if we have various administrators. The rest of the configuration options must be with the values that we put below, all of them are the default parameters and they are perfectly.
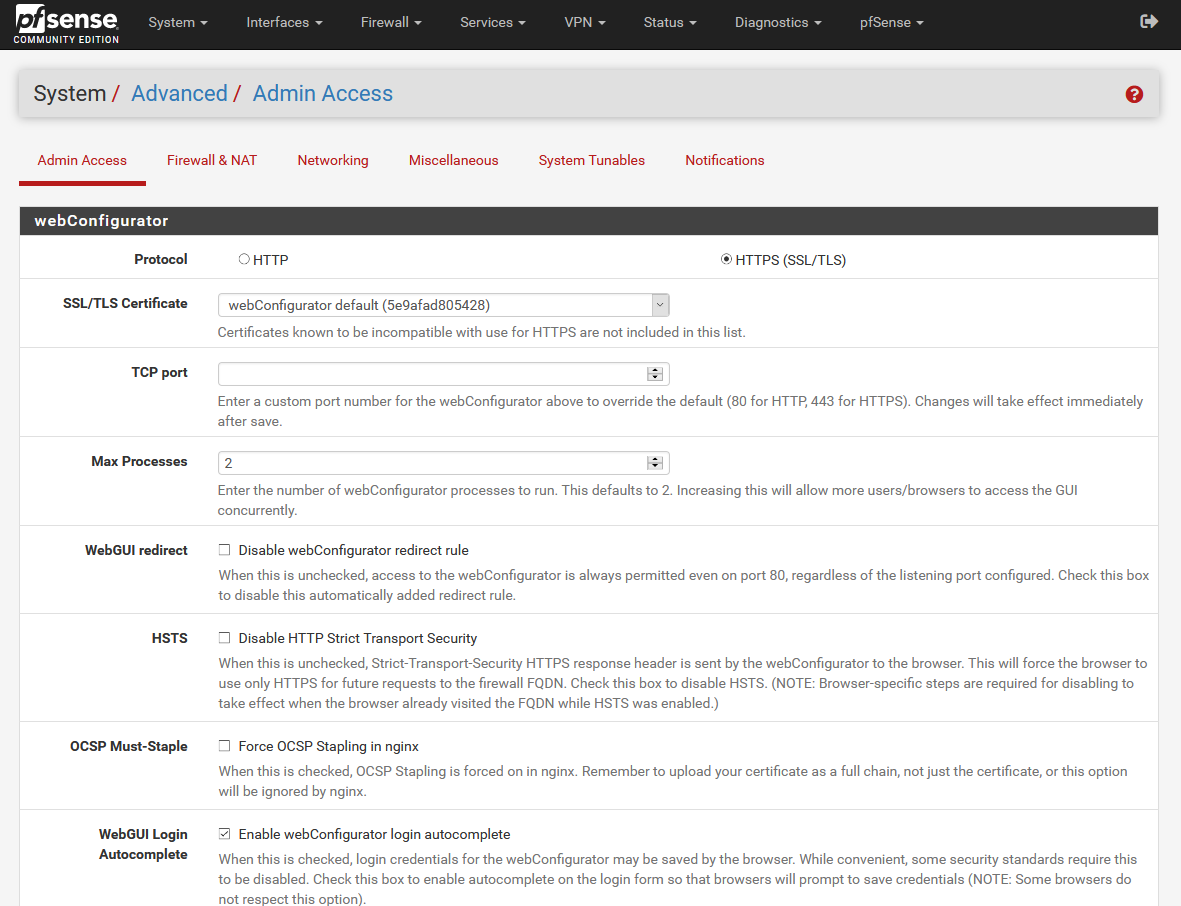
In the ” System / Certificate Manager ” section is where we can see the SSL / TLS certificate used by the HTTPS web server, we can renew it at any time, delete it, export the public key and also the private one. In principle, we should not touch this, but if we do, we can renew it or edit the name of the certificate itself.
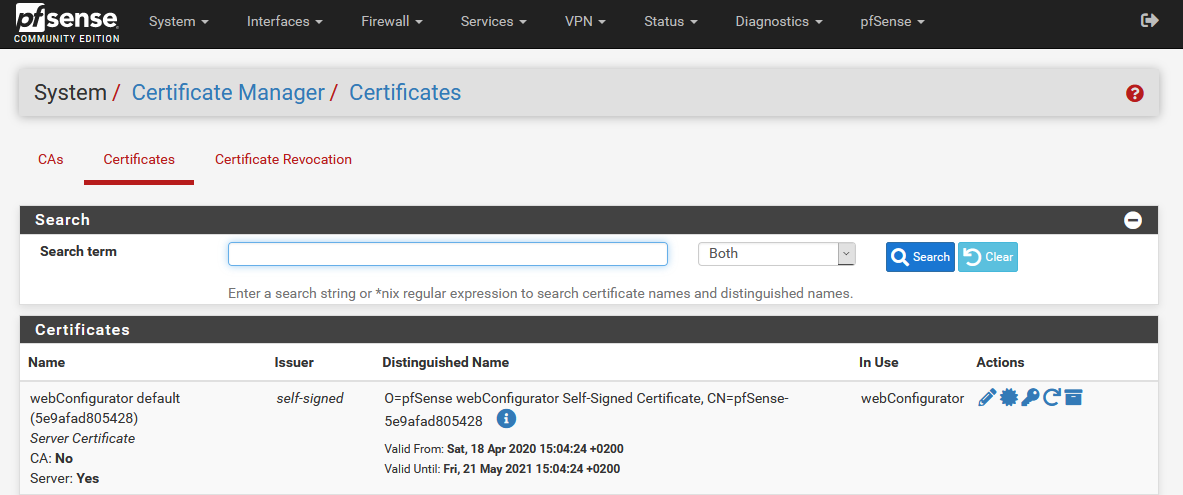
If we enter “Page information” with any browser, we can see that the connection is encrypted with TLS 1.3, the latest available protocol that gives us the best security and performance in secure connections.
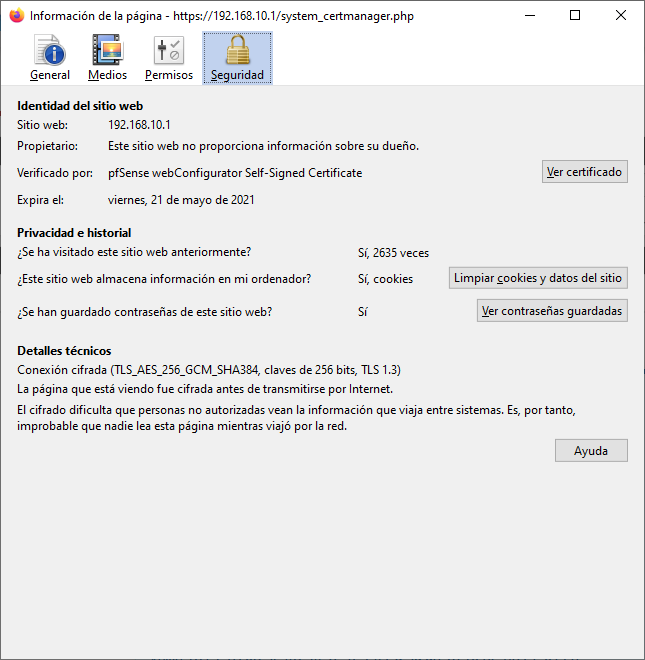
Regarding the certificate data, pfSense creates a 2048-bit RSA-based certificate, which is typical in these cases where we have a web server with HTTPS. If we want to change this security, we must create a CA (Certification Authority) and later a server certificate that hangs from said CA, in this way, we can make use of longer RSA and even elliptical curves (ECDSA), finally , we can configure the hash algorithm to use.
In the case of renewing the digital certificate corresponding to the web server, we simply have to go to the “System / Certificate Manager” section, click on renew the webconfigurator certificate and click on the “Renew or Reissue” button to generate it again.
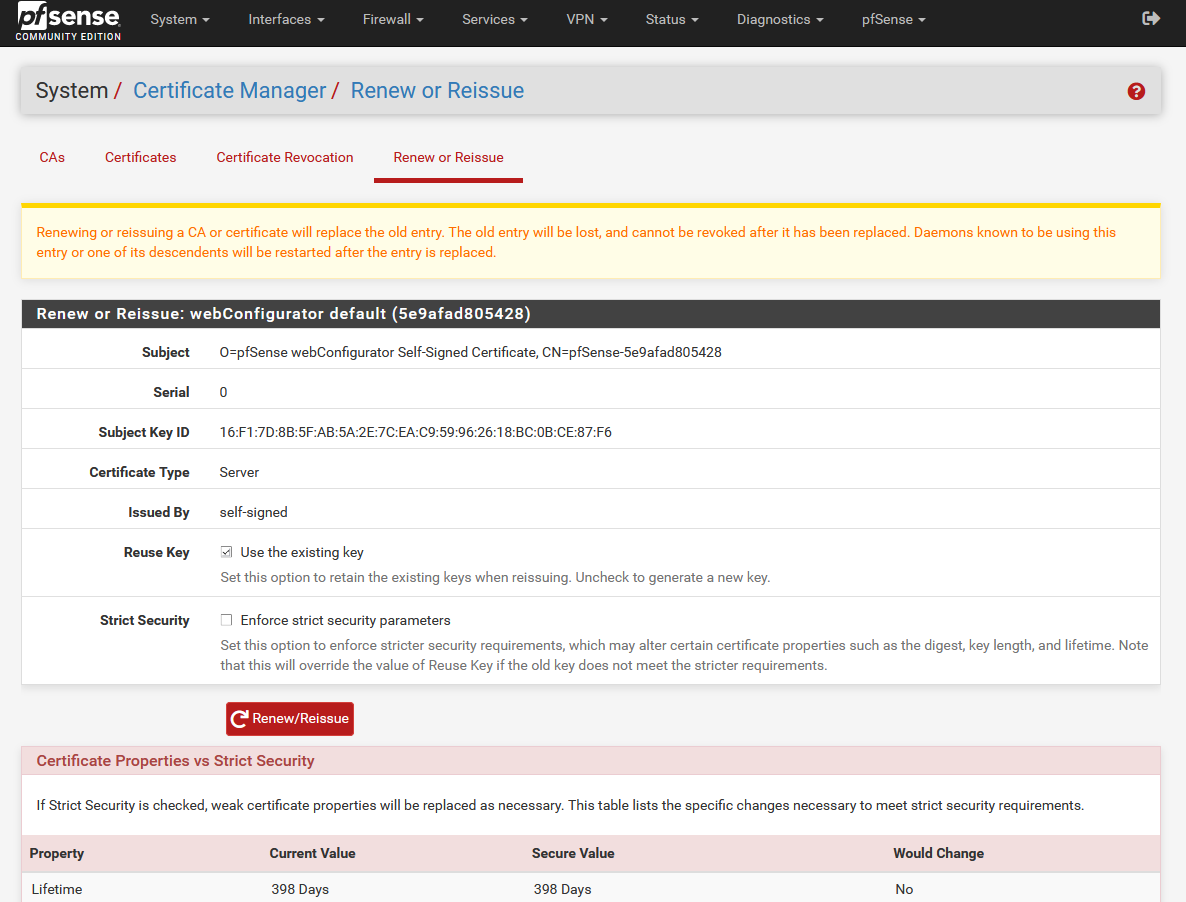
As you have seen, configuring HTTPS is really easy and simple, this will allow us to authenticate via the web safely.
Administration configuration via console with SSH
The secure SSH protocol will allow us to remotely enter the administration of the pfSense operating system via the console. We will have different types of authentication:
- SSH public key
- Password or public key (one or the other)
- Password and public key (both)
We will also have the possibility to enable forwarding on the SSH server, to perform SSH Tunneling, for example. Finally, we can modify the listening port of the SSH server, in the case of this protocol it is TCP 22, but we can change it, in fact, for security reasons it is advisable to change the default port of the SSH server.
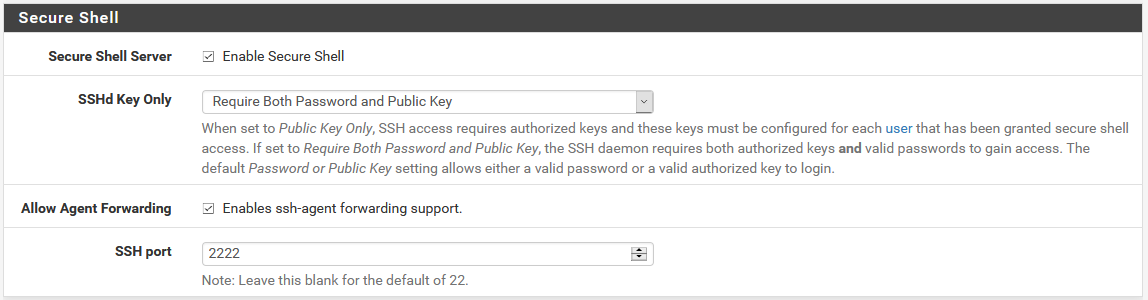
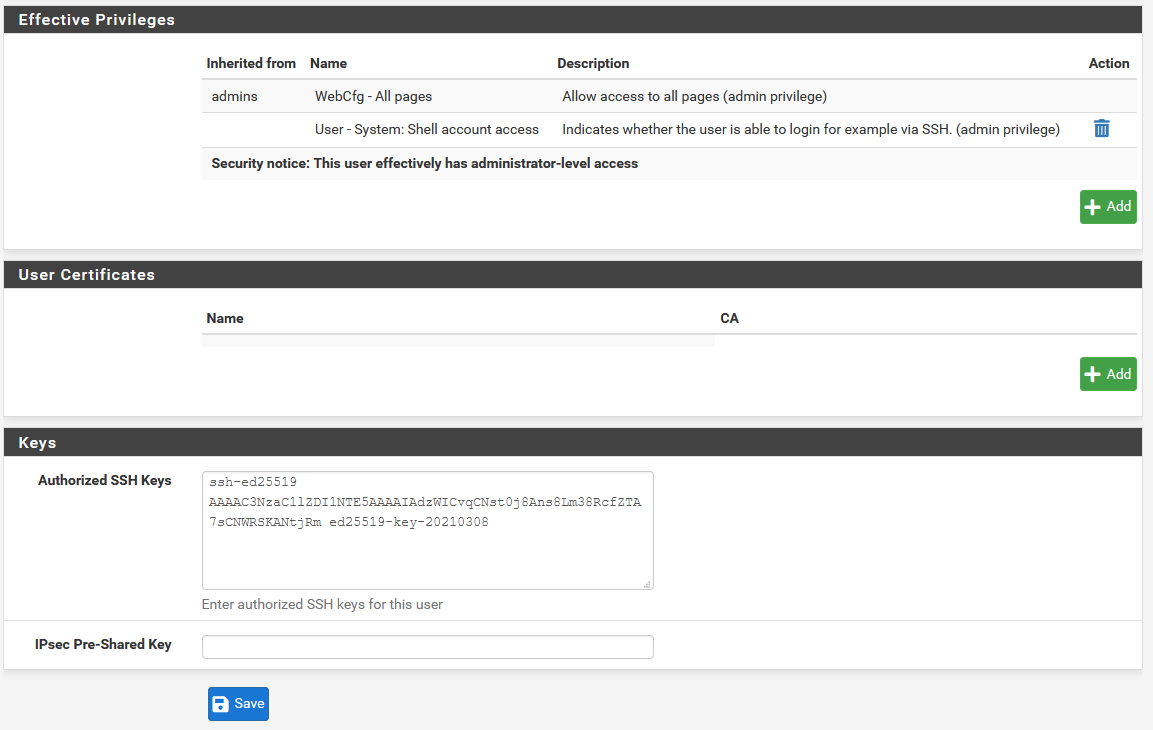
Once we have configured the authentication, we will have to configure the users that can authenticate in the SSH server, and also what SSH keys said users have. If we click on the hyperlink where it says “user” it will take us directly to “System / User Manager”, and here we can add a new user with different permissions. In our case, we have added a new user that belongs to the “admins” group.
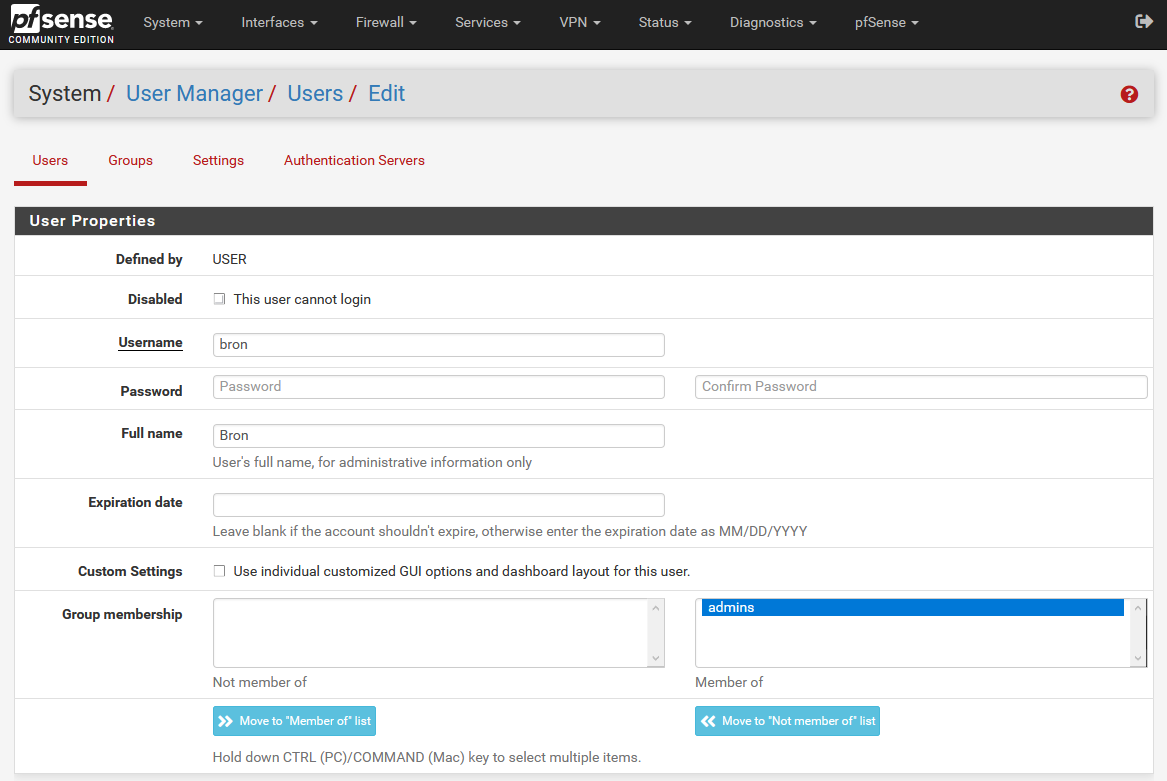
If we create a new user or edit it, we can configure different parameters. In our case, we have added it to the admins group, as you can see in the following image:
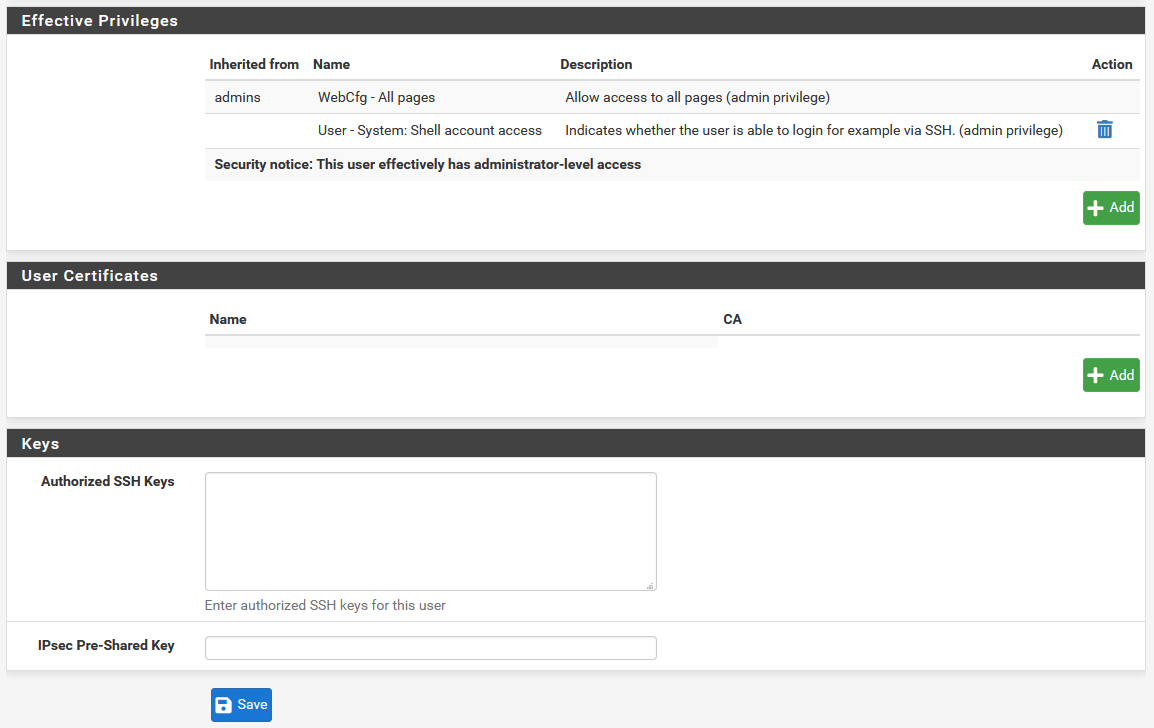
To be able to log in to pfSense via SSH, we must give it the corresponding permission in the “Effective Privileges” section, of all the list of permissions that a user can have, it must have the following:
- User – System: shell account access
Once you have this permission, we can log into the operating system with your username. Depending on what we have chosen when authenticating the user, we will have to perform an additional action:
- SSH public key: we must create it
- Password or public key (one or the other): we can use the configured key, or the SSH public key if we create it.
- Password and public key (both): we will use the configured key plus the SSH public key, it is necessary to create it.
As the safest thing for authentication is “SSH public key” or “Password and public key (both)”, we must create SSH keys.
Create SSH keys with Puttygen
We are currently using a Windows 10 operating system, the easiest way to create SSH keys is to use the ” Putty Key Generator ” program that you can download for free. No installation is necessary, when downloading the program we will execute it and we will see the following menu:
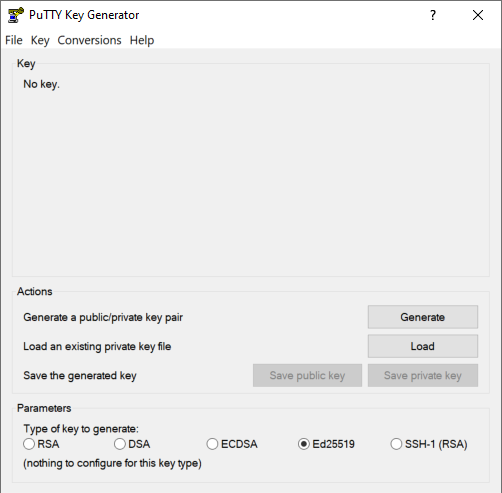
Here we can configure different types of SSH keys, RSA and DSA are the most common and well-known, but it is advisable to use keys such as ECDSA and also Ed25519 that use elliptical curves. In our case, we have used Ed25519, select it and click on «Generate».
Once we click on generate, we must move the mouse to create randomness and that the keys are generated correctly. Now we can see at the top the public key that we must paste in the pfSense user created previously. We can configure a comment in the key, and also a password to decrypt the private key when connecting, this increases security. If someone is able to steal our private key, they will not be able to use it unless they have the passkey of the generated private key.
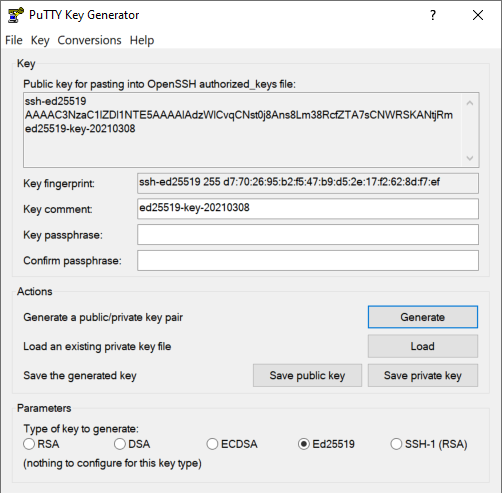
Once we have the generated key, we click on “Save public key” and also on “Save private Key” to have the pair of keys always at hand. We must remember that the public key is the one that we must copy to the user, as you can see:
Once the SSH server is completely configured in pfSense, we are going to show you how to connect with the popular Putty program.
Connect to pfSense with Putty and SSH key
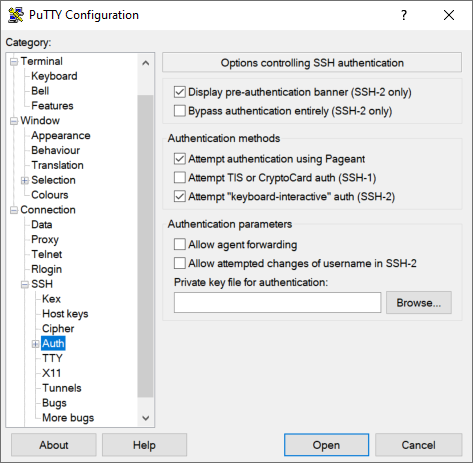
We open the Putty program and go to the “Connection / SSH / Auth” section and go to the “Private key file for authentication” section, and click on “Browse” to load the private key that we have previously saved.
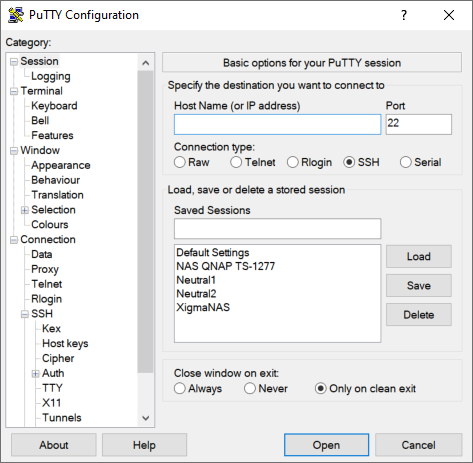
Now we go to the “Session” section, we put the IP address and the port of the SSH server in pfSense, once filled in, we click on “Open”.
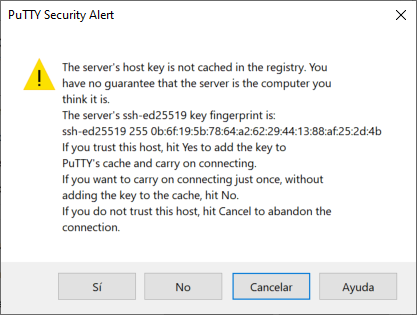
Now it will tell us that the connection is not cached, so it is the first time we connect. We must click on “Yes” to connect.
It will ask us for the username of the login, we put the username associated with this SSH key created:
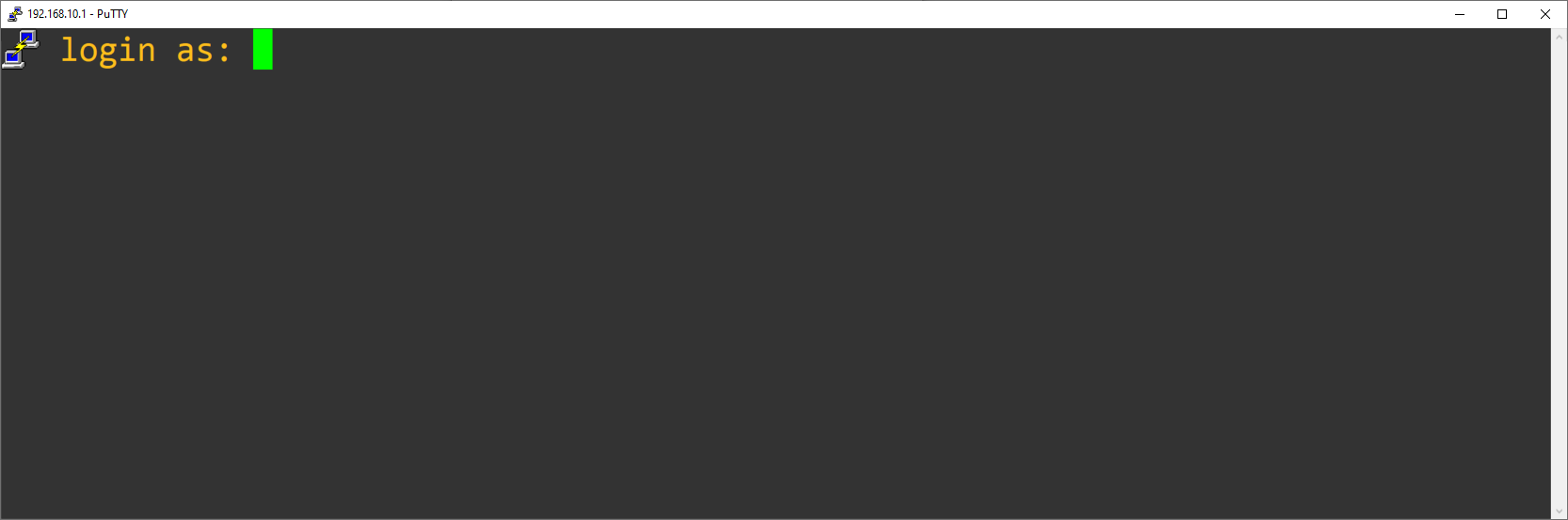
And as soon as we enter the username, it will indicate that the authentication is correct and we will be able to start executing commands via SSH in the pfSense operating system. In this example we have only used public key, we have not used the combination of password and SSH public key, but you can also use it without problems, the only thing that will ask us for the password when connecting.
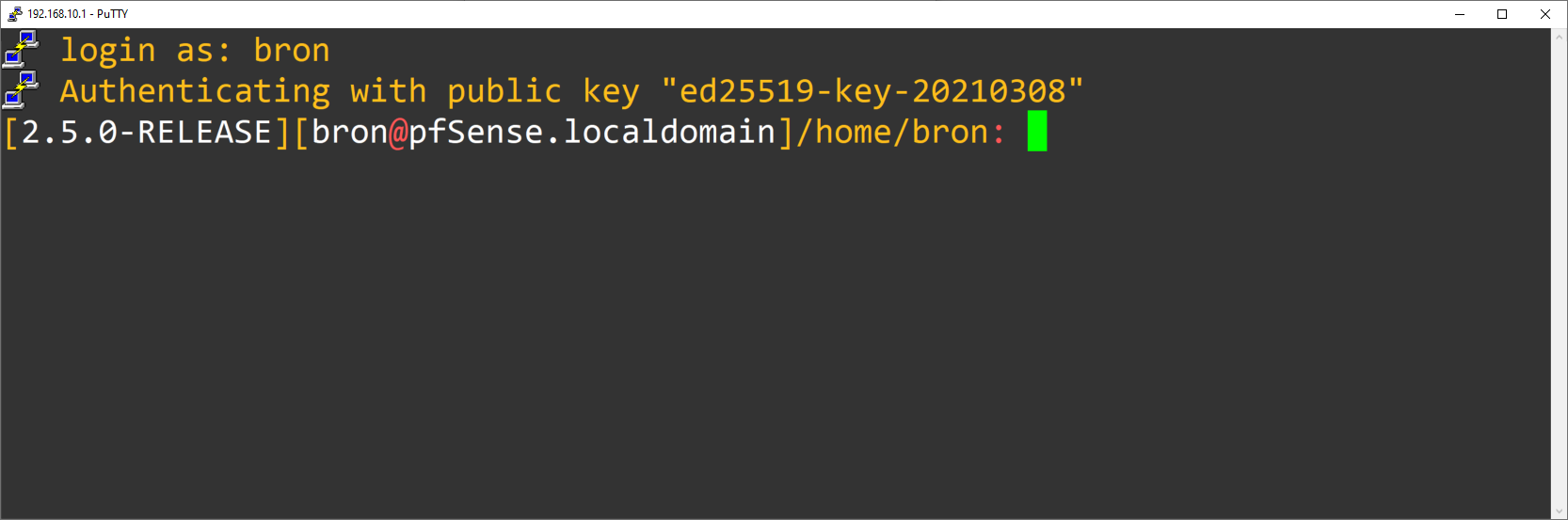
Now that we have the SSH server correctly configured, we are going to see some additional configurations.
Login protection and console management options
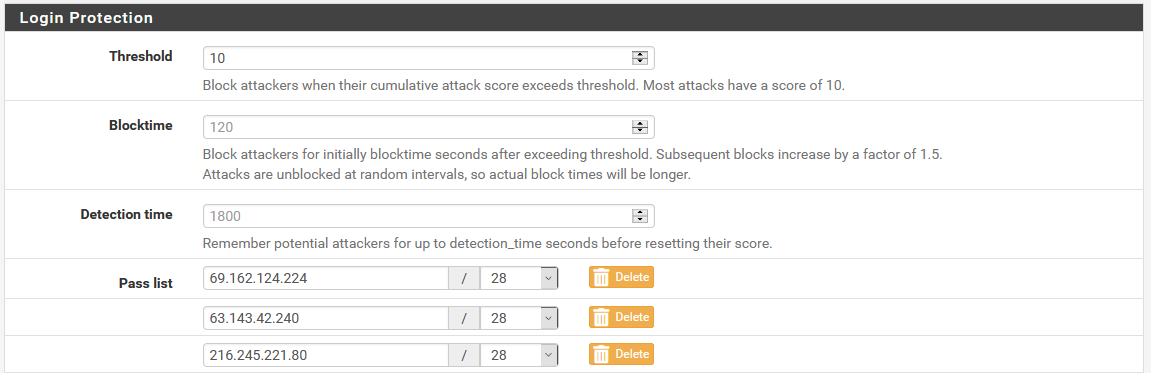
In the ” System / Advanced ” section we can configure the protection of the login, in principle, the configuration that comes by default is very good to block attackers who continuously try to connect to the SSH server. If we exceed the value of 10 in a time of 1800 seconds, access attempts will be blocked for 120 seconds.
At the bottom where we have the «Pass list» we can put public IP addresses that we do allow to pass these protections, this is necessary for services like UptimeRobot that every so often is trying to verify that the SSH or web server is up.
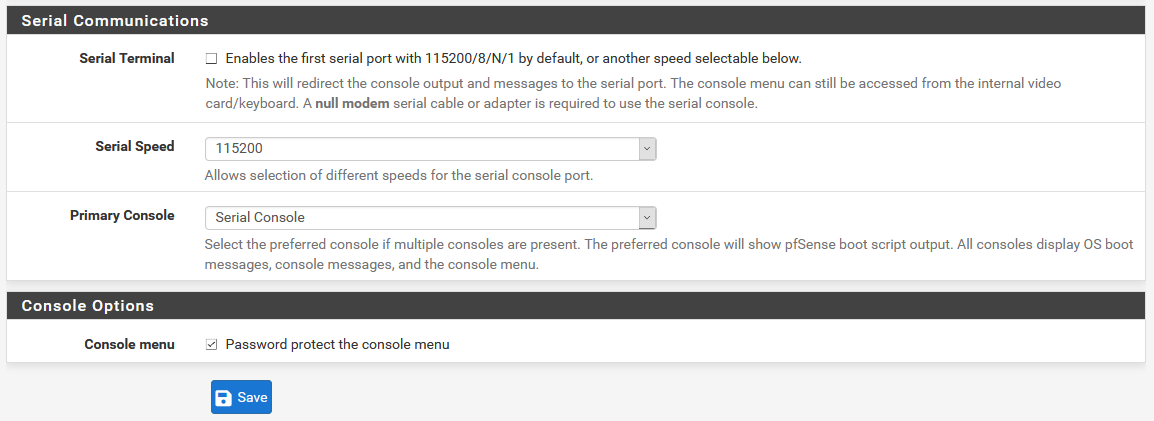
Other configurations that we should make is the “Console menu” section, it is advisable to protect it through an access password. Not only will we need to have physical access to the pfSense team, but it will also ask for password authentication for root.
Before we finish, we would like to discuss additional protective measures.
Rules on the firewall and use IDS / IPS
pfSense is a really powerful and advanced firewall-oriented operating system, thanks to the different rules that we can configure in the different interfaces, we will have the possibility to allow or deny access to both the web server and the SSH server. A good security practice is not to allow access via web or SSH over the Internet, if we need to manage pfSense remotely, a good practice is to connect via VPN to one of the multiple VPN servers that pfSense allows (OpenVPN, WireGuard, IPsec …), and later enter via web or SSH, but not expose both services to the Internet, even if we have protected them correctly.
In the event that you have no choice but to expose both services (for some reason), our recommendation is that you install and configure an intrusion detection and prevention system, such as Snort or Suricata. In this way, you will have more control over the connections that are made, and automatically block possible brute force attacks, denial of service, etc.
The same happens if we want to allow or deny access in the different VLANs that we can create, the most normal thing is that a network defined as “Guests” never has access to the pfSense administration panel, either via web or SSH. This must be done through the “Firewall / Rules” section, setting rules for addresses or networks of origin and destination of pfSense itself, as is usually done.
We hope that with these recommendations you will be able to correctly protect both web and SSH access to pfSense.