In a security investigation, it has been discovered that confidential data can be extracted from computers via Wi-Fi. The attack has been dubbed AIR-FI. Thanks to this new technique, Wi-Fi signals are exploited as a covert channel, and surprisingly does not require the presence of Wi-Fi hardware in the target systems. Today in this article we are going to explain in detail how this interesting attack works that could jeopardize many confidential computer data.
How the AIR-FI attack works
The AIR-FI attack is based on the implementation of specially designed malware that exploits DDR SDRAM buses to generate electromagnetic emissions on the 2.4 GHz Wi-Fi bands. It then transmits information on these frequencies that can later be intercepted and decoded by nearby Wi-Fi capable devices. Some examples of computers that we could use to send data to remote servers controlled by an attacker are:
- Smartphones.
- Laptops,
- IoT devices.
The research results were published in an article by Dr. Mordechai Guri who is head of R&D at the Cyber Security Research Center at Israel’s Ben-Gurion University of the Negev. This AIR-FI attack is characterized by the fact that it does not require Wi-Fi related hardware on computers. The attacker is going to exploit the DDR SDRAM buses to generate electromagnetic emissions in the 2.4 GHz Wi-Fi bands and encode binary data on top. We can define “air gap” equipment as machines without network interfaces. In maximum security environments, they can be made a priority to keep confidential data safe and thus reduce the risk of data leakage.
It is not always possible to use AIR-FI
If we want to carry out such an attack, it is often paramount that the transmitting and receiving machines are physically located close to each other. Furthermore, they are also required to be infected with the appropriate malware to establish the communication link. AIR-FI does not depend on a Wi-Fi transmitter and does not require kernel drivers, root or access to hardware resources to transmit data.
The covert channel can be used even from within an isolated virtual machine, and it has an endless list of Wi-Fi-enabled devices that can be hacked to act as a receiver. On a computer that implements malware through social engineering, it is enough to carry out this attack, some examples that could be used are:
- Self-propagating worms like Agent.BTZ.
- A tampered USB flash drive.
- Malicious insiders.
In addition, we must infect Wi-Fi capable devices located on the air gap network, compromising the firmware of the Wi-Fi chips , installing the malware capable of detecting and decoding the transmission, to finally exfiltrate the data through Internet.
The exploitation of DDR SDRAM buses
Malware on the target system collects the relevant data like confidential documents, credentials or encryption keys. They are then encoded and transmitted on the 2.4 GHz Wi-Fi band. Thus, using the electromagnetic emissions generated by the DDR SDRAM buses, data was often exchanged between the CPU and memory.
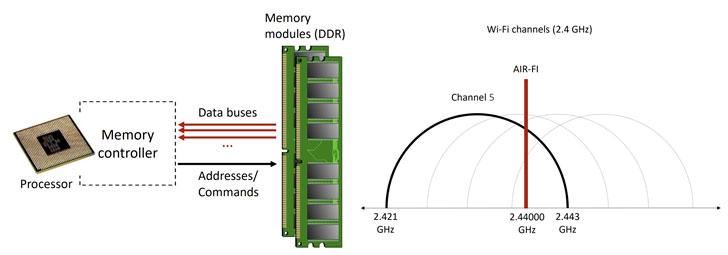
Its operation is based on the generation of Wi-Fi signals, in which the attack makes use of the data bus to emit electromagnetic radiation at a frequency correlated with the DDR memory module and read or write operations. This research is one more reminder that electromagnetic, acoustic, thermal and optical components can be used to perform refined exfiltration attacks against air gap equipment.
Dr. Guri to solve the problem, proposes zone protections to protect against electromagnetic attacks. Thus, we must allow intrusion detection systems to monitor and inspect processes that perform intensive memory transfer operations and use Faraday shields to block the covert channel. The AIR-FI malware has shown us how with this attack data can be stolen from computers with air gap to a nearby Wi-Fi receiver through Wi-Fi signals.