In these times, keeping our information secure is vital. For this reason, even users themselves are beginning to realize that an encryption system for their documents is the most optimal option, which prevents problems even if your PC has been hacked. In this sense, there is an encryption system that could be considered the most used by companies and governments and that will allow us to be safe: AES-256 bits.
Contrary to what you might believe, the best encryptions do not come from private companies like Google or anyone who is dedicated to crypto. Most come from governments, usually the US government, as it is the main driver of tools to protect its federal agencies like the NSA . What if they weren’t going to keep the confidential information secret?

This is no different for the well-known AES, since it was adopted by the federal government and as it was with the Internet at the time, it is currently an industry standard that keeps our data safe.
AES encryption, its types and Moore’s Law

There are currently three types of AES encryption: 128-bit, 192-bit, and 256-bit, where the latter is the most secure. This was designed based on Moore’s Law , as the first tests showed that, in a relatively short time, the power of the processors could break the weakest encryption in shorter and shorter periods of time.
So although it started with 56 bits, it was quickly switched to the three named types to make it more secure. Advanced Encryption Standard or AES has a fairly clear advantage over other competitors: it has an open nature, which means that it can be used both publicly and privately, whether for commercial purposes or not.
In addition, it is a symmetric key system, which gives it greater security, since the used key must be known for encryption and decryption and both sender and receiver need a copy of the corresponding key. This has an important advantage in the performance of an encryption system, since since the sender and recipient are forced to know the key, less computing power is required to travel the information since it is always secure.
How this sophisticated encryption works
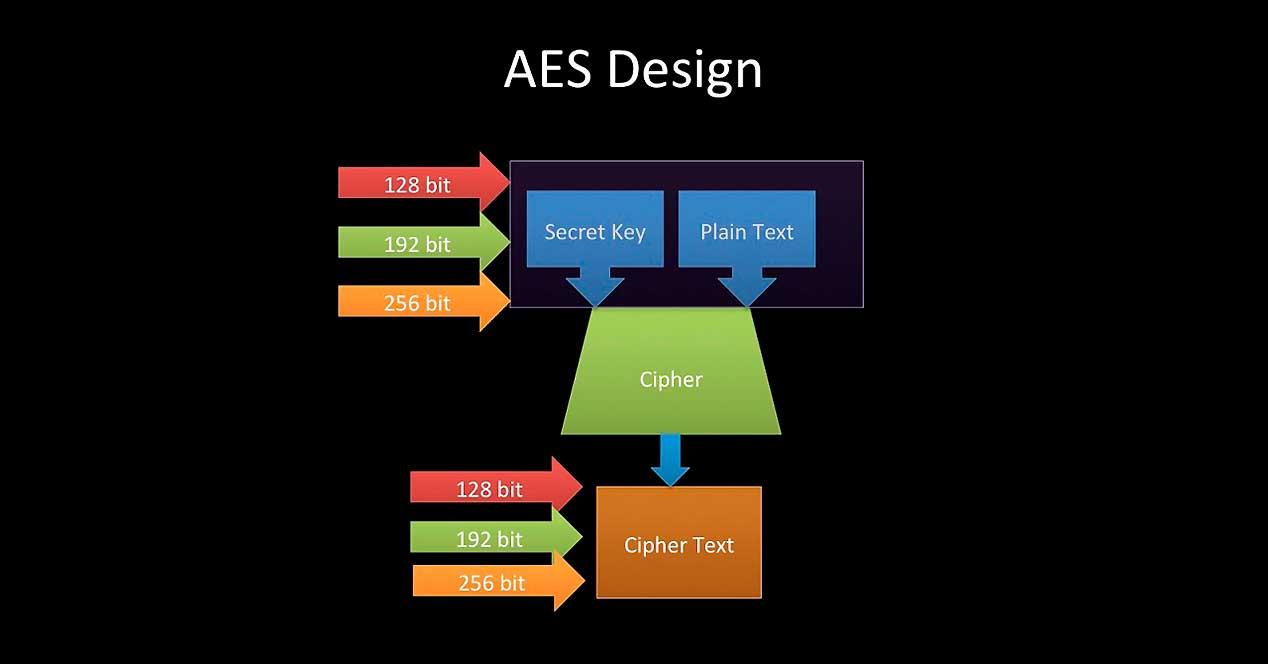
Everything is based on blocks, specifically 128-bit blocks which are divided into a four-by-four matrix with 16 bytes. Eight bits per byte give us the 128 bits mentioned and for this reason when encrypting the information its size is not altered thanks to the matrices. AES is a substitution and permutation system, making it highly secure thanks to the fact that the initial key serves to generate new keys.
Each byte of data is replaced by another by means of a predetermined table to then take each 4 × 4 matrix and move it as follows: the bytes in the second row move one space to the left, the bytes in the third row move two spaces and the fourth bytes move three to finally mix the columns and add the initial key to the set and start again.
This generates an encrypted text that has nothing to do with the original and that to decrypt it requires the reverse steps to be carried out, previously knowing the key. Among the three types of AES encryption, the only difference is precisely the length of the key, so if we compare 128 bits with 256 bits, we will have a key twice as long in the latter.
Finally, we are left to wonder if AES-256 bits is as secure as they paint it. The answer is yes, but it has its nuances, since we not only have the encryption itself, but the structure that houses it to receive or send the information.
The 256-bit encryption as far as we know is still impregnable and although there have been attempts with AES-128 bits, trying to break a 256-bit key requires 2128 times more computing power by brute force and even with such computing power and with current hardware, the time to decipher a single key would be more than twice the total age of the universe , so we can rest easy.