A new batch of malicious Android apps posing as file managers have managed to infiltrate the Play Store app store, infecting many users with the Sharkbot banking Trojan.
To avoid detection and thus be able to appear in the Android app store, they do not carry a malicious payload at installation time, but retrieve it later using a remote resource. Although right now they have already been discovered and are not in the app store, you could have installed one on your mobile, so it is important that you check that you do not have it. In addition, they are still in third-party stores.

Sharkbot is back on the attack
Sharkbot is dangerous malware that tries to steal online bank accounts by displaying fake login forms. If you try to log into your bank using one of these forms, they steal your bank details and use them to get your money or whatever they want.
Because malicious apps masquerade as file managers, they don’t raise as much suspicion when asking for dangerous permissions as they do to load the well-known Sharkbot malware. That is where all the deception comes from, because once the app is installed and the permissions are accepted, the victims have been infected with this virus.
This virus has evolved considerably over time and has managed to appear in various guises or from various infected apps , such as posing as fake antivirus or cleaning tools to inspire more confidence in potential victims. It has returned in the form of new apps, and we tell you what they are.
Beware of these 4 file management apps
In the new Bitdefender report, these new apps were discovered in the form of file managers and finally Google has removed them from the app store. In any case, the people who have installed them could still have them on their mobile, so check that you do not have one, uninstall it and take care of your bank account.
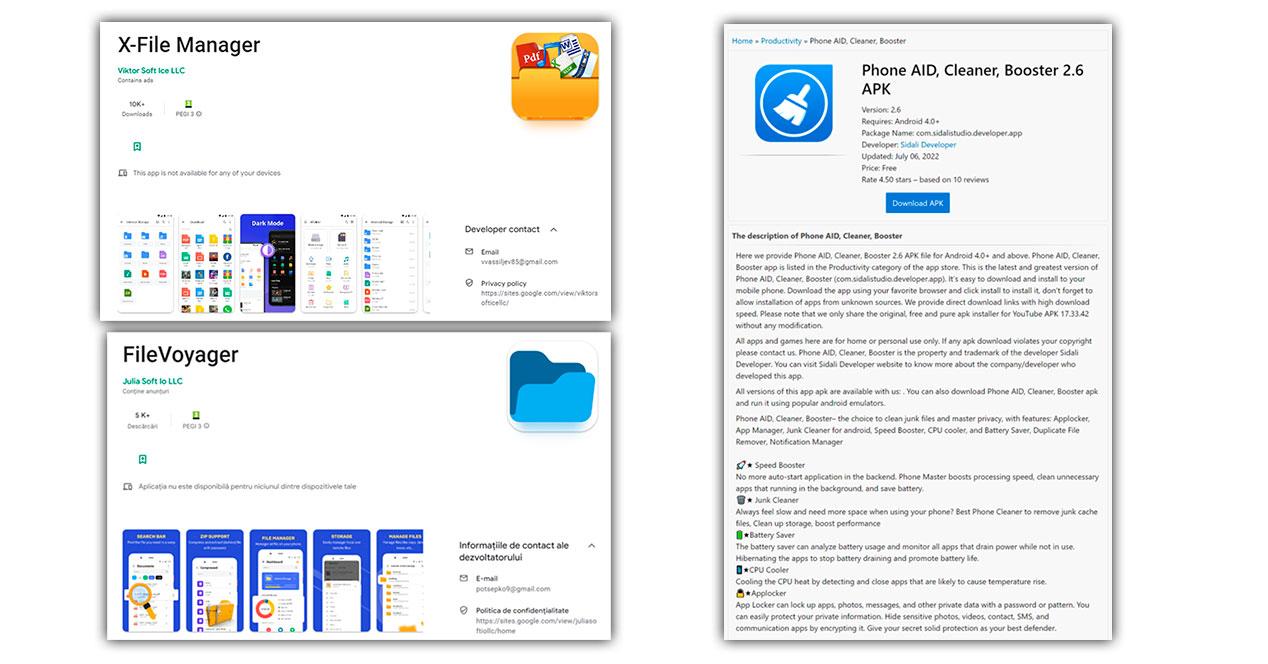
One of these malicious apps is X-File Manager , by Victor Soft Ice LLC (com.victorsoftice.llc), which has been downloaded 10,000 times on the Play Store app store. This one also has a lot of negative reviews. Another malicious app downloaded more than 5,000 times is FileVoyager from Julia Soft Io LLC (com.potsepko9.FileManagerApp).
With more than 1,000 downloads is LiteCleaner M’ (com.ltdevelopergroups.litecleaner.m), now only available in third-party app stores like APKSOS; in which there is also Phone AID, Cleaner, Booster 2.6′ (com.sidalistudio.developer.app).
Like the others, any of them run anti-emulation checks to evade detection and will only load the malware on British or Italian SIM cards, for now, as part of a targeted campaign. In principle, most of its victims are in the United Kingdom, Italy, Iran and Germany.
Once it is installed, it requests that you accept risky permissions such as installing new packages, reading and writing to internal storage, accessing account details, etc., which, although they would be normal in this type of app, are very dangerous because they are not actually legitimate applications. The point at which Sharbot malware is obtained is through a fake update that users agree to.
Remember, these are:
- X File Manager
- FileVoyager
- LiteCleaner M’
- Phone AID Cleaner Booster 2.6′
If you have installed this app or any other of the type that is infected, it is important that you remove it as soon as possible and change the passwords of your online bank account to prevent them from accessing and using it. Remember to enable Play Protect if you haven’t already done so and it doesn’t hurt to try an antivirus.
What mobile banking apps is the attack targeting?
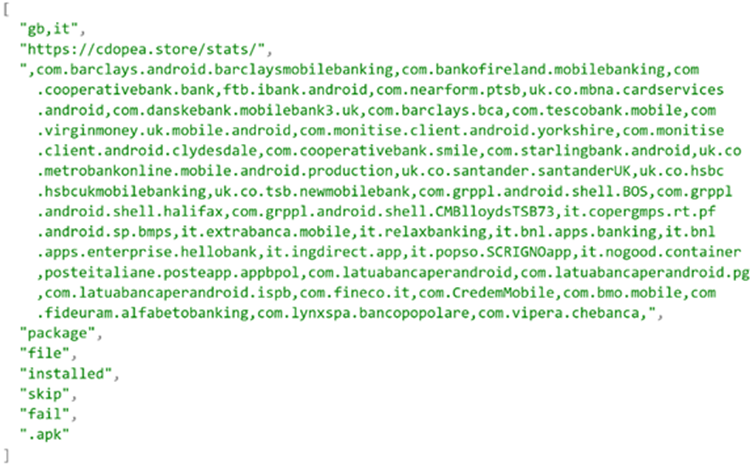
Note that although several mobile banking apps targeted by malware have been detected, the list can be updated with new apps. The ones that are known at the moment are these:
| package name | Banking entity |
| com.barclays.android.barclaysmobilebanking | barclays |
| com.bankofireland.mobilebanking | Bank of Ireland Mobile Banking |
| com.cooperativebank.bank | The Cooperative Bank |
| ftb.ibank.android | AIB (NI) Mobile |
| com.nearform.ptsb | permanent tsb |
| uk.co.mbna.cardservices.android | MBNA Mobile App |
| com.danskebank.mobilebank3.uk | Mobile Bank UK – Danske Bank |
| com.barclays.bca | barclaycard |
| com.tescobank.mobile | Tesco Bank and Clubcard Pay+ |
| com.virginmoney.uk.mobile.android | Virgin Money Mobile Banking |
| com.cooperativebank.smile | “smile – the internet bank” |
| com.starlingbank.android | Starling Bank – Mobile Banking |
| uk.co.metrobankonline.mobile.android.production | Subway Bank |
| uk.co.santander.santanderUK | Santander Mobile Banking |
| uk.co.hsbc.hsbcukmobilebanking | HSBC UK Mobile Banking |
| uk.co.tsb.newmobilebank | TSB Mobile Banking |
| com.grppl.android.shell.BOS | Bank of Scotland Mobile App |
| com.grppl.android.shell.halifax | Halifax Mobile Banking |
| com.grppl.android.shell.CMBlloydsTSB73 | Lloyds Bank Mobile Banking |
| it.copergmps.rt.pf.android.sp.bmps | MPS Bank |
| it.extrabanca.mobile | NewExtraMobileBank |
| it.relaxbanking | RelaxBanking Mobile |
| it.bnl.apps.banking | BNL |
| it.bnl.apps.enterprise.hellobank | Hello Bank! |
| it.ingdirect.app | ING Italy |
| it.popso.SCRIGNOapp | SCRIGNOapp |
| posteitaliane.posteapp.appbpol | Post Bank |
| com.latuabancaperandroid | Intesa Sanpaolo Mobile |
| com.latuabancaperandroid.pg | Intesa Sanpaolo Business |
| com.latuabancaperandroid.ispb | Intesa Sanpaolo Private |
| com.fineco.it | fineco |
| com.CredemMobile | believe us |
| com.bmo.mobile | BMO Mobile Banking |
| com.fideuram.alphabetobanking | Banking Alphabet |
| com.lynxspa.bancopopolare | YouApp – Mobile Banking |
| com.vipera.chebanca | CheBanca! |
Although it is a localized attack, for the moment, all precaution is little. Be careful what you install!